Hi,
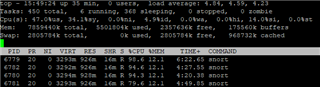
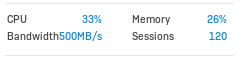
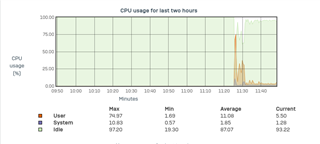
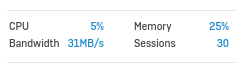
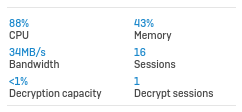
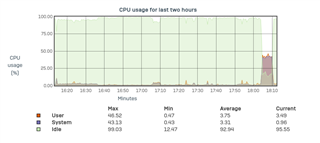
I upgraded from v17.5.8 to v18 EAP about a week ago and noticed a drop in performance and an increased RAM usage.
I do have a XG115 rev2 Appliance installed with the Software Image and a Home Use License.
My Internet connection is 100/40.
With version 17.5.8 I was able to reach about 80 to 90 Mbit download (I already expected more from the hardware)
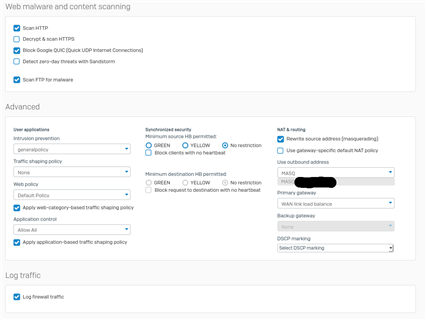
After the Upgrade I only reach about 50 to 60 Mbit download. There is no DPI or webfiltering activated and it doesn't matter if i activate IPS or not.
SSL/TLS Inspection is turned on but there are not any rules.
Are there any tweaking options for the software version of Sophos XG running on a HW Appliance?
Thank you!