Hi,
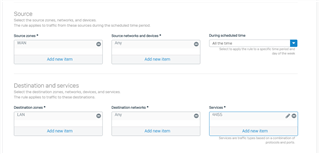
We are testing V18 in my LAB and I am confused with Firewall rule and Destination NAT policy. My configuration as like:
In the Firewall Rule, Why I need Destination HOST as "ANY". If I will choose a host IP in destination Host as my SSH server then this rule is not working. Is it a bug or some specific reason for the required "ANY" in the Destination HOST field?