Hi guys,
Been messing with the new version and Im not sure how to publish services to internet (Outgoing NATs are working fine)
What's the way to do it? What takes effect first?
Scenario (demo):
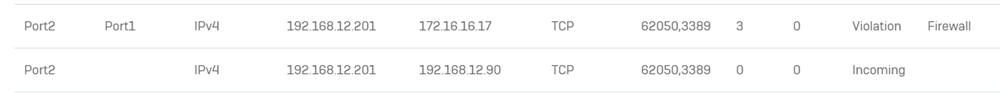
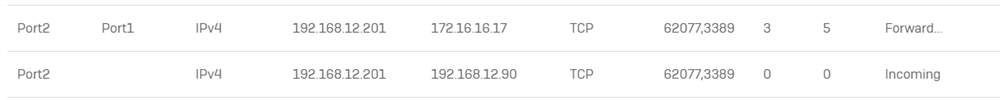
WAN (Port2):
192.168.12.90
LAN (Port1)
172.16.16.0/24 (.16 gateway / XG)
Host:
172.16.16.17
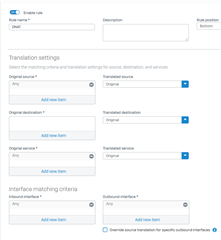
Im publishing any port (lets take for the sake of this example the safest port: 3389). How should I create the rules for this scenario?
Thanks in advance!!! Antonio.
[locked by: Stuart Hatto at 11:24 AM (GMT -7) on 15 Oct 2019]
[unlocked by: Stuart Hatto at 9:10 AM (GMT -7) on 16 Oct 2019]