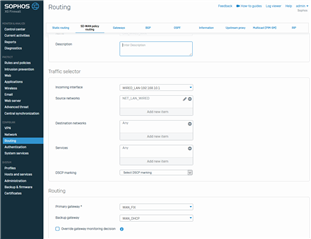
My ISP provides only dynamic IP.
After upgrading to v18, SNAT will only work with IPs assigned to the last-numbered WAN interface. All other interfaces does not work with SNAT.
outbound of the each interface is green
If you want see the device directly, Sophos access ID is here: 3445a410-a079-3f93-b6ef-75a9aba0ffeb@eu2.apu.sophos.com