Hi guys,
there was a little conversation about the migration of NAT in V18.
Just a little information / explanation, how i interact with the V18 Migration.
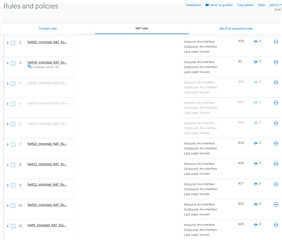
If you migrate to V18, the MASQ Rules in the firewall policies are gone. Those rules are getting migrated to Linked NAT rules, which are basically doing the same.
But you will get some of those rules.
for example:
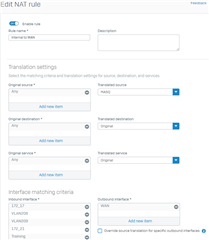
You can actually replace those rules with a new SNAT Rule.
This new rule has to match on your internal interface and your external interface.
For example:
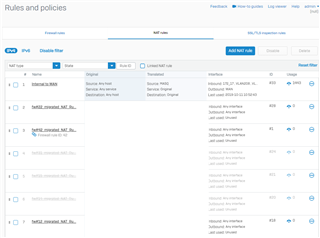
This will actually match, if you put it on top of your rule set.
My Suggestion would be: Place a top rule like that on your rule set and reset the counter of all other rules below.
So you can actually verify, that your new SNAT Rule is matching against everything.
All Linked NAT Rules should have a usage of 0.
If that is the case for a longer period, start to delete those Linked NAT rules.
The new Rule set should be clean.