Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your
Table of Contents
Overview
This Recommended Read describes using the SD-WAN route to perform failover on site-to-site RED tunnels.
The SD-WAN route is usually used in WAN gateways as a means of Active - Standby in case the primary WAN port fails. The same method can be used in RED Site-to-Site VPNs if each tunnel uses a different WAN port.
This applies to the following Sophos products and versions:
- Sophos Firewall
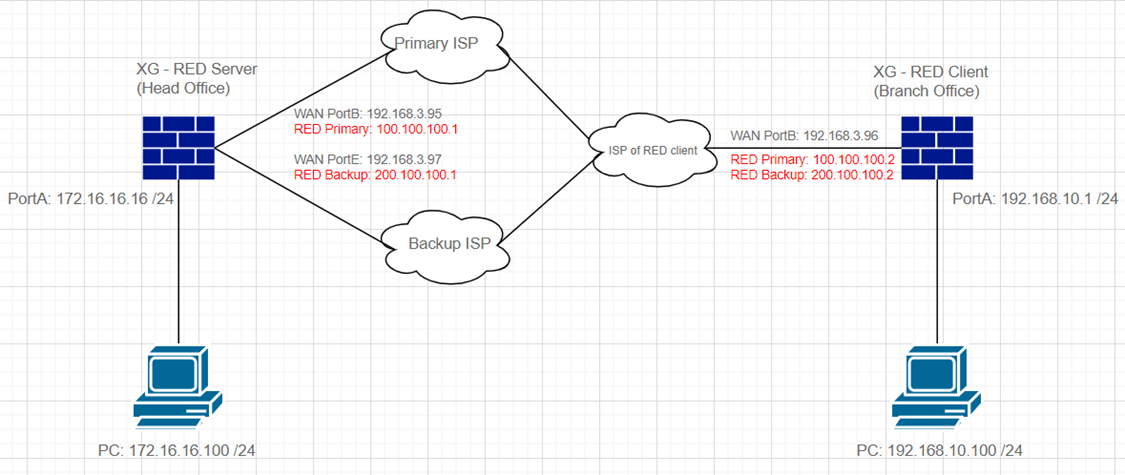
Topology
The remote firewall (Branch Office) has only one WAN connectivity, and the Head Office Firewall has two WAN connections.
Configuration
As a pre-requirement, kindly apply first the KB Sophos Firewall: Create a site-to-site RED tunnel to create two RED VPNs from the remote firewall to the Head Office firewall.
Terminate the two RED tunnels on the two WAN interfaces at the head office.
The picture below is an example of a RED tunnel configuration on the server side. I used the default settings as much as possible:
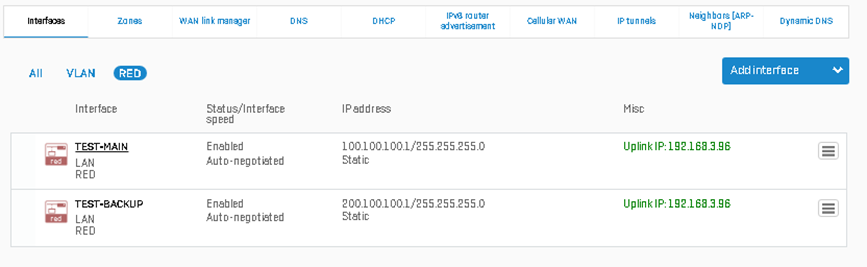
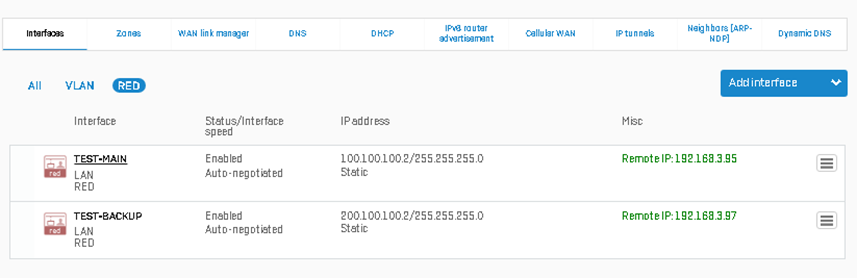
Verify if both RED Tunnels are UP on both ends shown below:
- Head Office:
- Branch Office:
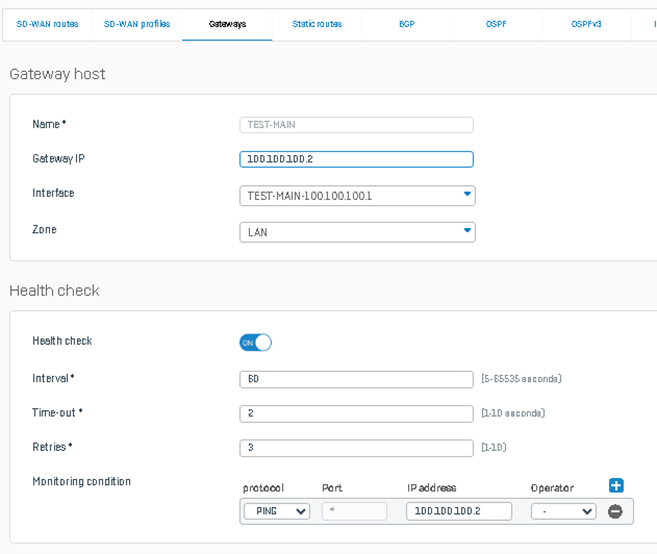
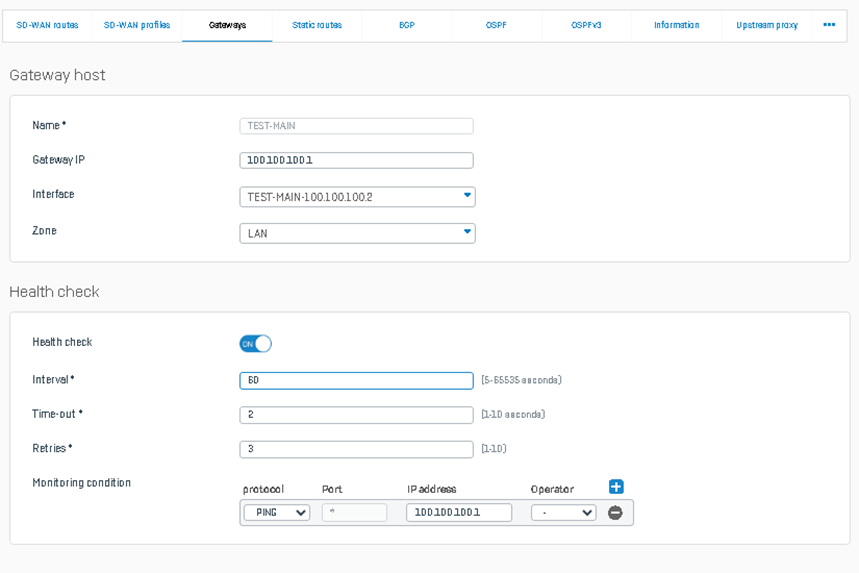
Create a gateway for each RED interface. Go to Routing > Gateways and follow Add a Gateway - Sophos Firewall. Make sure that the Health Check is turned on, as this will indicate whether the other side is reachable.
The picture below is an example of the gateway configuration for the Primary RED interface on the server side. I used the default settings as much as possible:
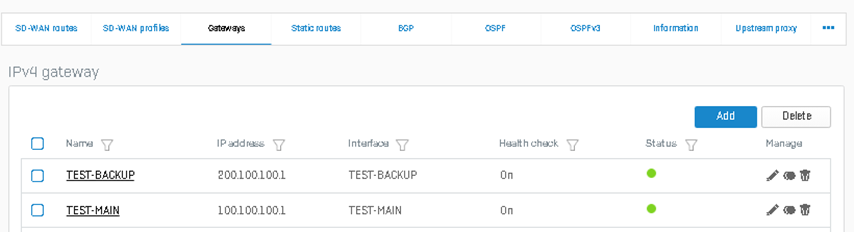
Afterward, make sure all RED gateways created for both HO and BO are UP as shown:
- Head Office:
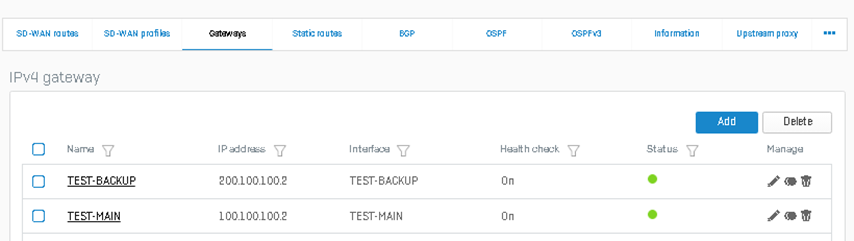
- Branch Office:
After creating the gateways, we’ll create the SD-WAN routes for both HO and BO firewalls. Go to Routing > SD-WAN route to create one.
Below is a sample configuration from the Head Office firewall. Indicate the Source and destination networks. For the Primary and Backup gateways, indicate those created earlier.
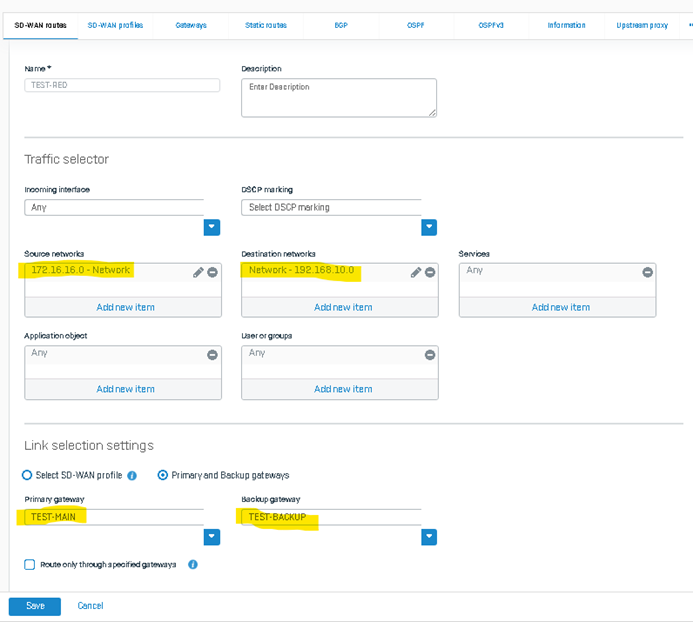
Configuration from the Branch Office firewall:
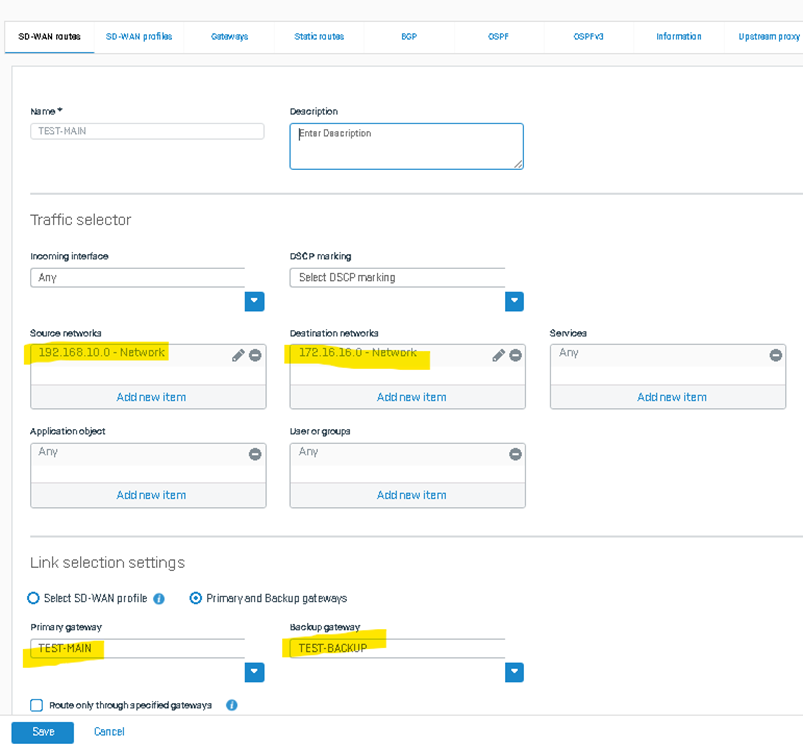
Next is to check the route precedence. It’s recommended that SD-WAN is the topmost priority to ensure that the RED site-to-site traffic will use the SD-WAN route we created. Use this KB Routing - Sophos Firewall to know how to change the route precedence. If a static route is the topmost priority and the user does not want to change the route precedence, ensure that no static routes will conflict with the SD-WAN route. If there’s, delete it.
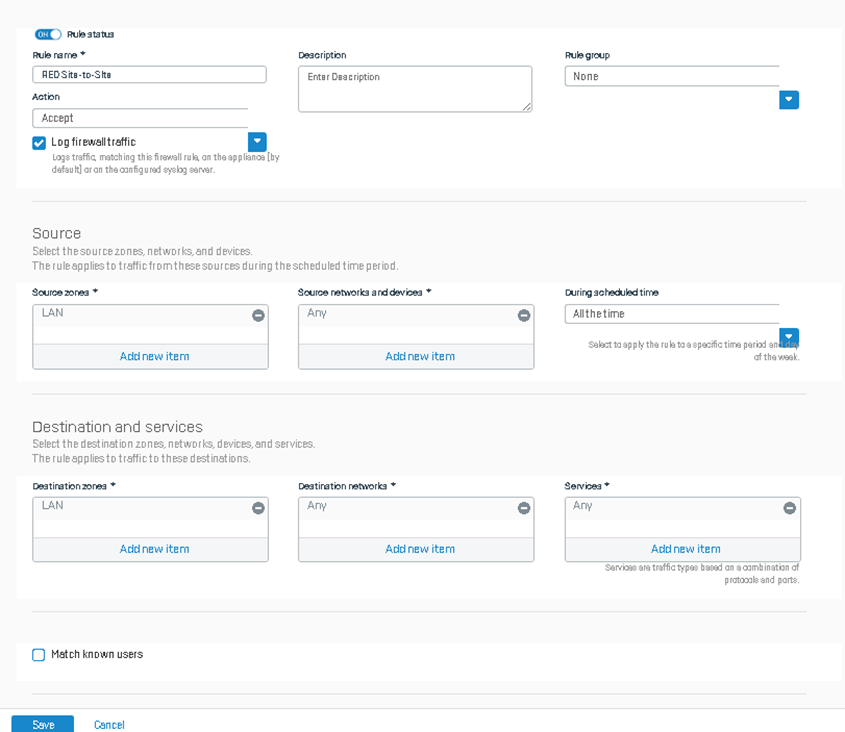
Firewall Rules
Lastly, don’t forget to set up firewall rules. Since the RED interfaces we created are in the LAN Zone, we’ll create a LAN-to-LAN firewall rule. Adjust accordingly if you use a different zone. Here is an example of allowing traffic from LAN to LAN zone.
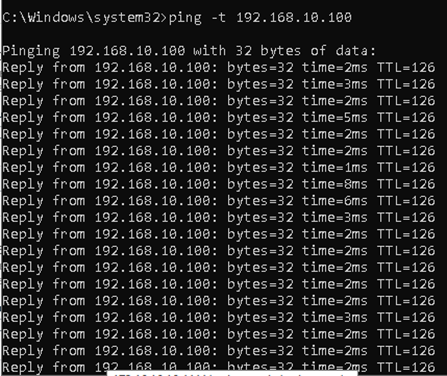
Verification
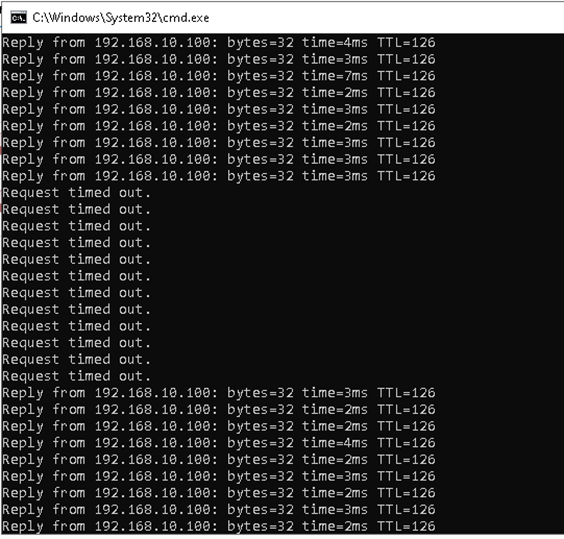
To verify if the failover is working, we’ll run a continuous ping from PC: 172.16.16.100 to PC: 192.168.10.100.
- Sample output is shown:
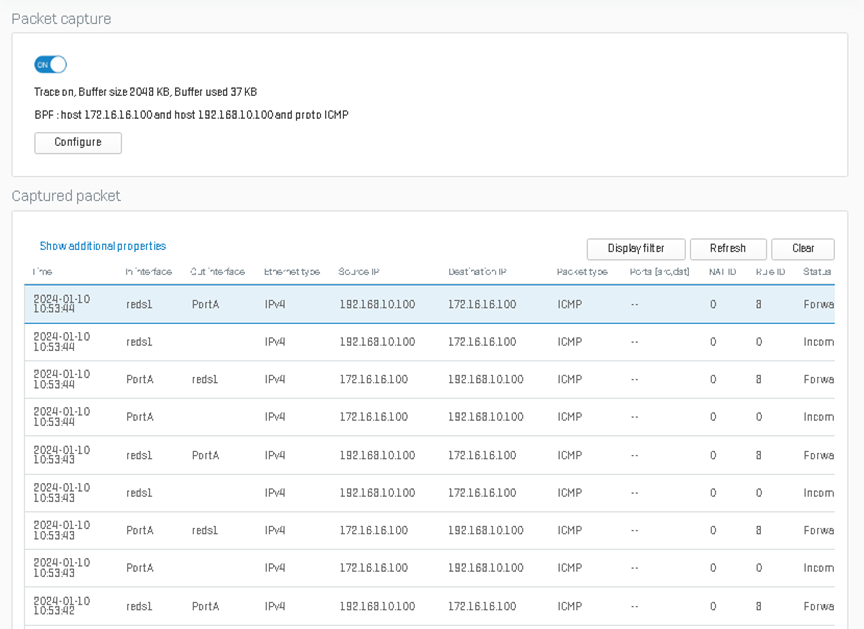
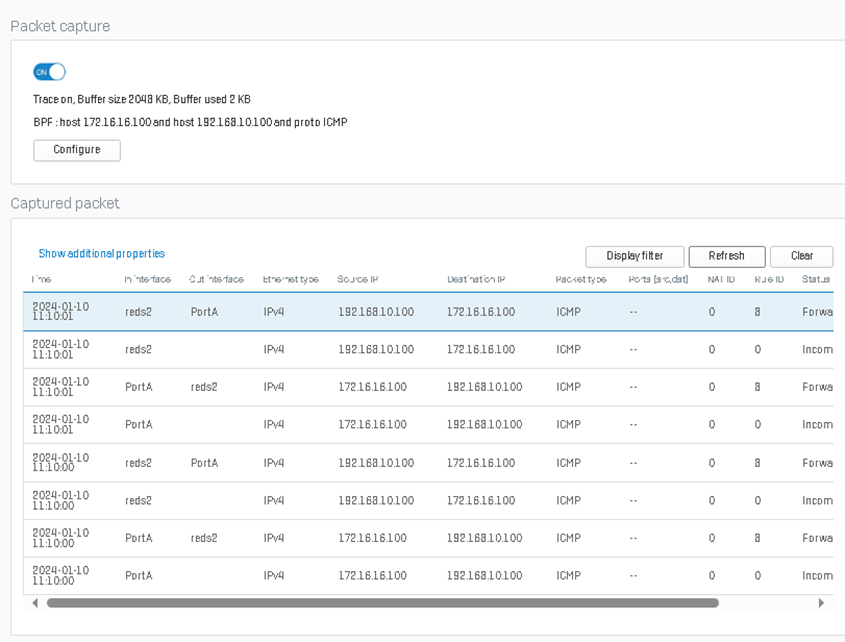
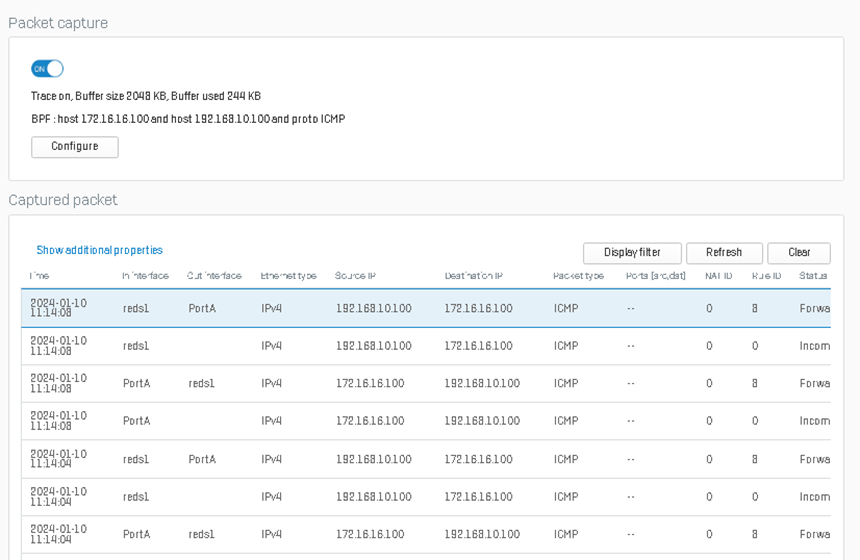
While the ping is running, go to diagnostics > packet capture and use the filter host 172.16.16.100, host 192.168.10.100, and proto ICMP. As shown below, the firewall is forwarding the traffic to reds1, the primary RED tunnel.
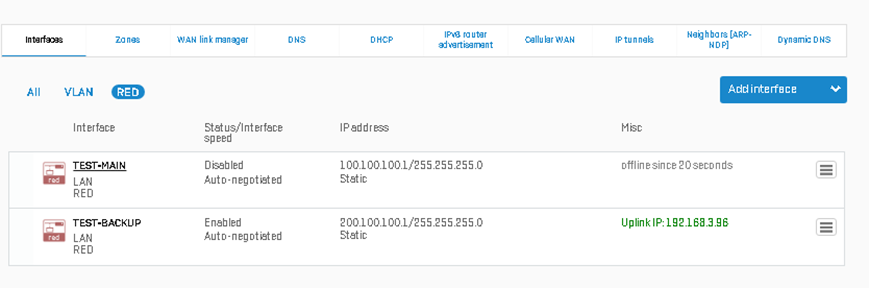
Next, we’ll turn OFF the primary tunnel on the Head Office side as shown and wait for approximately 1 minute for the failover to kick in:
 Checking back the continuous ping after 1 minute, there’s a brief moment of requests time outs, but the ping continues afterward.
Checking back the continuous ping after 1 minute, there’s a brief moment of requests time outs, but the ping continues afterward.
If 1 minute is too long, you can adjust the Health Check parameters on your gateway to a lower value. For more information, see this KB: Add a gateway—Sophos Firewall.
Checking the packet capture from before, we can see that the traffic is now being forwarded to reds2 as reds1 is currently offline.
We’ll turn back ON the primary RED interface as shown:
- As shown in the packet capture, the traffic failback to the reds1 interface as the primary RED interface is online.
Updated links.
[edited by: Raphael Alganes at 2:43 PM (GMT -7) on 10 Oct 2024]

