Update: V21.0 supports Lets Encrypt onboard: Sophos Firewall v21 Early Access Announcement
Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Note: Make sure your Sophos Firewall time is correct to avoid potential Certificate Trust issues
Table of Contents
Overview
Sophos Factory brings a new Tool to automate Script-based approaches. This means you can easily run a Script like Certbot or Lego in a Sophos Factory environment to generate and upload the certificate to the Sophos Firewall.
Sophos Factory offers a "free" Community Edition. https://community.sophos.com/sophos-factory/
Within Sophos Factory, it could look like this:
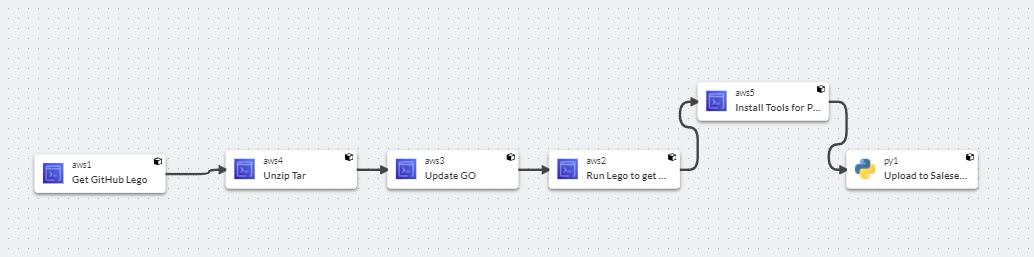
Use the Sophos Factory Community for any Factory Related Questions: Sophos Factory
Let us dig deeper into this scenario:
We’re using Lego to renew the Certificate. Kindly refer to Lego for more information: https://go-acme.github.io/lego/dns/. Lego supports multiple DNS Providers. In this example, we’re using DNS by AWS with the AWS Console Feature of Sophos Factory.
If your DNS Vendor isn’t supported:
You can do this with a DNS Redirect Feature of Lego as well: https://letsencrypt.org/docs/challenge-types/ https://www.eff.org/deeplinks/2018/02/technical-deep-dive-securing-automation-acme-dns-challenge-validation This means, your ACME-Challenge will point to a supported Vendor of Lego. In my example, I am using Route53 by AWS.
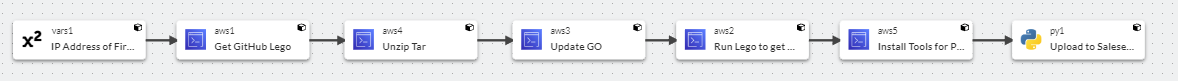
Sophos Factory uses Pipelines to do a job. In this pipeline, we’re installing the tools needed to renew the Wildcard LE Certificate and upload it to the firewall.
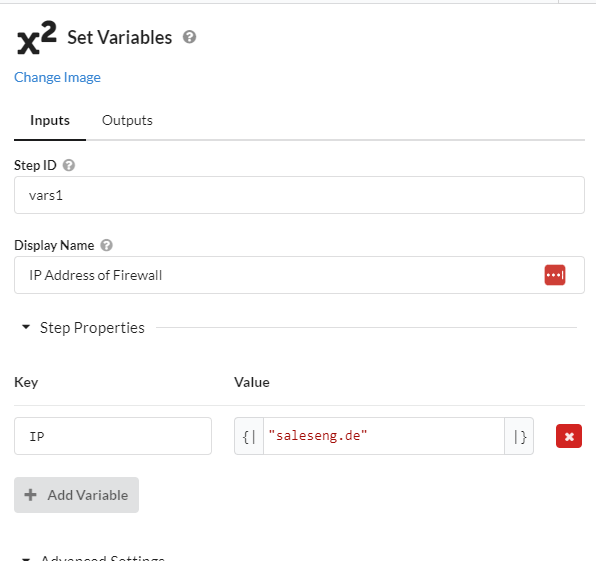
Step1:Firewall Variable
Define the Variable of the Firewall.
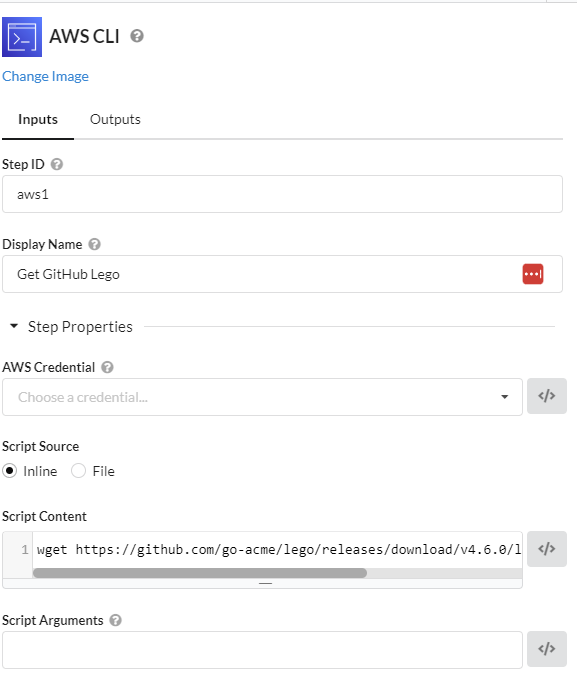
Step2:Lego Repository
Get the Needed repo of Lego (an alternative to Certbot).
Step3:Extracting Repository
Unzip the repo:
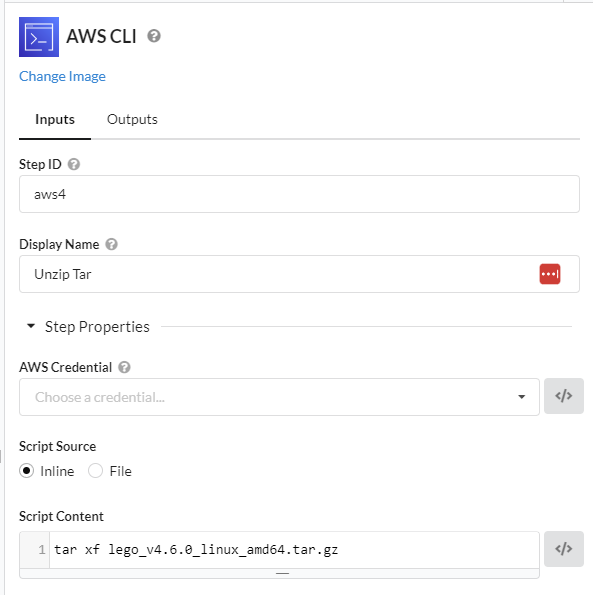
tar xf lego_v4.10.0_linux_386.tar.gz
Step4:Installation and Cloning
Install and clone GO for Lego to run.
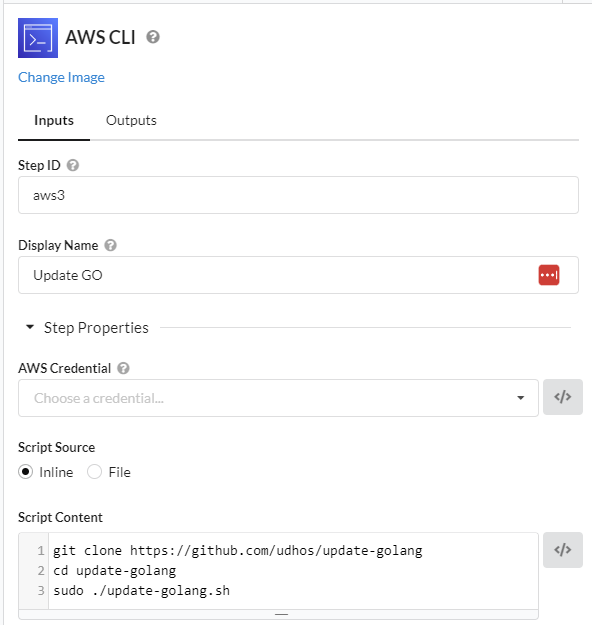
git clone https://github.com/udhos/update-golang cd update-golang sudo ./update-golang.sh
Step5:Running of Lego and Fetching of LetsEncrypt Certificate
Important: We’re running this with AWS Credentials.
You must rename the File directory from "saleseng" to your domain name.
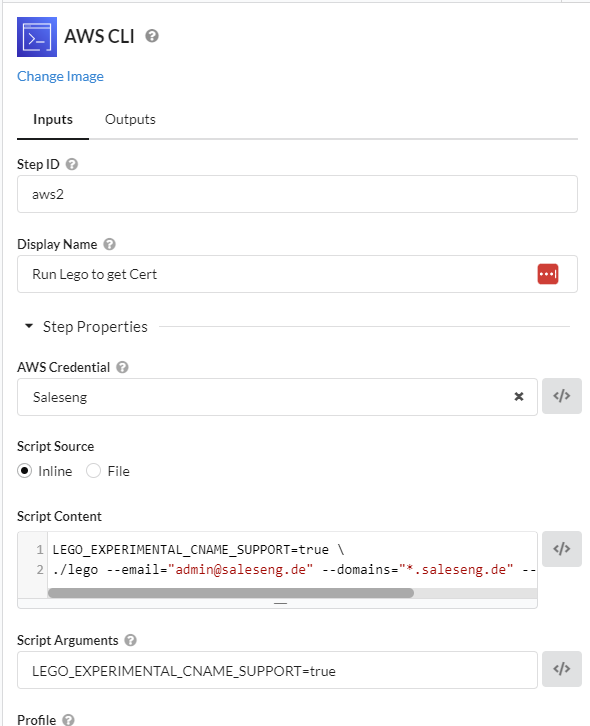
LEGO_EXPERIMENTAL_CNAME_SUPPORT=true \ ./lego --email="admin@saleseng.de" --domains="*.saleseng.de" --dns="route53" -a run
LEGO_EXPERIMENTAL_CNAME_SUPPORT=true
Step6:Uploading Certificate and replace it everywhere
This step can be a Script based from here: Sophos Firewall: [LetsEncrypt] How To in Sophos Firewall
My recommendation would be the following:
Try the renewal and upload it to a Storage of your choice first before you try to automate the entire process. You could also do a renewal process in one step and another pipeline to upload it to the firewall from your storage (Like an S3 bucket).
Important Notice: Be careful with the initial runs, as an invalid renewal process can block your domain for some hours/days by LetsEncrypt. https://letsencrypt.org/docs/rate-limits/
Sophos Factory uses a container approach: This means if you run the renewal and fail to upload it to your storage like a S3 bucket, it’s gone. The Pipeline will be run once, and after the run, all data will be erased by the runner.
Added TAGs
[edited by: Raphael Alganes at 5:27 AM (GMT -7) on 18 Sep 2024]

