Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
______________________________________________________________________________________________________________________________________
Table of Contents
Overview
Sophos Authentication for Thin client (*SATC) with Sophos Server Protection enables Sophos Firewall to authenticate users accessing a server or remote desktop.SATC is included with Sophos Server Protection in Sophos Central. It's part of Sophos Central Server Core Agent and is available with any Server Protection license in Sophos Central. Currently, SATC with Sophos Server Protection only supports Windows Remote Desktop Services. You must download the Windows Server installer from Sophos Central. The installers that you can download would depend on the licenses you have.
Sophos Firewall controls those authenticated users using a session-based approach via an identity-based firewall rule, providing more granular access controls for each user group.
*Note: SATC functionality is only supported on Windows Server 2016 and requires a Core Agent of 2022.2 and higher.
What To Do
Follow the steps below to set up new SATC client integration with Sophos Server Protection:
For full details on enabling SATC with Sophos Central Server Protection see this help document: SATC with Sophos Server Protection.
The steps below walk through the setup:
-
Turn off tamper protection for server protection. Note the current settings before you turn off tamper protection, as you need to change these back once SATC is activated.
- On the server, open a command-line console/Power Shell. Add new parameter Satc PendDuration Ms in SATC, run the following command to turn on SatcPendDurationMs parameter
command: - reg add "HKLM\Software\Sophos\Sophos Network Threat Protection\Application" /v SatcPendDurationMs /t REG_DWORD /d 300
NOTE: We are updating the pend duration only when there is network latency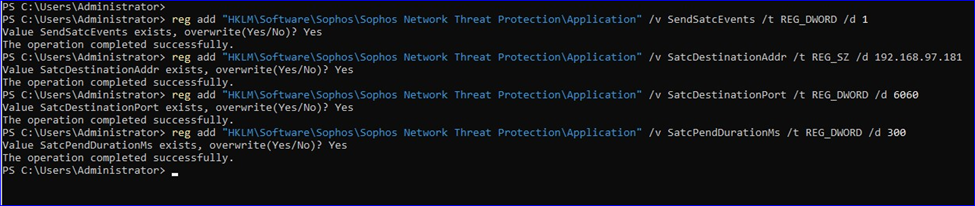
- Please ensure to reboot the Terminal Server once changes are applied.
- Lastly, check the windows registry to confirm the changes under: HKLM\Software\Sophos\Sophos Network Threat Protection\Application
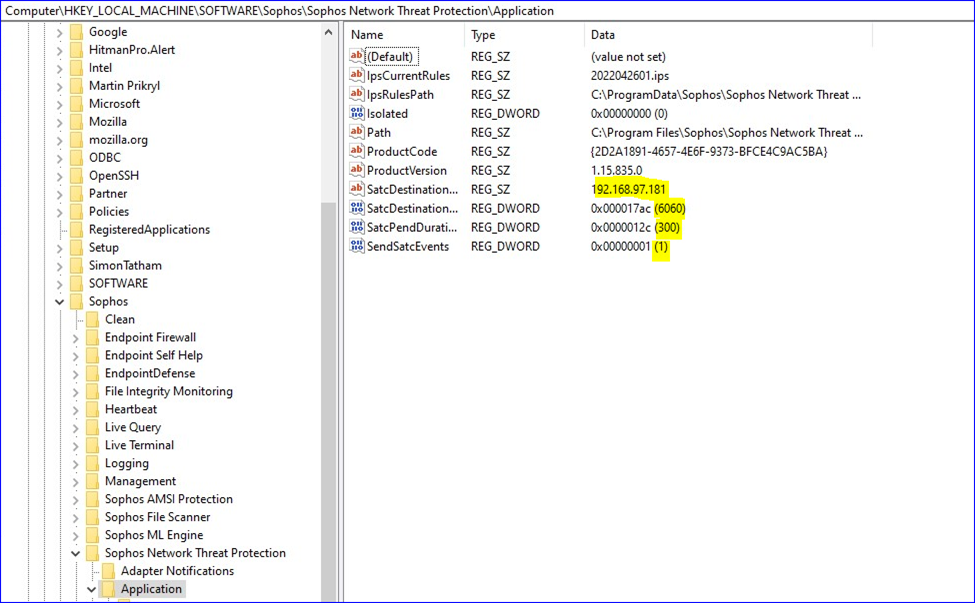
-
If you face any issues or need further assistance with this, kindly reach out to our Sophos Support team - support.sophos.com
______________________________________________________________________________________________________________________________________
Updated links to latest
[edited by: Raphael Alganes at 11:56 AM (GMT -8) on 18 Nov 2024]

