Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
______________________________________________________________________________________________________________________________________
Table Of Contents
SSL Inspection:
In order to apply SSL Inspection in Sophos Firewall, an administrator requires to install the SecurityAppliance_SSL_CA if you're using default CA. An admin can use a CA signed from their Organization's Root CA if they already have the PKI set up in their organization. Some of the benefits of using this are:
- Not using self-signed CAs that are unique to each Sophos Firewall appliance. Reduces certificate management sprawl and redistribution of certs, especially in environments that use multiple firewalls.
- Security best practice to not use self-signed CAs. Visibility and better key management of the resigning CAs is achieved.
- Cert deployment is handled with AD and GPOs. As long as the client trusts the Root CA, the resigning subordinate CA is trusted.
- Eases administrative burden in most cases.
Configuration
In order to do this, you will first need to go through the following steps:
- Create a CSR for your specific environment and download the CSR tarball from your Sophos Firewall device (KBA: How to generate a certificate signing request (CSR)).
- Extract the tarball contents and save it.
- Open the CSR in a notepad editor and copy the contents.
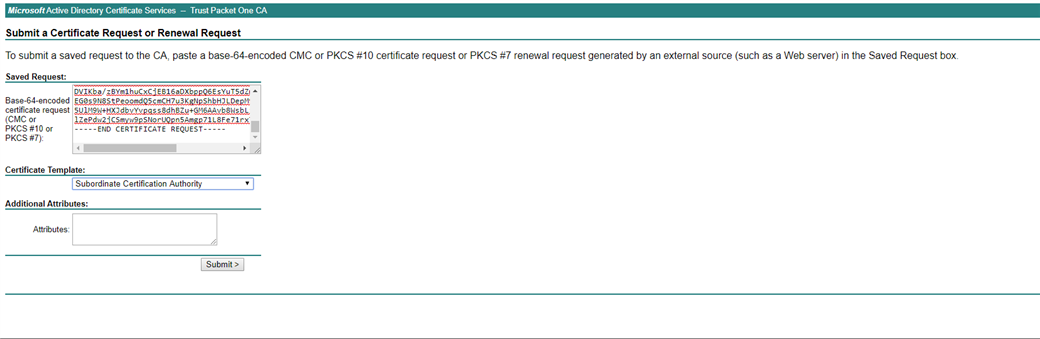
- On your Microsoft Server CA, create a new advanced certificate signing request using “Subordinate Certificate Authority” as the template type and paste the CSR:
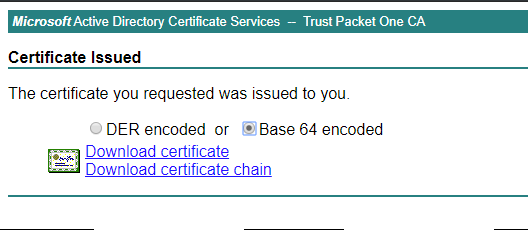
- Download the signed Subordinate CA certificate:
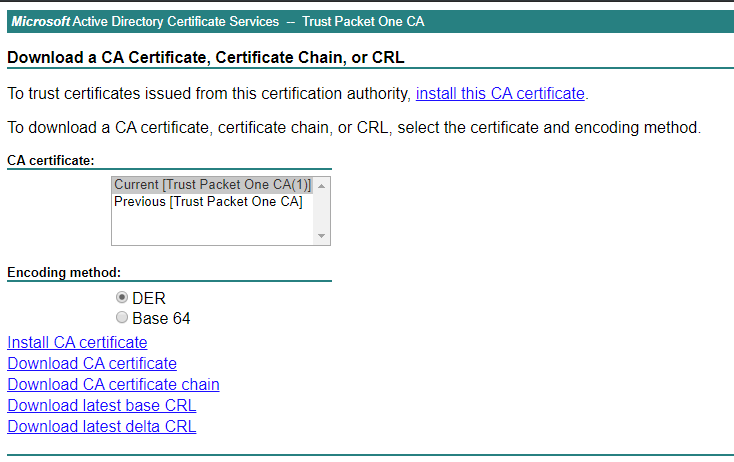
- Download the Root CA certificate:
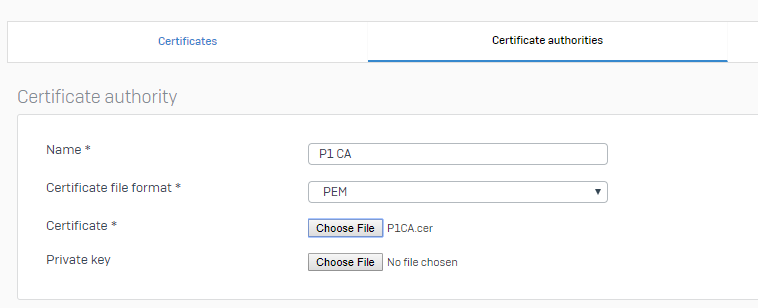
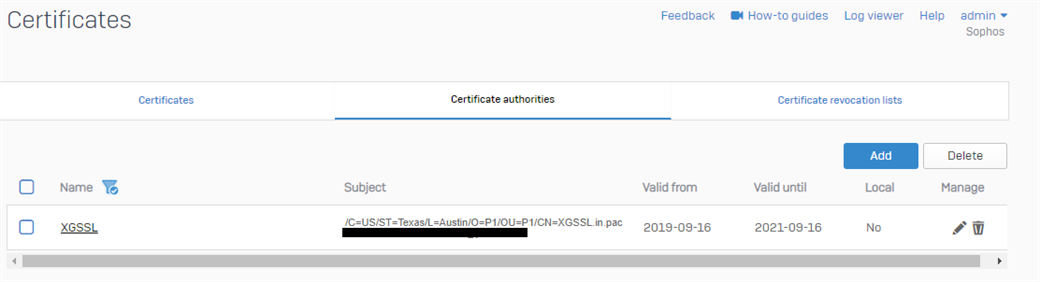
- Return to Sophos Firewall and upload the Root CA certificate to XG under SYSTEM > Certificates > Certificate Authorities:
- Now, DO NOT return to the Certificates page to import the signed Subordinate CA certificate. Instead, use the Certificate authorities section. Select PEM format, import the signed Subordinate certificate, upload the private key extracted from the previously downloaded tarball, and provide a passphrase.
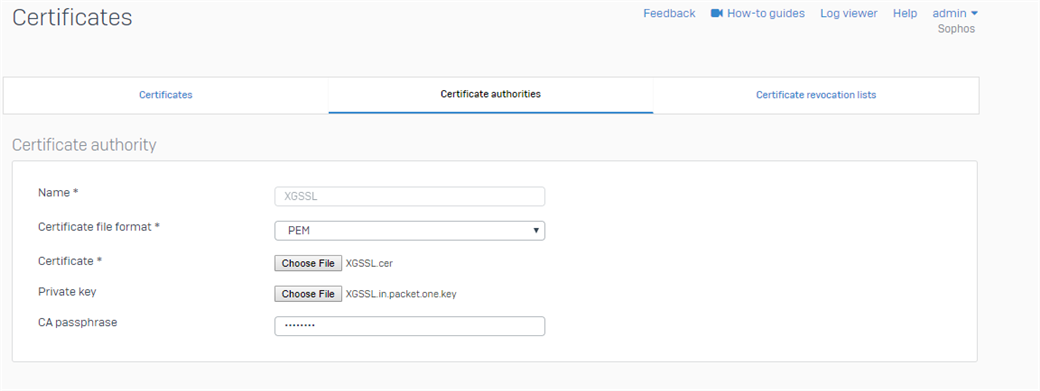
- Find the imported certificate in the list:
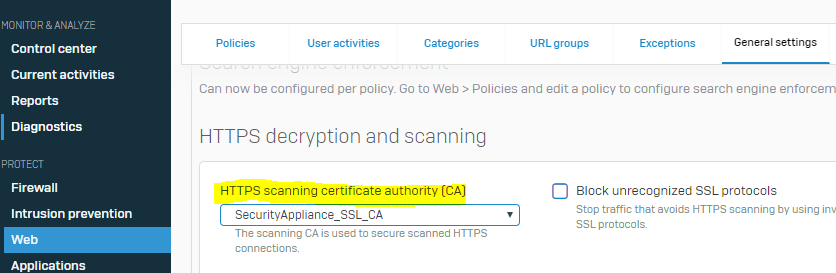
- Select the newly uploaded Sophos Firewall SSL CA under PROTECT > Web > General settings | HTTPS decryption and scanning to use the new Subordinate CA:
- Assuming the client already has the Root CA installed, validate SSL inspection works by opening the certificate in your browser and check if the signing CA is the same as you selected in the previous step.
Following the steps mentioned above, you should be able to implement proper SSL scanning using your Sophos Firewall without needing to install additional CA in your machines.
Added TAGs
[edited by: Raphael Alganes at 5:13 AM (GMT -7) on 18 Sep 2024]

