Overview
This article describes the steps to troubleshoot SSL VPN remote access connectivity and data transfer issues. Before proceeding to troubleshoot, please verify that the SSL VPN remote access is configured correctly by following Sophos Firewall: How to configure SSL VPN remote access.
SSL VPN remote access users are not able to connect
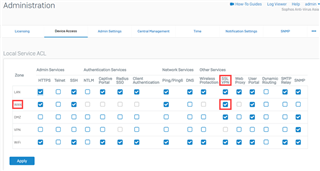
Verify the users portal accessibility
Make sure that the SSL VPN service is selected for the WAN interface under Administration > Device Access.
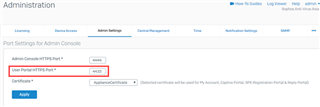
Verify the admin port settings
Make sure the SSL VPN users are accessing the portal using the port configured under Administration > Admin Settings.
Verify the certificate
Make sure that the proper certificate is associated with the SSL VPN user. Using the appliance certificate and regenerate the certificate if required is recommended. For more details, please refer to Sophos Firewall: Self signed certificates are not supported as SSL server certificate in SSL VPN.
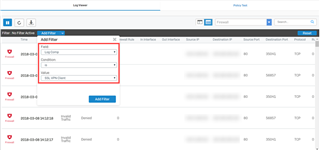
Verify the logs from the GUI
Go to Log Viewer and filter the Log Comp to SSL VPN Client.
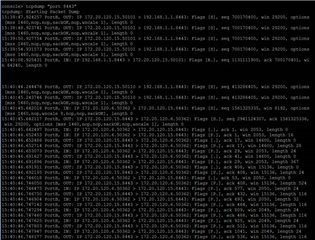
Verify the SSL VPN traffic flow from the console
Log in to the command-line interface (CLI) and select 4: Device Console. Run the following command, which uses the default SSL VPN port 8443, to analyze the output.
tcpdump "port 8443"
Verify the logs from the advance shell
Log in to the command-line interface (CLI) and select 5: Device Management then 3: Advanced Shell and type the following command:
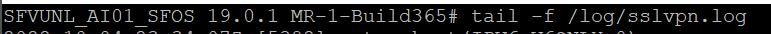
tail -f /log/sslvpn.log
Verify the logs from SSL VPN Client
Right-click SSL VPN Client from your PC taskbar and select View Log.
Verify the user has proper SSL VPN remote access policy assigned
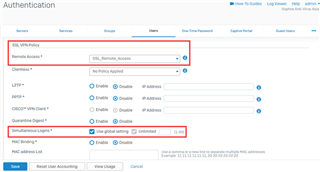
Go to Authentication > Users and confirm that the SSL VPN user has two or more simultaneous logins allowed, in case if the user is simultaneously logged in from different machines at the same time.
Verify the SSL VPN authentication method
When receiving the Auth-failure error message in logs, verify the authentication method under Authentication > Services > SSL VPN Authentication Methods.
SSL VPN users are not able to transfer data
Verify the firewall rule
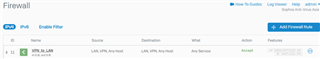
In the event that the SSL VPN connects successfully but users are not able to connect to the allowed resources behind the Sophos XG Firewall, verify if a firewall rule is created and configured. If any specific service is selected in this rule, try allowing any service and check the connectivity.
Verify the accessibility of the resources
Log in to the command-line interface (CLI) and select 4. Device Console. Verify that the internal allowed resource is accessible from the Sophos XG Firewall itself. As an example, you can ping an internal resource from the Sophos XG Firewall's console. If the allowed resources are not accessible from the Sophos XG Firewall, then they would not be accessible from the WAN side.
Verify the permitted network resources
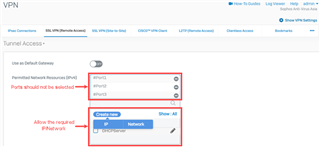
Make sure that the physical ports of the Sophos XG Firewall are not allowed in the Permitted Network Resources (IPv4) of the Tunnel Access section under VPN > SSL VPN (Remote Access). If allowed, the SSL VPN user would not be able to access the internal network, instead, create a new IP Host/Network for SSL VPN user access.
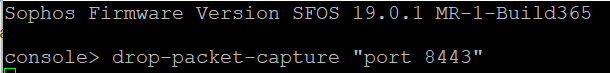
Verify the drop packet capture for SSL VPN
Log in to the command-line interface (CLI) and select 4. Device Console to run the following command, which uses the default SSL VPN port 8443.
drop-packet-capture “port 8443”
SSL VPN is restarting frequently
Verify that the WAN port of the Sophos Firewall is not allowed under VPN > SSL VPN (Remote Access) > Tunnel Access > Permitted Network Resources (IPv4). If it is allowed, the SSL VPN client could disconnect frequently.
Note: As a last resort, try uninstalling the SSL VPN remote access client and reinstall it.
Have an idea or suggestion regarding our Documentation, Knowledgebase, or Videos? Please visit our User Assistance forum on the Community to share your feedback! https://community.sophos.com/community-chat/f/user-assistance-feedback
Updated Horizontal lines, links
[edited by: Raphael Alganes at 9:52 AM (GMT -8) on 14 Nov 2024]