Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Note: Make sure your Sophos Firewall time is correct to avoid potential Certificate Trust issues
Table of Contents
Overview
This Recommended Read reviews different options for obtaining a Let's Encrypt certificate.
UTM has LE Support for WAF (since UTM9.6). But on Sophos, you can use LE certificates as well. Seems like many people does not know, you need a little Linux server and 5-10 minutes of your time each three month. Or you can automate this.
First of all, I want to share the "how it works" page of LE. https://letsencrypt.org/how-it-works/
My Setup.
Internet - Sophos - Ubuntu 20.04 LTS
Ubuntu has "certbot" installed. Feel free to use other LE modules.
https://certbot.eff.org/ https://certbot.eff.org/lets-encrypt/ubuntubionic-apache
Follow straight the Guide for your OS. I am relying fully on those apps for the renewal process.
Next, I am choosing the HTTP-01 method for LE, so I need a DNAT for LE to my Ubuntu.
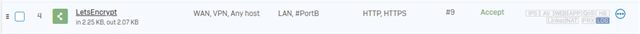
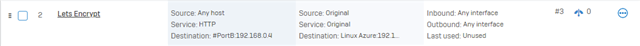 (V18).
(V18).
PS: I am using HTTP DNAT for the renewal process and deactivate those Rules after the process. But you can also use only the LE IPs:
https://community.letsencrypt.org/t/can-i-get-list-ip-from-letsencrypt/57117
PS2: You could switch to the DNS validation as explained in this Community thread.
The next step would be to check your Domain. Your DNS A-Record should point to your WAN IP. Otherwise, this process won’t work.
So perform a dig / nslookup of your domain. It’ll point to your WAN IP, so your DNAT will work, and HTTP packets will be forwarded to Certbot.
You can also use the Sophos free DDNS service. https://community.sophos.com/kb/en-us/123126
Certbot
Let us start Certbot and try it.
My renewal process is straightforward:
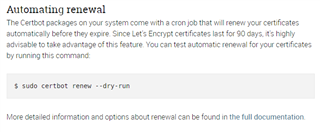
(Be careful: LE blocks you after couple of "failed" requests for some time. So check everything).
Ultimately, you’ll get four files on your Linux: Public, Chain, Fullchain, Privatkey Certificates.
Upload to Sophos Firewall
You’ll use this Public and Privatkey certificate.
There are a couple of approaches to upload this to Sophos. 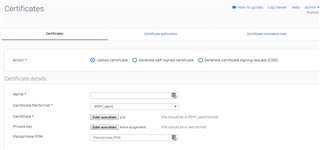
The first LE Cert can be uploaded.
You should use the Public.pem in "Certificate" and the Privatkey in "Privat key".
PS: you have to rename the Privatkey.pem to Privatkey.key. Otherwise, Sophos won’t take this certificate.
Optionally, you can upload the other Chain and fullchain Certificate under Certificate Authorities (Without Privat key).
Now, you can use this Certificate for WAF/Webadmin.
In case of renewal (each 90 Days), you have to choose a process.
Automation
You can upload the new LE certificate with another Name and replace it in WAF/Webadmin.
Or you can "update" the current LE certificate with the new public.pem / privat.key. But for this method, you have to switch to a fallback certificate in WAF/Webadmin, because Sophos can't update a currently used certificate.
After all, those steps are manual processes every 90 Days.
You can "script" this if you want to. So basically, upload the certificate every 90 Days to Sophos.
Other members of the community have already performed scripts for this.
- https://community.sophos.com/sophos-xg-firewall/f/discussions/102208/upload-certificate-using-api
- https://community.sophos.com/sophos-xg-firewall/f/discussions/126295/automatically-renew-let-s-encrypt-ssl-certificates-on-Sophos -using-powershell
- https://github.com/mmccarn/sophos
- https://community.sophos.com/sophos-xg-firewall/f/discussions/129768/letsencrypt-api-update-script---dynamically-handles-multiple-certs-multiple-rules-including-re-grouping-of-policies-rules
- https://community.sophos.com/sophos-xg-firewall/f/discussions/134534/sophos-Sophos -api-lets-encrypt-powershell-7-waf-update
- https://community.sophos.com/sophos-xg-firewall/f/discussions/138668/upload-certificates-using-powershell-to-automate-let-s-encrypt
If you want to script this, this community can help you if you struggle with a point.
So please open a new thread with your issue with the API, and we’ll try to find a solution.
Sophos Factory
Sophos Factory brings a new Tool to automate Script-based approaches. This means you can easily run a Script like Certbot or Lego in a Sophos Factory environment to generate and upload the certificate to the Sophos Firewall.
Sophos Factory offers a free Community Edition. https://community.sophos.com/sophos-factory/ https://community.sophos.com/sophos-factory/b/release-notes-news/posts/get-started-here-sophos-factory-offer-automation-for-all-with-its-free-community-edition
Within Sophos Factory, it could look like this:
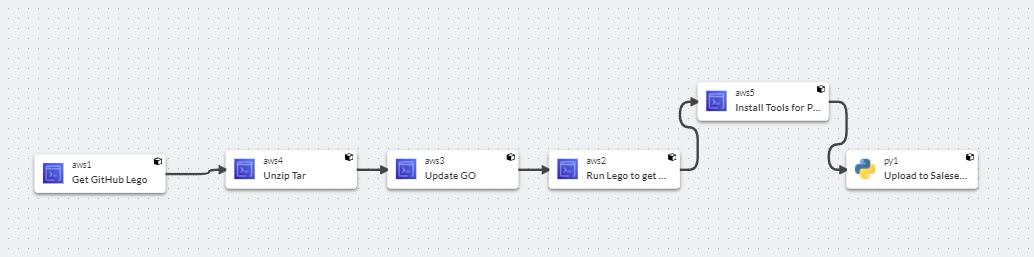
Each step is one scripting component.By using tools like Lego and Github, the "Pipeline" will run one time, generate the certificate and upload it to the Firewall.
Contribution:
rgreat https://zerossl.com/free-ssl/#crt Free alternative to this approach
LucianoRodriguezFor the Github script.
burton, Thanks for the PHP Script!
nplm85 for a Powershell Script with WAF integration.
Martin Walter for another version of a Powershell Script.
Edited Links
[edited by: emmosophos at 10:23 PM (GMT -8) on 5 Mar 2024]

