Good morning.
I have several XG/XGS of different clients configured with IPSEC against the same central, this central uses a CISCO firewall (we do not manage it).
The problem we have is that every 30 minutes we receive an email from all the XG/XGS indicating that the tunnel is down/up but no one has complained about connection losses since they are “micro outages”.
Checking the logs comes up with the following:
<CLIENTE-1|14700>received DELETE for IKE_SA CLIENTE-1[14700]
<CLIENTE-1|14700> deleting IKE_SA CLIENTE-1[14700] between 90.90.90.90[90.90.90.90]...217.217.217.217[217.217.217.217]
24[IKE] <CLIENTE-1|14700> restarting CHILD_SA CLIENTE-1
24[IKE] <CLIENTE-1|14700> initiating IKE_SA CLIENTE-1[14704] to 217.217.217.217
24[ENC] <CLIENTE-1|14700> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
24[NET] <CLIENTE-1|14700> sending packet: from 90.90.90.90[500] to 217.217.217.217[500] (922 bytes)
24[IKE] <CLIENTE-1|14700> IKE_SA deleted
24[APP] <CLIENTE-1|14700> [COP-UPDOWN] (ref_counting) ref_count: 1 to 0 -- down -- (192.168.200.142/32#192.168.100.142/32)
24[APP] <CLIENTE-1|14700> [COP-UPDOWN] (ref_counting_remote) ref_count_remote: 1 to 0 -- down -- (90.90.90.90#217.217.217.217#n)
24[APP] <CLIENTE-1|14700> [COP-UPDOWN] (cop_updown_invoke_once) UID: 14700 Net: Local 90.90.90.90 Remote 217.217.217.217 Connection: CLIENTE Fullname: CLIENTE-1
24[APP] <CLIENTE-1|14700> [COP-UPDOWN] (cop_updown_invoke_once) Tunnel: User '' Peer-IP '' my-IP '' down-client
24[ENC] <CLIENTE-1|14700> generating INFORMATIONAL response 179 [ ]
24[NET] <CLIENTE-1|14700> sending packet: from 90.90.90.90[500] to 217.217.217.217[500] (96 bytes)
12[APP] [COP-UPDOWN][DB] (db_conn_info) hostname: 'CLIENTE' result --> id: '3', mode: 'ntn', tunnel_type: '0', subnet_family:'0'
29[NET] <CLIENTE-1|14704> received packet: from 217.217.217.217[500] to 90.90.90.90[500] (574 bytes)
29[ENC] <CLIENTE-1|14704> parsed IKE_SA_INIT response 0 [ SA KE No V V N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) V ]
29[IKE] <CLIENTE-1|14704> received Cisco Delete Reason vendor ID
29[IKE] <CLIENTE-1|14704> received Cisco Copyright (c) 2009 vendor ID
29[IKE] <CLIENTE-1|14704> received FRAGMENTATION vendor ID
29[IKE] <CLIENTE-1|14704> authentication of '90.90.90.90' (myself) with pre-shared key
29[IKE] <CLIENTE-1|14704> establishing CHILD_SA CLIENTE-1{2345}
29[ENC] <CLIENTE-1|14704> generating IKE_AUTH request 1 [ IDi IDr AUTH SA TSi TSr N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
29[NET] <CLIENTE-1|14704> sending packet: from 90.90.90.90[500] to 217.217.217.217[500] (384 bytes)
11[NET] <CLIENTE-1|14704> received packet: from 217.217.217.217[500] to 90.90.90.90[500] (304 bytes)
11[ENC] <CLIENTE-1|14704> parsed IKE_AUTH response 1 [ V IDr AUTH SA TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
11[IKE] <CLIENTE-1|14704> authentication of '217.217.217.217' with pre-shared key successful
11[IKE] <CLIENTE-1|14704> IKE_SA CLIENTE-1[14704] established between 90.90.90.90[90.90.90.90]...217.217.217.217[217.217.217.217]
11[IKE] <CLIENTE-1|14704> scheduling rekeying in 28415s
11[IKE] <CLIENTE-1|14704> maximum IKE_SA lifetime 28775s
11[IKE] <CLIENTE-1|14704> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
11[KNL] <CLIENTE-1|14704> ipsec_offload enabled
11[KNL] <CLIENTE-1|14704> ipsec_offload interface Port2
11[KNL] <CLIENTE-1|14704> ipsec_offload enabled
11[KNL] <CLIENTE-1|14704> ipsec_offload interface Port2
11[IKE] <CLIENTE-1|14704> CHILD_SA CLIENTE-1{82798} established with SPIs cba6a5cc_i f891532d_o and TS 192.168.200.142/32 === 192.168.100.142/32
11[APP] <CLIENTE-1|14704> [COP-UPDOWN] (ref_counting) ref_count: 0 to 1 ++ up ++ (192.168.200.142/32#192.168.100.142/32)
11[APP] <CLIENTE-1|14704> [COP-UPDOWN] (ref_counting_remote) ref_count_remote: 0 to 1 ++ up ++ (90.90.90.90#217.217.217.217#n)
11[APP] <CLIENTE-1|14704> [COP-UPDOWN] (cop_updown_invoke_once) UID: 14704 Net: Local 90.90.90.90 Remote 217.217.217.217 Connection: CLIENTE Fullname: CLIENTE-1
11[APP] <CLIENTE-1|14704> [COP-UPDOWN] (cop_updown_invoke_once) Tunnel: User '' Peer-IP '' my-IP '' up-client
12[APP] [COP-UPDOWN] (do_cop_updown_invoke_once) connection 'CLIENTE' using interface 'ipsec0'
12[APP] [COP-UPDOWN] (add_routes) no routes to del for CLIENTE on interface ipsec0
12[APP] [COP-UPDOWN][SHELL] (run_shell) '/bin/opcode set_timer_mail_updown -s nosync -t json -b '{"event":"down","conn":"CLIENTE","local_net":"192.168.200.142/32","remote_net":"192.168.100.142/32","reason":"0"}'': success 0
12[APP] [COP-UPDOWN][DB] (db_conn_info) hostname: 'CLIENTE' result --> id: '3', mode: 'ntn', tunnel_type: '0', subnet_family:'0'
12[APP] [COP-UPDOWN] (do_cop_updown_invoke_once) connection 'CLIENTE' using interface 'ipsec0'
12[APP] [COP-UPDOWN] (add_routes) no routes to add for CLIENTE on interface ipsec0
2024-08-14 08:15:45Z 12[APP] [COP-UPDOWN][SHELL] (run_shell) '/bin/opcode set_timer_mail_updown -s nosync -t json -b '{"event":"up","conn":"CLIENTE","local_net":"192.168.200.142/32","remote_net":"192.168.100.142/32","reason":"0"}'': success 0
Is the CISCO equipment dropping the connection every 30 minutes?
In the VPN profile we do not have anything configured that indicates that it restarts every 30 minutes:
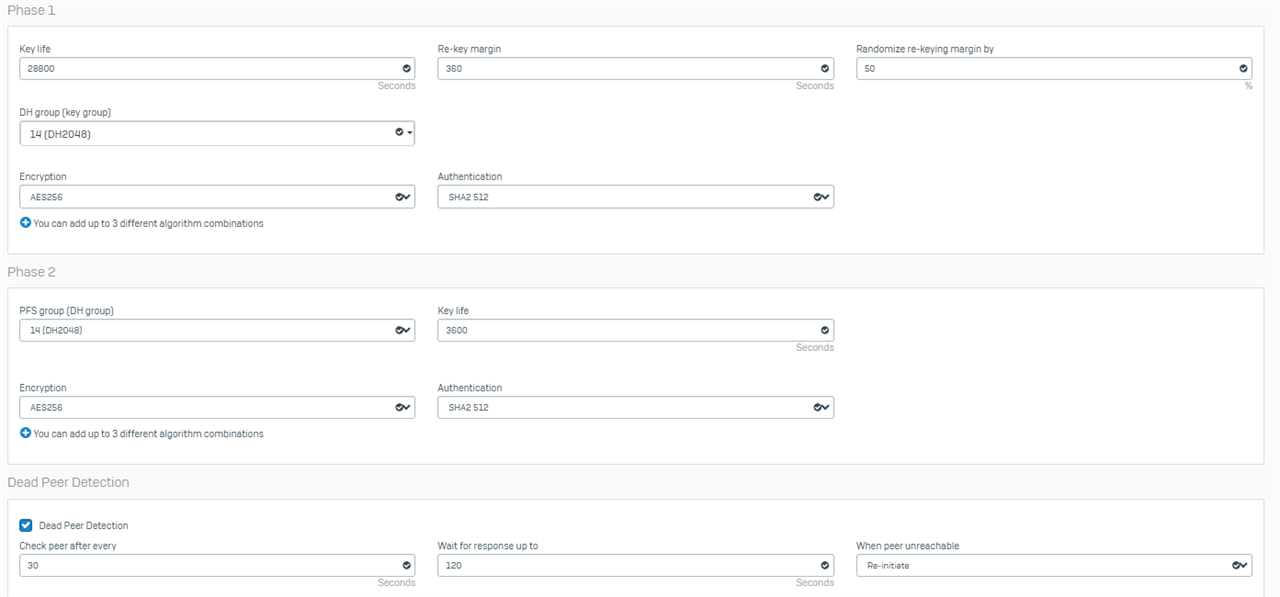
Thanks!!!!
Edited TAGs
[edited by: Erick Jan at 3:28 PM (GMT -7) on 2 Sep 2024]


