Hey Folks,
we rolled out a XGS126 in our Branch yesterday (before SG125) and we cannot get Veeam to work backing up our Branch VMs.
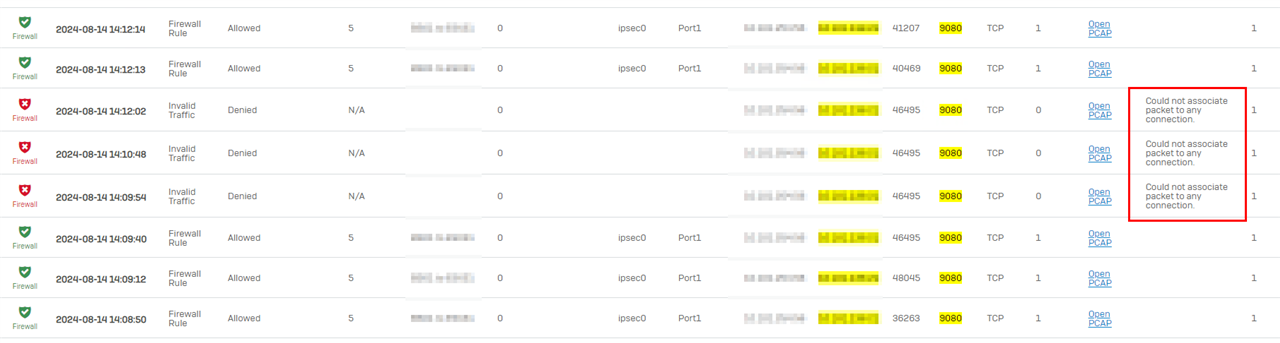
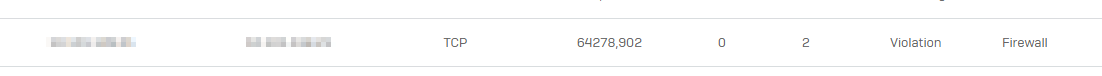
The Branch is connected via IPSEC VPN Tunnel to our Datacenter (Sophos SG310). I already found the older thread Veeam B&R 12 issue - Discussions - Sophos Firewall - Sophos Community but nothing works, and Veeam backup still fails -> always gets stucked at "Getting VM info from vSphere" -> NFC storage connection is unavailable ..... Failed to create NFC download stream....
Things done so far:
Checking the Logs -> IPS, ATR, ZDP no entries
Disabled, IPS, MDR threat feeds, and x-ops threat feeds (ATP) - no luck
set ips ac_atp exception fwrules 5 -> no luck (FW Rule of Backupserver to ESX Server)
created a SSL/TLS inspection rule to exclude -> Source VPN Backupserver to LAN ESX Server, with Don't decrypt and max compatibility - no luck
added local.domain and FQDN of Backupserver and ESX server to Local TLS exclusion list - no luck
at the moment i am out of ideas, hence any other help would be very much appreciated.
Thanks.
Peter
This thread was automatically locked due to age.