Hi,
I have a Sophos XGS107 (SFOS 20.0.1 MR-1-Build342) setup with Site to Site vpn to a Mikrotik router.
There is 4 vpn tunnels (or separate address pairs), It mostly works fine, but every other day one tunnel goes down. If I check in webgui >> site to site vpn, active is green and most of the time connection is green. But if I check in "i" then one address pair is yellow and no traffic pass.
I have 3 Sophos UTM 9 with the exact same setup to same Mikrotik Router, and they never goes down.
The only error message I see is
First,
IPSec Terminated Couldn't parse IKE message from x.x.x.93[500]. Check the debug logs.
Then
IPSec Failed IPSec_VPN_-1 - Couldn't parse IKE message from x.x.x.93[500]. Check the debug logs. (Remote: x.x.x.93)
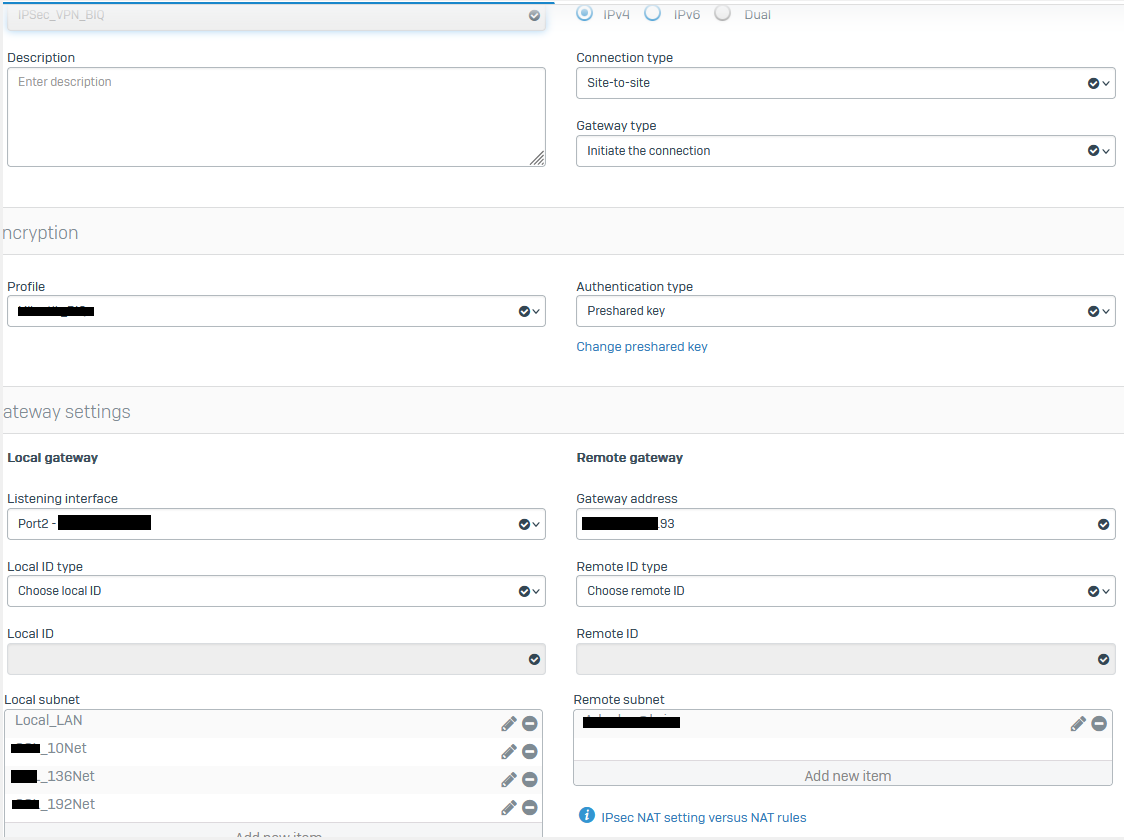
Perhaps the setup is a bit daft, behind the Sophos SGX thereare 4 networks, 1 local lan and 3 remote lans the is connected on a separate link..
Users on the local lan needs to connect to a server behind the Mikrotik router and the server behind the Mikrotik router need to connect to servers on the remote lans behind the Sophos FW.
Should I have two separate vpn tunnels, one with the sophos as remote office and one with sophos as Head office? Just related to who initiate the traffic
I do think it should work anyway.
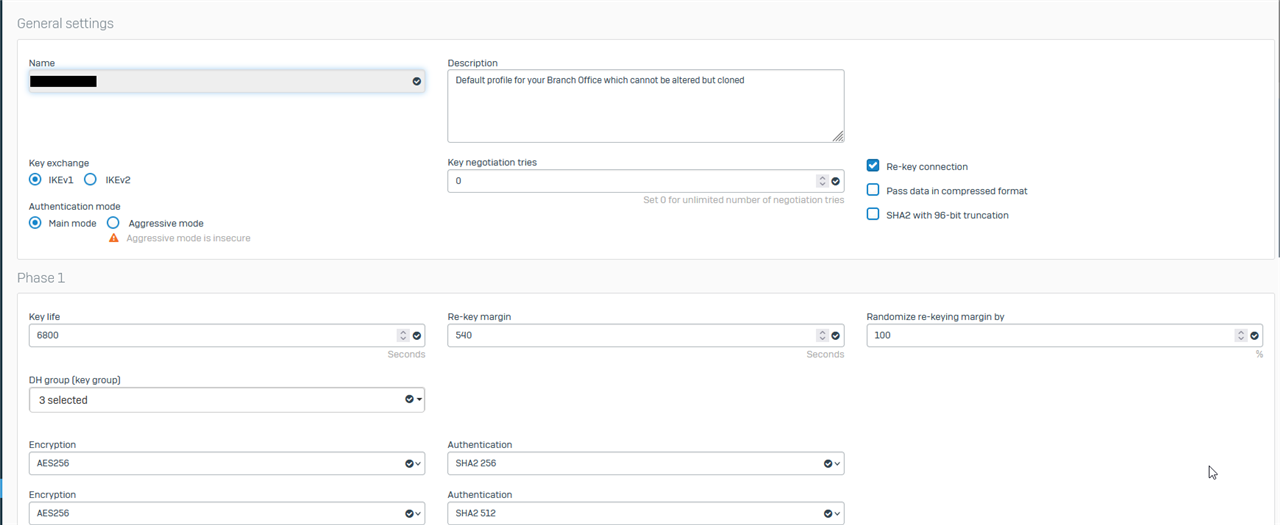
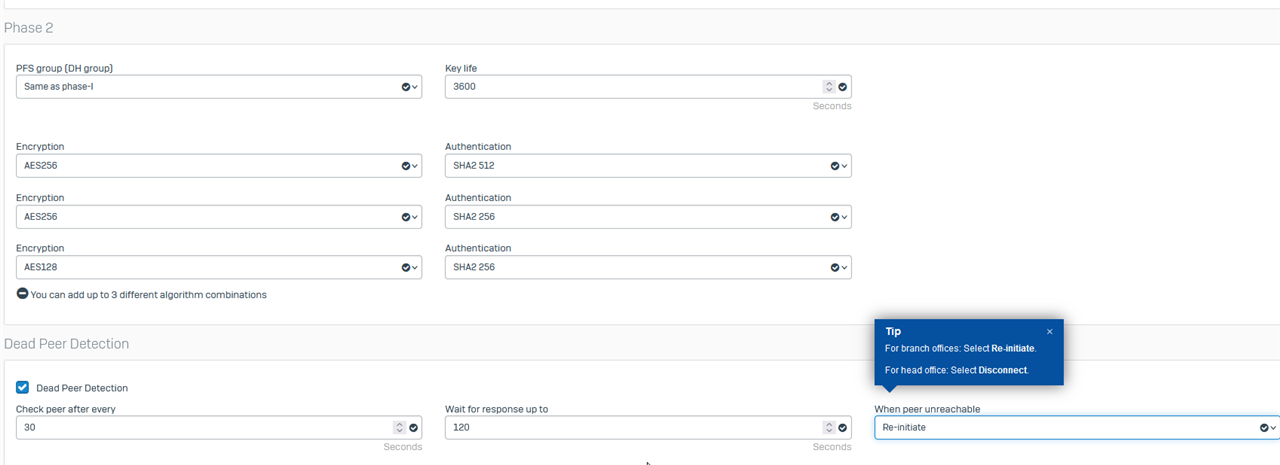
It's setup with following settings
Policy settings
This thread was automatically locked due to age.


