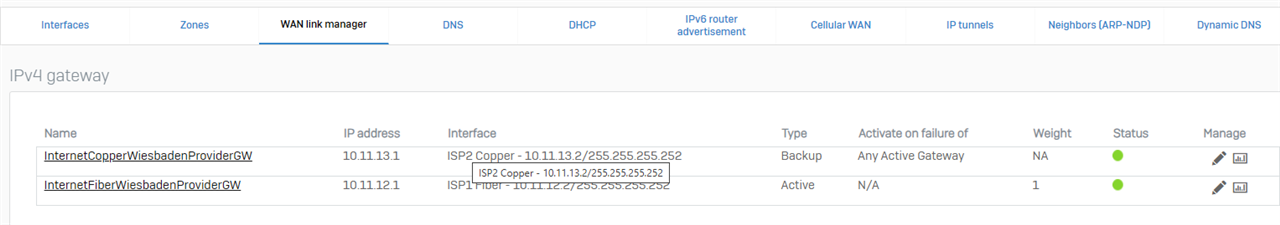
Customer is installing a new ISP connection but will have the old one for a while as they have WAF to an internal server, and DNS pointing to current ISP PIP.
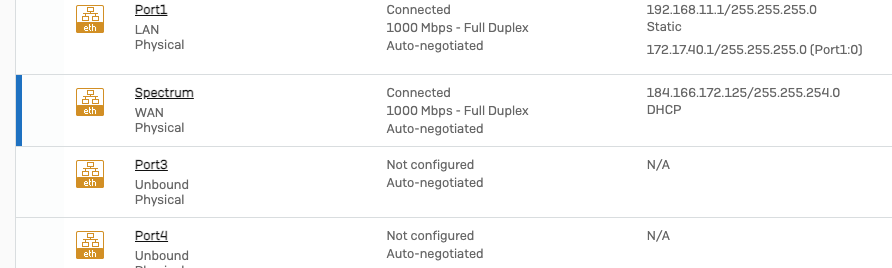
Left Port2 configured as it was. WAN zone, with static IP info.
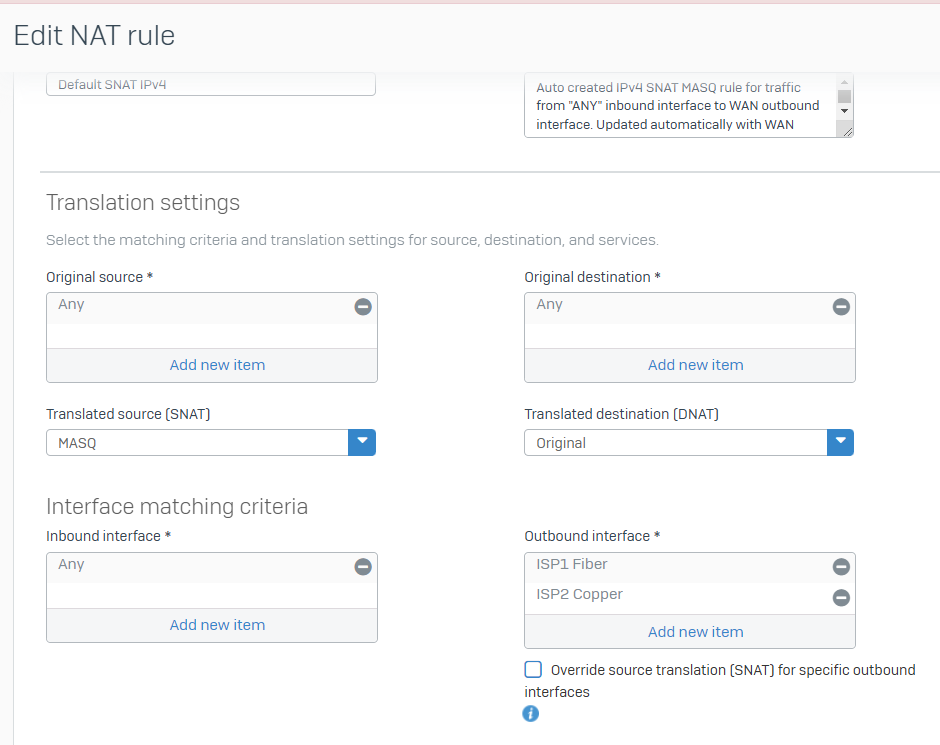
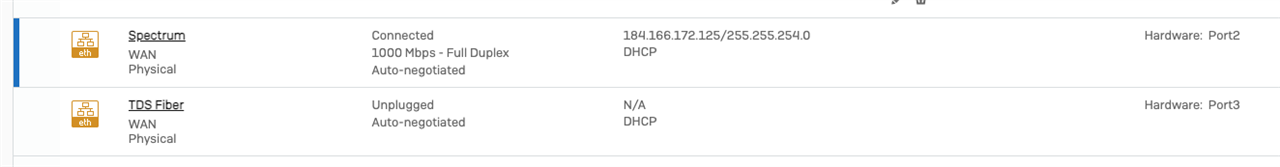
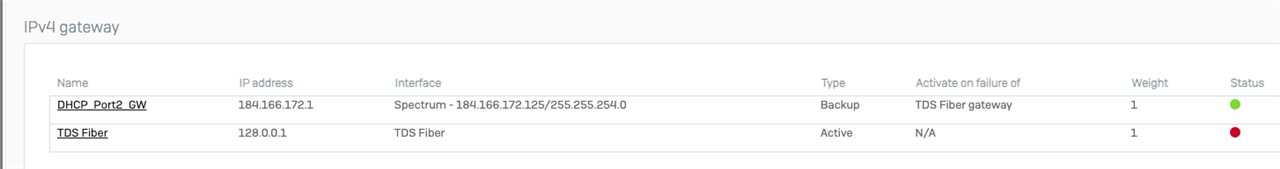
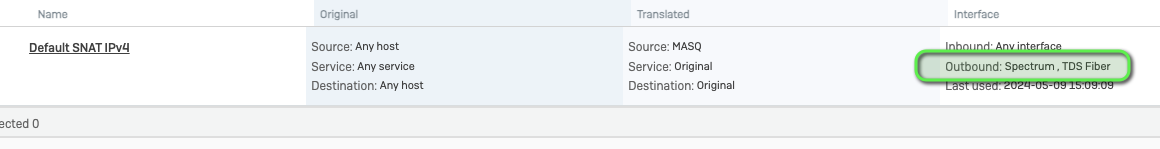
Configured Port3 to be the new ISP connection. Then the network went down. DNS didn't work. All kinds of strange. Checked the NAT policy as traffic is not going out the Internet and sure enough, Port2 was removed and Port3 added.
Seems like a bug to me. We've experienced this before but not consistently. Is this an issue anyone else has faced?
XGS116 on 19.5.3.
This thread was automatically locked due to age.