Hello all,
Network (kinda) and XGS newb is back with another question. I'm pretty sure the answer is going to be a "yes/no and you're just missing this little step to get it done". I've included a summarizing picture.
Presently working:
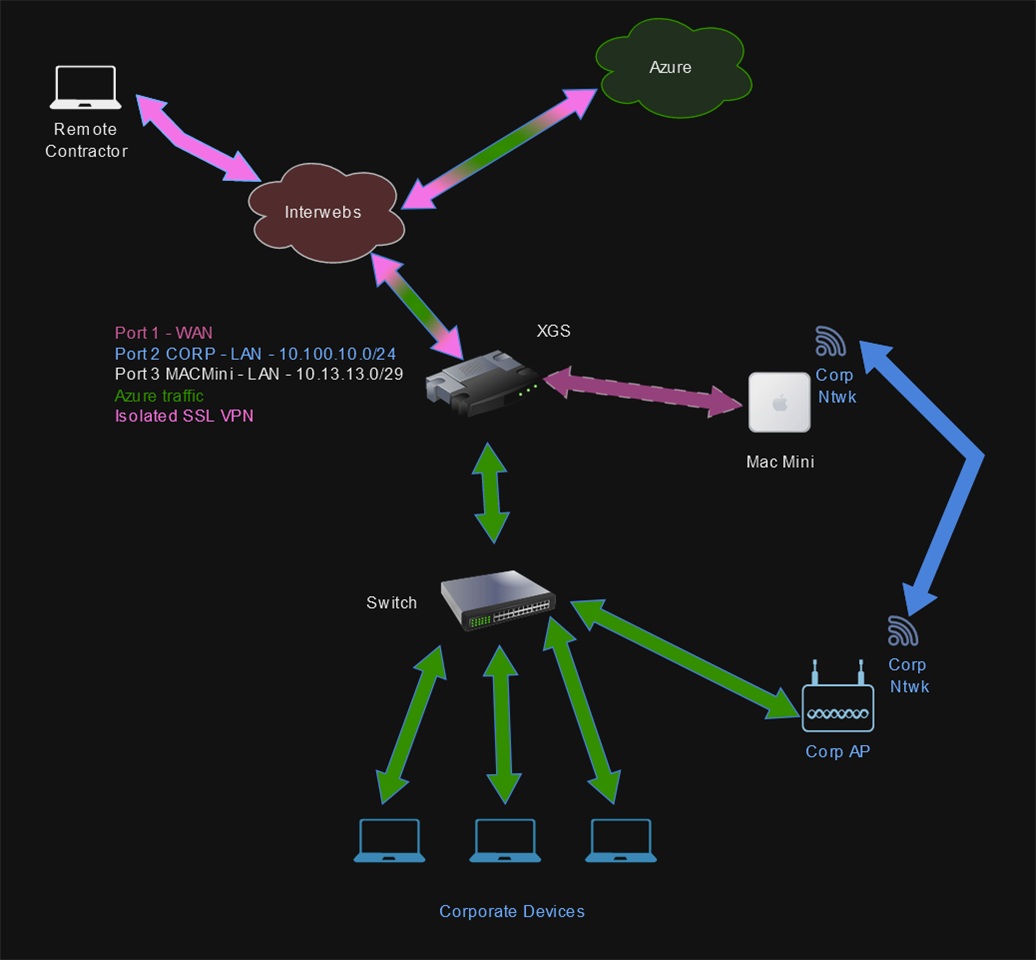
We have an IPSec tunnel setup to our Azure vnet, and anyone using SSL VPN to connect to it is in a full/default gateway policy. There are 2 such policies and remote contractors only have access to the Azure vnet, with nothing internal being accessible. Remote corporate users have access to both internal and Azure vnet.
Issue:
As we are going to be creating an iOS app and Apple requires an Apple device to create said application, we're looking to provide isolated access to a Mac Mini that already exists in our corp environment to an external contractor with an AVD we supplied. They are going to need access to both the existing and working Azure vnet (done) AND to the mentioned Mac Mini, without being able to access internal networks.
What I have done so far:
Created another LAN/Subnet 10.13.13.0/29 on Port 3 with an IP of 10.13.13.1 for the Port. On the Mac Mini I gave it a static Ethernet IP of 10.13.13.3, and connected it to Port 3 on the XGS. The Mac Mini also is connected to our corporate network via Wi-Fi.
I still need to make sure that the Mac Mini can get access to the Az vnets from the ethernet port (and I'm even a bigger newb with Macs - but was going to turn off the WiFi and see where I can get).
Q: How can I ensure my Sophos config is correct (while testing the above) and where to start looking trace log wise should the contractor's AVD and his SLL VPN access can not access Mac Mini and finally, once on the Mac Mini, he can't connect to the corp lan?
This thread was automatically locked due to age.


