in recent scanning, we received "SSH Terrapin Prefix Truncation Weakness (CVE-2023-48795)" vulnerability on port 22.
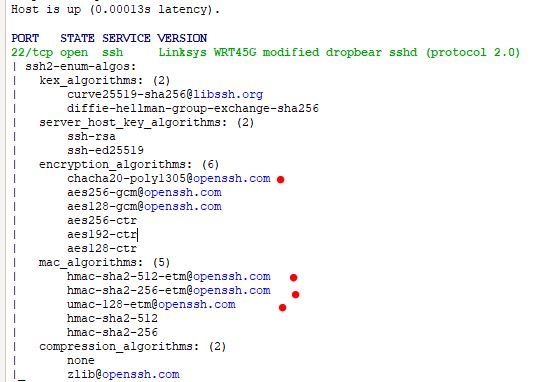
just use this command in nmap "nmap -sV -p 22 --script ssh2-enum-algos 192.168.xxx.xxx"
if it shows "chacha20-poly1305@openssh.com" or any this with "-etm" then it will enables the Terrapin Attack.
i had latest firmware version SFOS 20.0.0 GA-Build222.
will it get patch or need to do anything manually.
.
This thread was automatically locked due to age.

