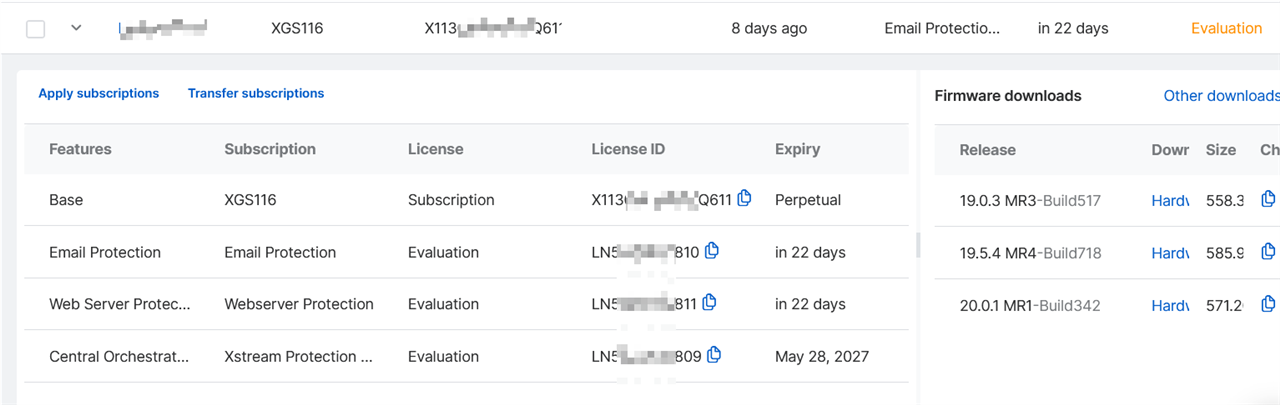
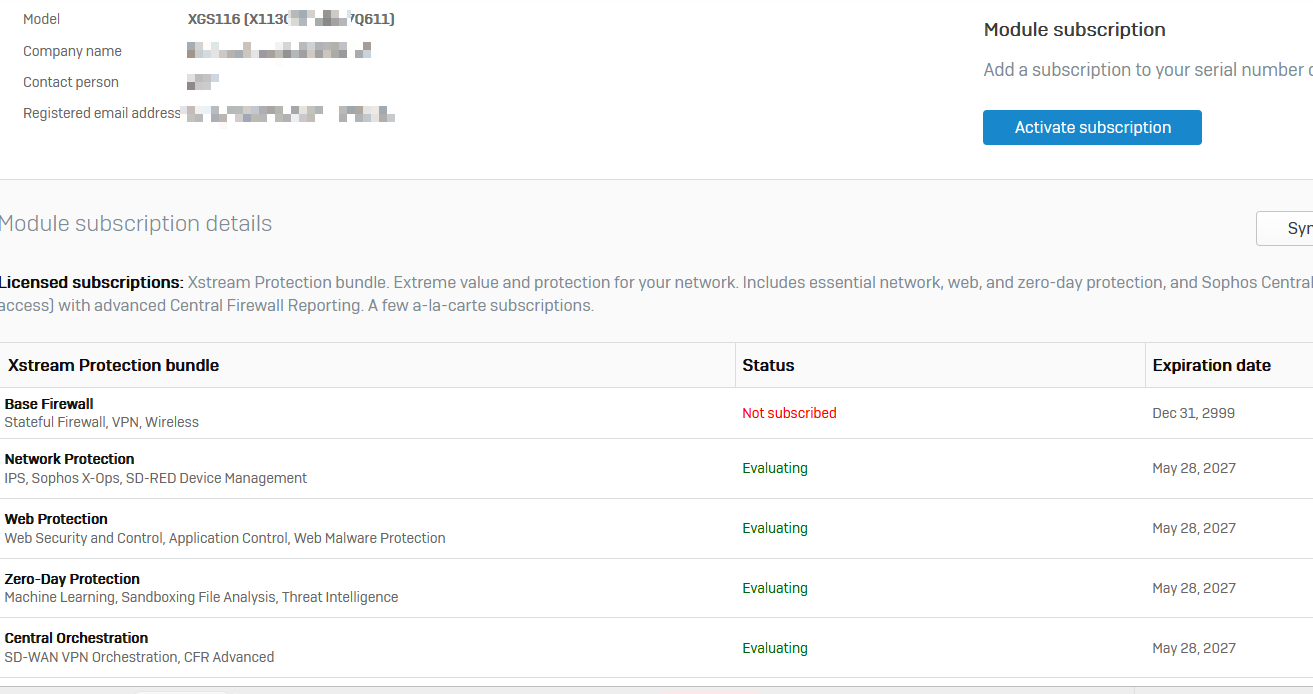
I am referring this post with similar issue
DNS request to DNS over Site2Site VPN
I have below setup
XG310 -- branch office
XG430 -HA -- Head office
Now I got
XGS2100 - 2nd branch office ( Gateway local ip: 172.16.1.100 )
XGS2100 - 3rd branch office
with XG310 I can reach Head office Active Directory with SNAT, but with XGS2100 I can't reach strange issue, but from Head office I can reach XGS2100
( was implemented based on article : https://support.sophos.com/support/s/article/KB-000035830?language=en_US ) 2 years before on XG310, same in XGS2100 not working )
console> show advanced-firewall Strict Policy : on FtpBounce Prevention : control Tcp Conn. Establishment Idle Timeout : 10800 UDP Timeout : 30 UDP Timeout Stream : 60 Fragmented Traffic Policy : allow Midstream Connection Pickup : off TCP Seq Checking : on TCP Window Scaling : on TCP Appropriate Byte Count : off TCP Selective Acknowledgements : on TCP Forward RTO-Recovery[F-RTO] : off TCP TIMESTAMPS : off Strict ICMP Tracking : off ICMP Error Message : allow Caching for route lookups : on IPv6 Unknown Extension Header : deny IPv6 Ready Logo Compliance : off WAN access control for web admin console : on Bypass Stateful Firewall ------------------------ Source Genmask Destination Genmask NAT policy for system originated traffic --------------------- Destination Network Destination Netmask Interface SNAT IP 192.168.1.33 255.255.255.255 172.16.1.100 192.168.1.66 255.255.255.255 172.16.1.100 192.168.1.77 255.255.255.255 172.16.1.100 ### from branch office 2nd Sophos Firmware Version: SFOS 20.0.0 GA-Build222 Model: XGS2100 Hostname: removed console> ping 192.168.1.33 PING 192.168.1.33 (192.168.1.33): 56 data bytes ping: sendto: Operation not permitted console>
console> system ipsec_route show tunnelname host/network netmask HO 192.168.1.0 255.255.255.0 HO_Backup 192.168.1.0 255.255.255.0 console> system route_precedence show Routing Precedence: 1. SD-WAN policy routes 2. VPN routes 3. Static routes
This thread was automatically locked due to age.