Does anyone have VLAN success with Sophos XG over Proxmox and a managed switch?
This thread was automatically locked due to age.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Yes, I have it in use with no problems in my home setup (with smart managed Netgear switches). What's your issue?
Managing several Sophos firewalls both at work and at some home locations, dedicated to continuously improve IT-security and feeling well helping others with their IT-security challenges.
Jeez, I just typed out the whole issue only to have it flagged for abuse.
I'll try without screenshots as I think its the link that flags it.
I'll add them if I can post this.
__________________________
Basically what I said was...
Awesome, I was beginning to lose hope!
Do you mind sharing your configurations?
I can't get it to work no matter what how-to guides I follow or ideas I try. Most people throw in the towel at this point I think and the documentation isn't very good for this use case. It seems like once people get the issue solved they disappear without showing setup. I was about to try ESXi after this before going a completely different route. I really like Sophos XG, once understood it's easy to use for how extensive it is. It's more like an AIO than other at-home solutions. I'm really hoping to get this sorted so I can keep using Sophos how I am.
My current setup is ISP > Intel-225V, SFF PC, Proxmox w/ Sophos XG VM, XG-C100C > Netgear MS510TXM > local net
I'll leave my setup alone for now until I hear from you. I want to focus on VLAN 211 for this.
Here are pics of my configs,
Proxmox Network devices:

Sophos VM config:

Sophos XG Network config:

Sophos DHCP for VLAN 211:

PVID config of switch:

mg2 is the nic of the device I want on 211, mg4 is the port to Sophos, everything else can be set to whatever is necessary.
Thank you
Don't create the VLAN interface at Proxmox.
Create the VLAN "211" at "Port1" on Sophos Firewall.
What's happening right now is that you created a VLAN (Sophos Firewall) inside another VLAN (Proxmox vmbr2 interface).
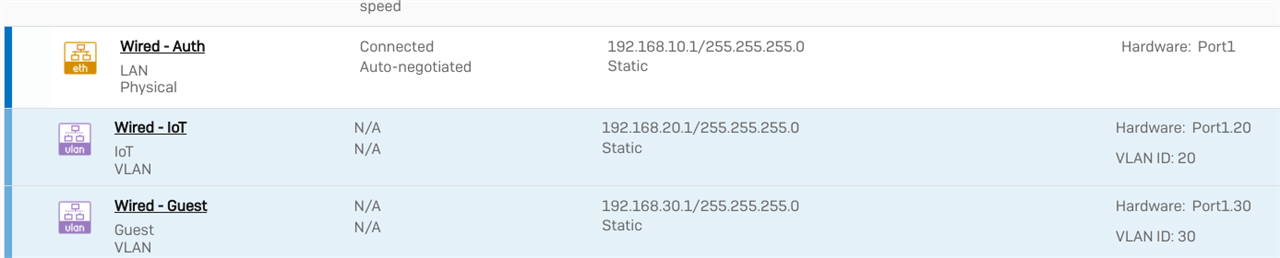
As an example: At Sophos Firewall I have two VLAN's, one for Guest and another for IoT at "vmbr0"
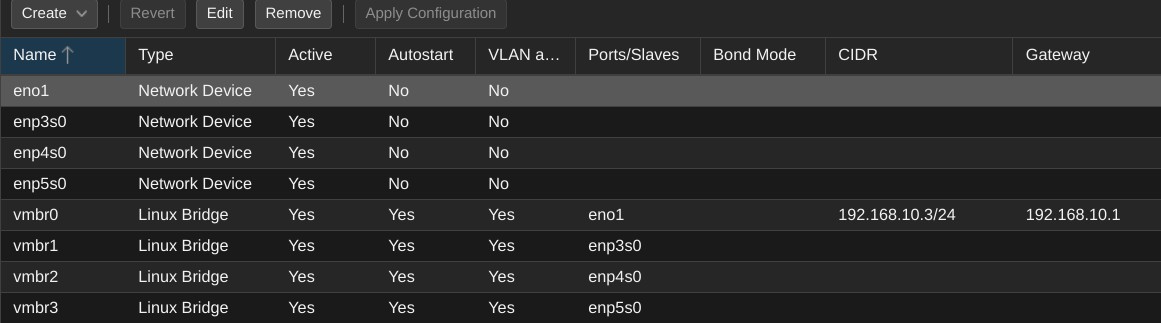
But on Proxmox I have them setup without any VLAN's, only as bridges for the physical interfaces.
vmbr0 = "Wired - Auth".
PS; Use the Interfaces at Proxmox as "Physical Interfaces"(Only create the necessary bridges to use on the VM), leave VLAN's and everything else on Sophos Firewall.
If a post solves your question use the 'Verify Answer' button.
Ryzen 5600U + I226-V (KVM) v21 EAP @ Home
Sophos ZTNA (KVM) @ Home
Thanks for clearing that up. I had been doing this in the beginning but I must be missing something still.
Here is my current setup.
New Proxmox:

New Sophos VM:


Sophos Ports/VLANs:

Sophos DHCP:

Can you double check on my VM setup that the Network Devices are the same setup as yours?
If this all looks good then perhaps I have the switch to deal with.
Thanks for clearing that up. I had been doing this in the beginning but I must be missing something still.
Here is my current setup.
New Proxmox:

New Sophos VM:


Sophos Ports/VLANs:

Sophos DHCP:

Can you double check on my VM setup that the Network Devices are the same setup as yours?
If this all looks good then perhaps I have the switch to deal with.
This looks ok at first sight, however in the switch screenshot I don't see VLAN 117 but it is in Sophos. So VLAN 117 might not work in the rest of your network.
PS, if you do want to work with VLAN interfaces in Proxmox like you did before, then you create alle the necessary interfaces in Proxmox and just add every interface as an additional NIC in the Firewall VM. In that case you don't have any VLANs in XG but you have every network on a separate NIC.
Managing several Sophos firewalls both at work and at some home locations, dedicated to continuously improve IT-security and feeling well helping others with their IT-security challenges.
Prism apijnappels Thanks both of you, The proper way is to set up VLANs in Sophos only and leave Proxmox out of it. I attempted to use VLANs in Proxmox because of all the videos on Proxmox VLANs. Unfortunately, when Proxmox creates the new interface, Sophos sees it as a physical interface. Which makes sense because Sophos is a VM, but it does not know that, so any NICs attached to the VM config will be recognized as physical. Now I'm not positive because I didn't spend a bunch of time with different configurations troubleshooting the Proxmox VLANs, but I think that what happens is Sophos strips the tag because it thinks the NIC is physical. Even setting up a VLAN on the "pysical" VLAN didn't do much. Maybe there is a way to get that to work but this setup is simplified and the way I would like it to be. Here's how it is set up...
Proxmox:

Sophos VM in Proxmox:

Sophos Ports (WAN not displayed) and VLANs:

DHCP Servers:

A communication rule:

I change 211 to WiFi so here's the corresponding rule:

Switch PVID configuration:

Now the switch config was really the most difficult to understand. I found that I must not tag a port with a PVID and VLAN Member. How I understand it is that VLAN tags are exclusive to ports that traffic is intended to pass through with multiple VLANs for a specific PVID. For example, VLAN 117 is tagged on mg4 (the port to the router, PVID 1) and untagged on xmg6 which requires the PVID of 117. For some reason, if I tag xmg6 with 117 I have local network access but lose internet access.
This has been probably one of the coolest things I've done lately thanks to you guys for helping me understand how this stuff works.