I have to seperate two networks using the same LAN Interface running XG in natest version with 1 phyiscal NIC bound to LAN and 1 physical nic bound to wan. The need is that there is no access form Private Network IPs to Company Network IPs and Vice Versa. Both LAN IP Ranges using the same physical network.
Private LAN: 192.168.1.0/24, Gateway: 192.168.1.5
Company HomeOffice LAN: 192.168.55.0/24
Company HomeOffice Lan Computers are allowed and should to use the Gateway 192.168.1.5
I tried to configure a separate IP Range:
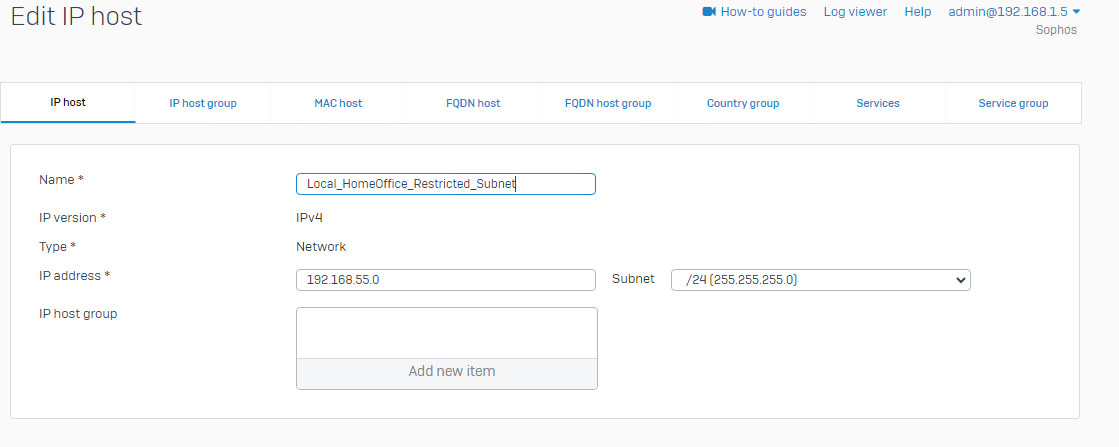
And in the Firewall Rules I created a Rule
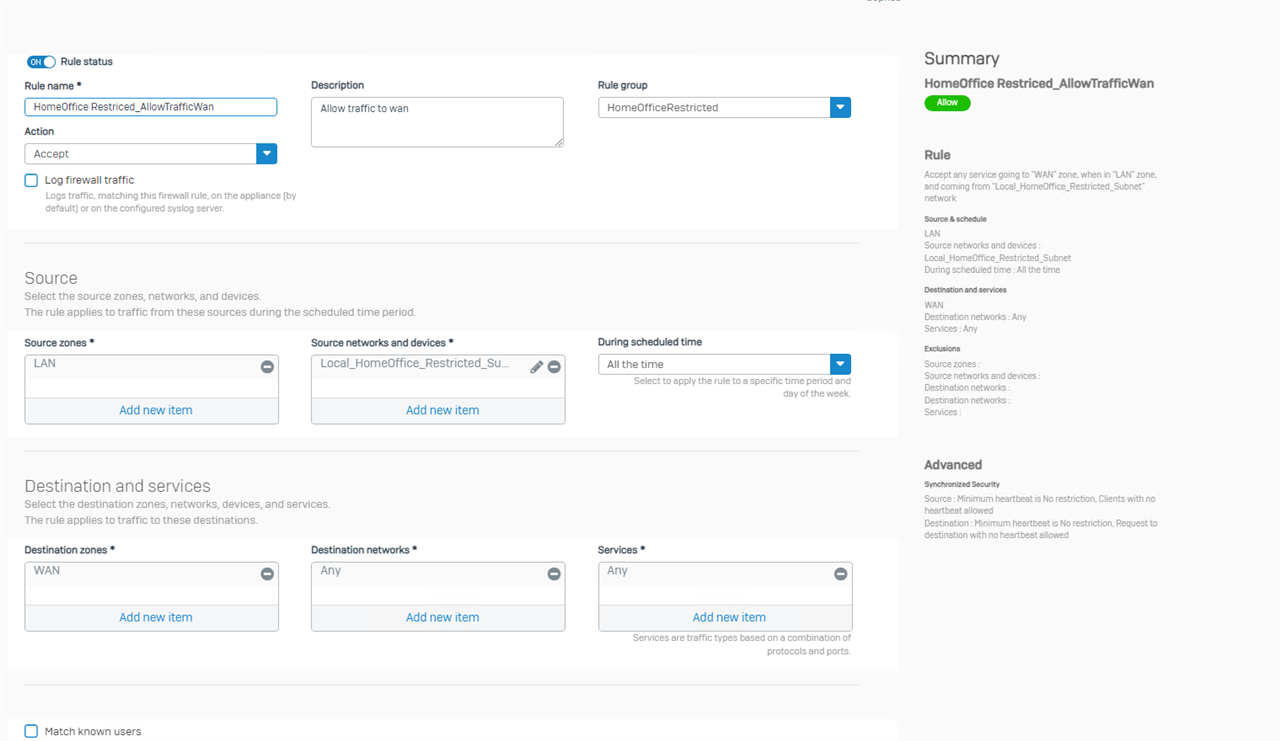
When assinging a IP Address 192.168.55.2 there is no connection to Internet possible with Gateway 192.168.1.5
What addtional rule do I need?
Is there some routing required and how?
This thread was automatically locked due to age.


