We will have a special deployment at one customer soon.
The customer has serveral branch offices where Sophos XGS 136 will be the local gateway for 5-6 subnets for each branch office.
The BO firewalls will only have base subscriptions and only some firewall rules for local subnet-rules like "https allowed from LAN to DMZ".
In the head office there is an XGS HA cluster (XGS3100) which will be the central internet breakout for all BOs and the HO.
The BO firewalls will be connected through route-based VPNs to the HO and will have no local internet breakout (device traffic should pass the HO firewall, too). At first they will theoretically have a local WAN interface but in a few months the BO's WAN connections will be changed to MPLS connections with no direct internet connection.
Today we have one older XG firewall that is already completely tunneled to the HO (policy-based, since it is a Sophos SG UTM) but I wonder if my configuration is "best practice" for a SFOS firewall behind another firewall.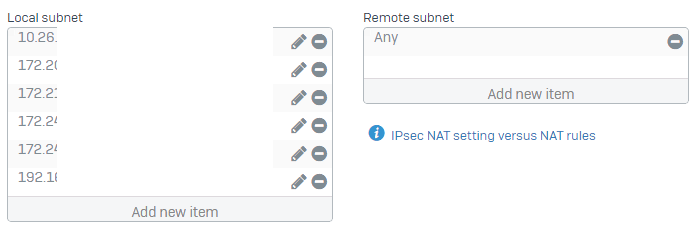
To make anything of the firewall itself working I had to create a NAT policy for system originated traffic, first I was hoping, that this firewall would use it's WAN interface for that but - with an "ANY" on the other side of a VPN-tunnel this doesn't seem to be true.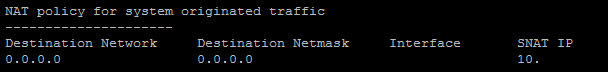
SNAT IP is the firewall's IP on the LAN zone. DNS server for the BO firewall is the HO firewall.
Anything else I should look for or take into planning?
I know that the lack of network protection in the BOs could be a bit of an issue.
This thread was automatically locked due to age.
