XG550 (SFOS 19.0.2 MR-2-Build472)
This is specially directed to Sophos:
Hello SOPHOS,
i tried to import a Sophos XG created TOTP into Sophos UTM which is handling reverse proxy functionality with reverse auth including totp (because sophos xg is not able to do totp with reverse auth o.O )
I tried to import the token but UTM is sayin:
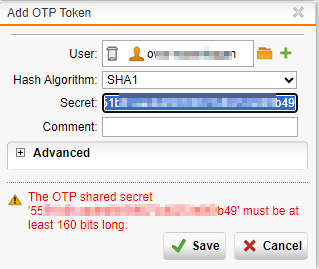
Why there is no chance to change hash algorithm in XG?
Why the created TOTP tokens are that "weak"?
I am tired making comparison to utm but why is utm supporting SHA1, SHA256 and even SHA512 algorithmns for OTP and the NEWER, BETTER, MORE SECURE, undiscontinued product SOPHOS XG can not even handle this basic thing????
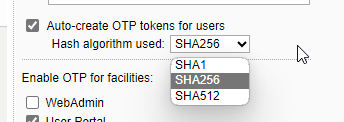
Please give me an explanation...
Kind regards,
Nafets
This thread was automatically locked due to age.


