Hi everyone,
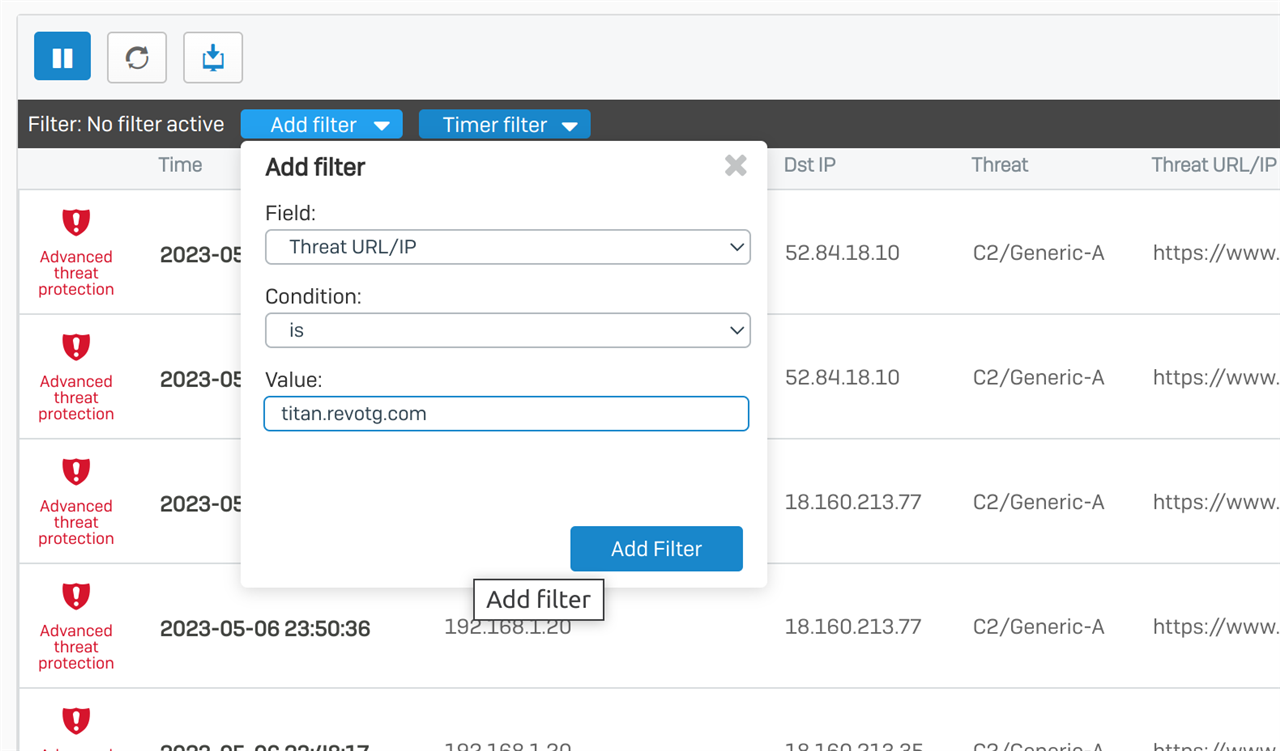
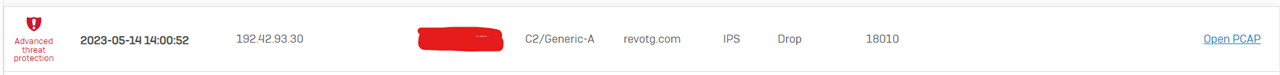
So like a lot of others here I've experienced where we get the notification that an attempt to communicate with a botnet or command and control server has been detected.
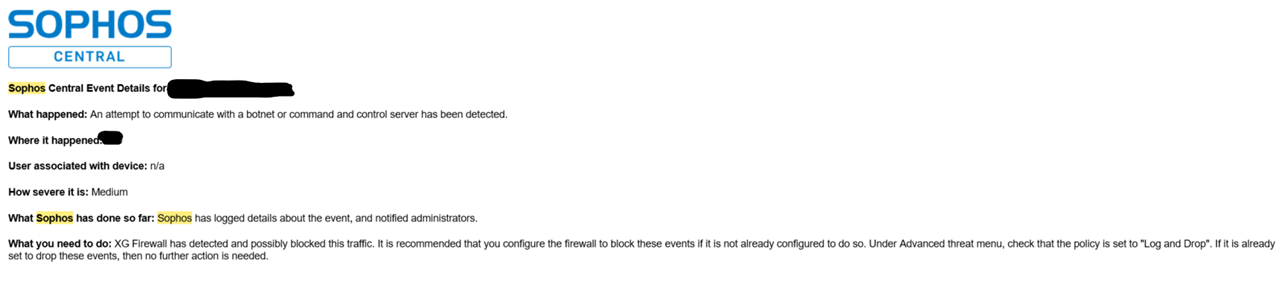
And its always these same three sites:
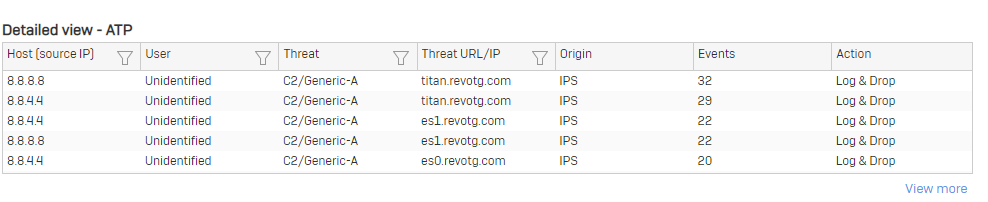
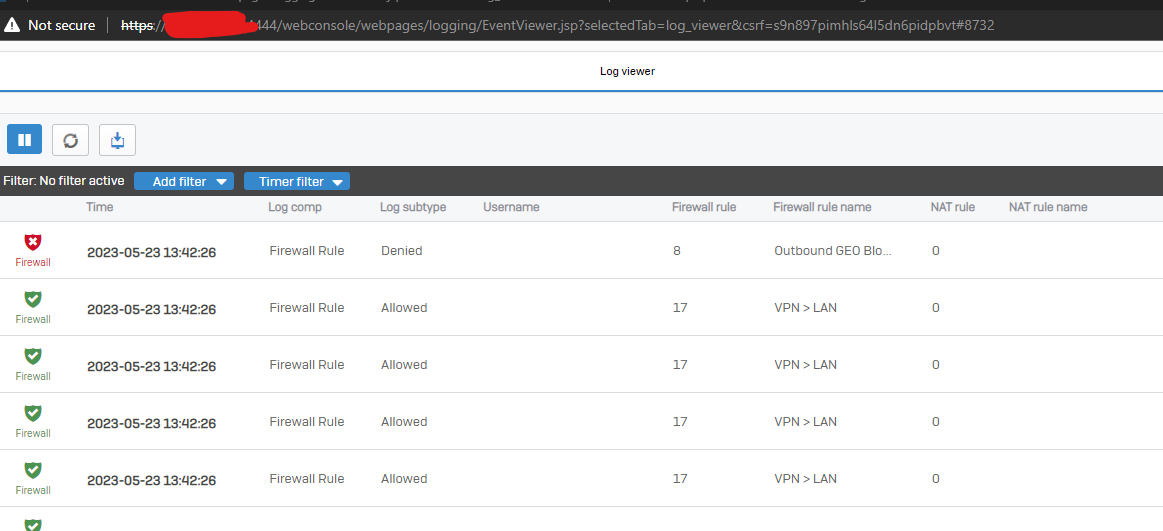
As you can see it's pinging our DNS provider (in this case Google) but also pings our DNS server (which is also our DC).
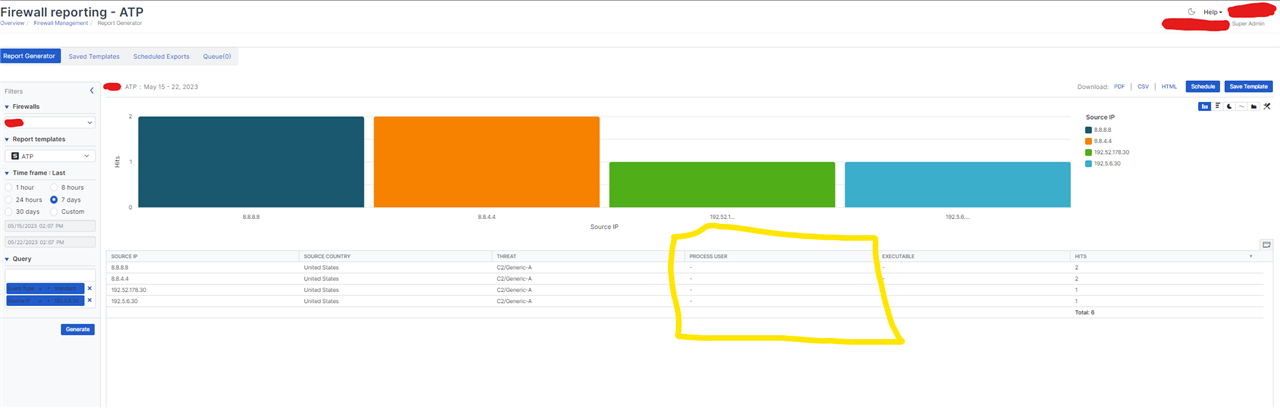
In checking out the site the only vendor that sees it was malicious is Sophos:
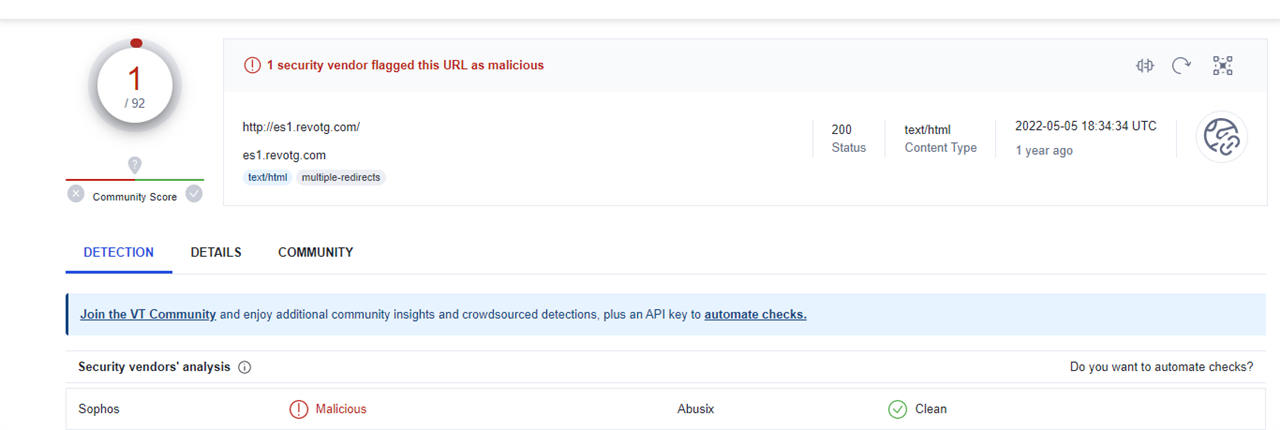
And checking Abuse IPDB doesn't pull up anything either:
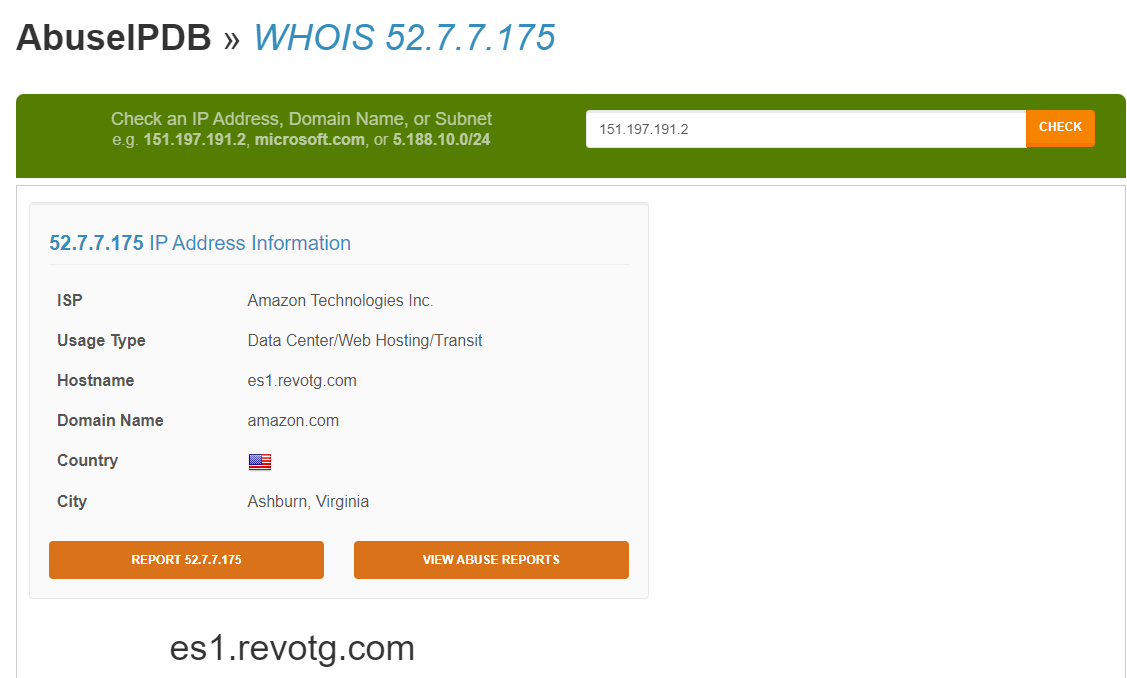
When I open the site in a VM this is what I get:
So do you think that enabling deep scans for the server, and IPS would help with this situation? I'm just puzzled as to what's requesting this site on my network.
This thread was automatically locked due to age.