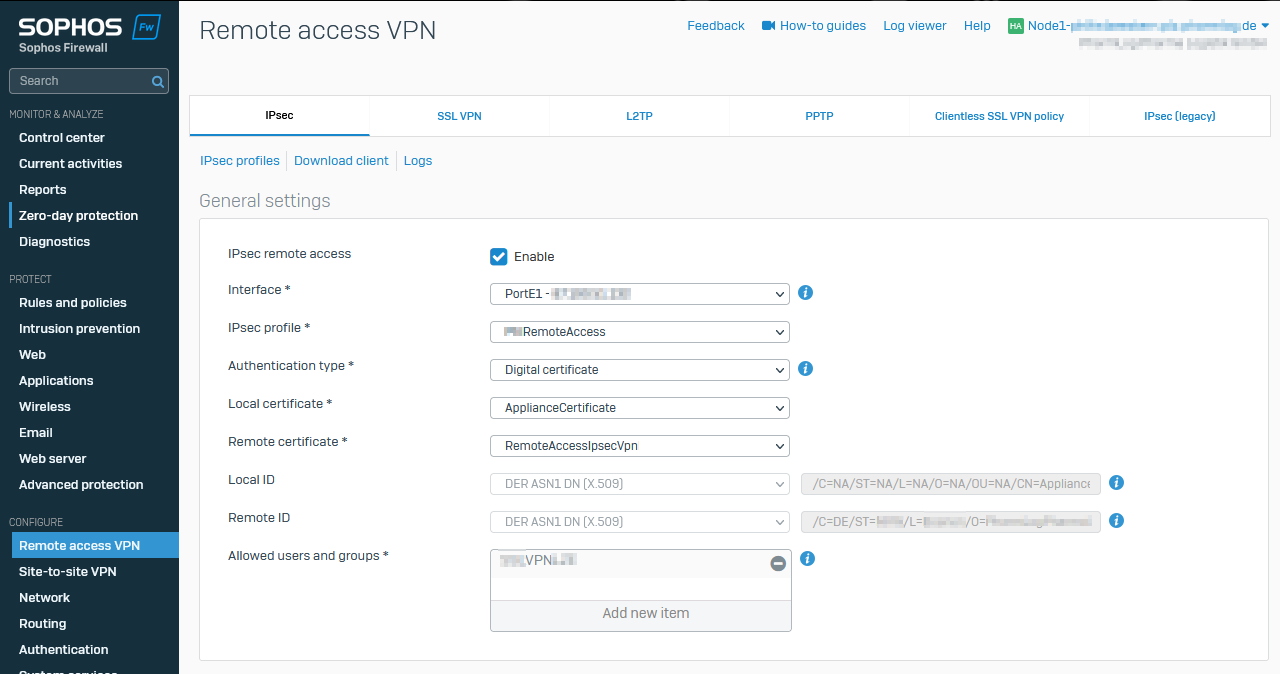
Remote Access VPN IPSEC with Authentication type certificate does still lead to invalid connection .scx file on SFOS 19.5.0 GA-Build197, SFOS 19.5.1 MR-1-Build278 and SFOS 19.5.2 MR-2-Build624 if the "Organization name" in the Certificate does contain Whitespaces.
There are some Bug Reports like NC-85383 and NC-95633 whitch are listed as "resoled issues" at the release notes: https://docs.sophos.com/releasenotes/index.html?productGroupID=nsg&productID=xg&versionID=19.5
Looks like the same Problem is reported for older Firmware Versions: IPSEC Remote Access .scx file invalid
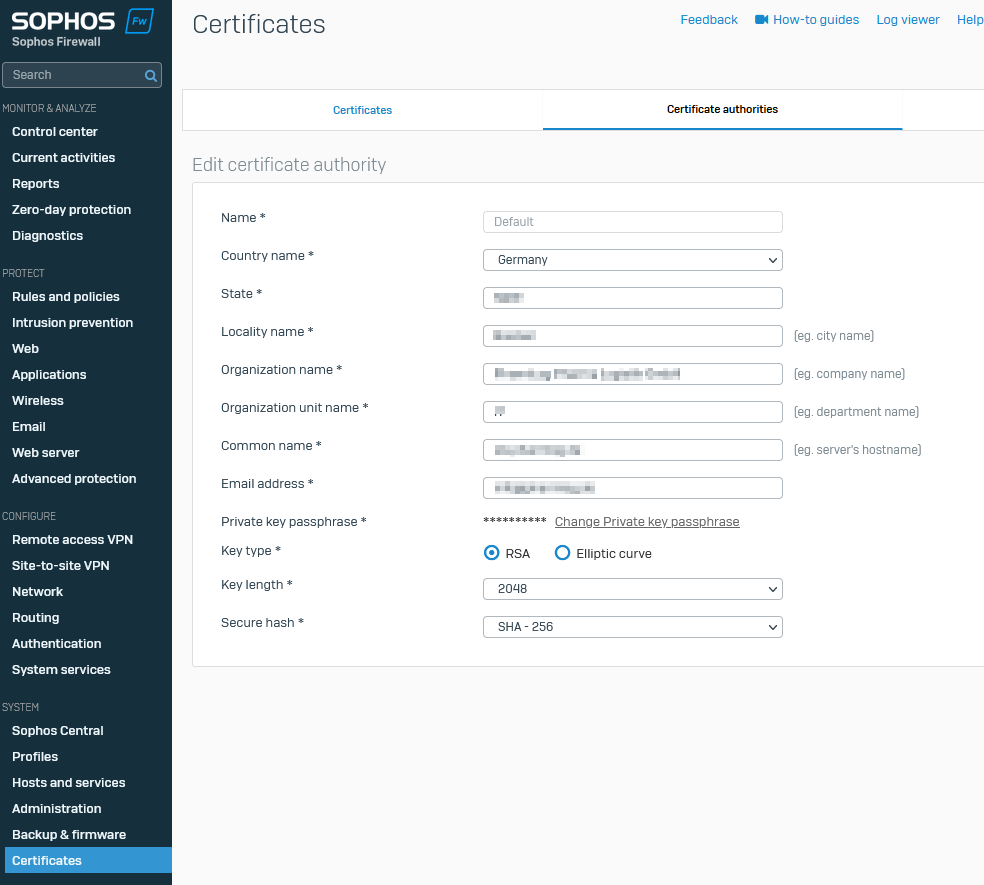
CA Settings
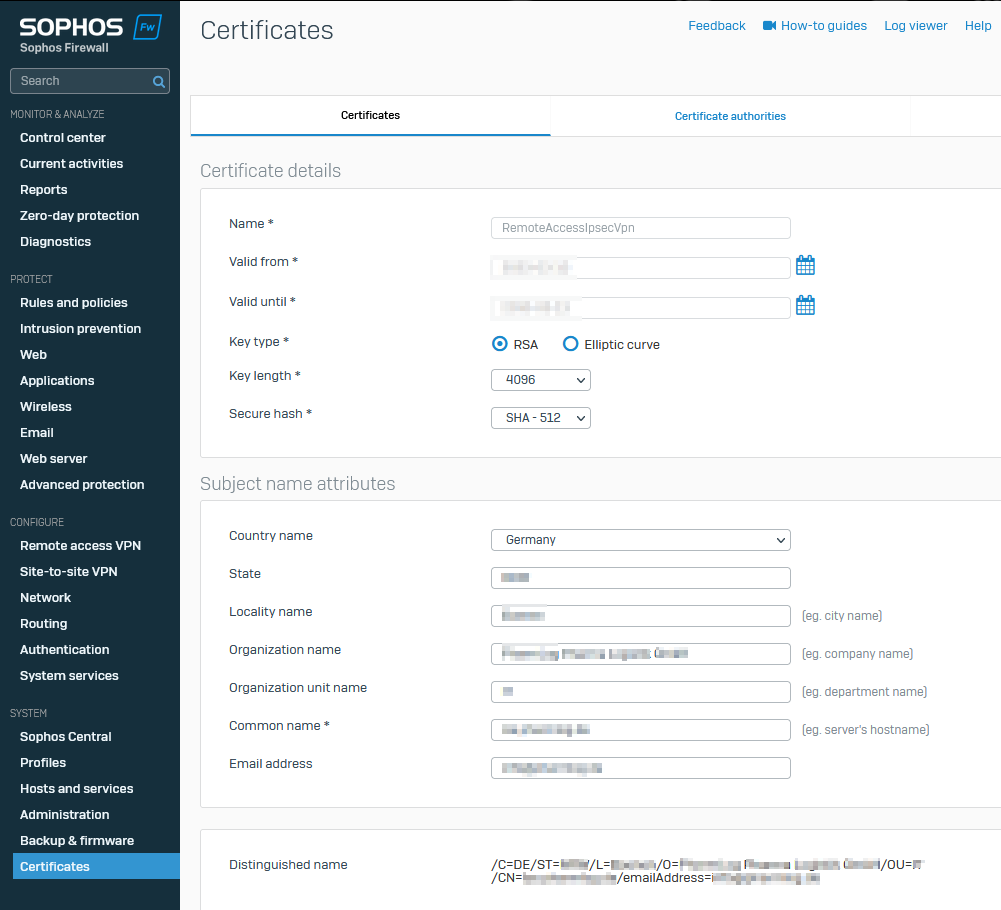
No "German" Umlaute / "Special" Characters but Whitespaces in Company Name Organization Name.
Certificate Settings
Content of xxx.scx:
cannot open file /tmp/root_cert.txt at /scripts/vpn/ipsec/generateJSONVPNClientConf.pl line 331.
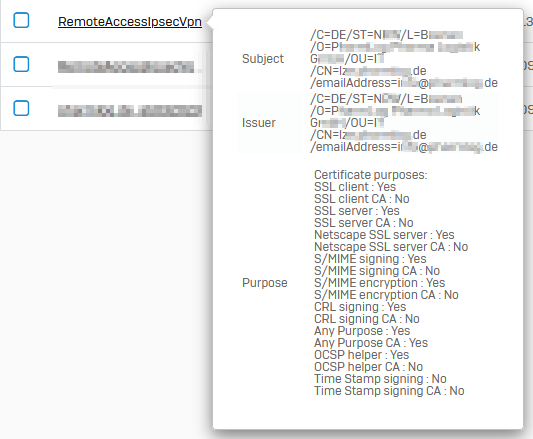
Distinguished name:
/C=DE/ST=NRW/L=City/O=The Example GmbH/OU=IT/emailAddress=info@example.com
Update
It does still happen on 19.5-MR2.
This thread was automatically locked due to age.