Hello Sophos Community
Using the latest firmware as of today (SFOS 19.5.0 GA-Build197) on Sophos Firewall, installed as a virtual appliance in Proxmox 7.3-4. It's a home license, on 4 virtual CPUs (host), and 6GB memory. I'm using the official qcow2 images.
I am hosting a Wordpress blog behind it, using WAF, which I use mainly for sharing family pictures and videos. Below is a screenshot of the policy.
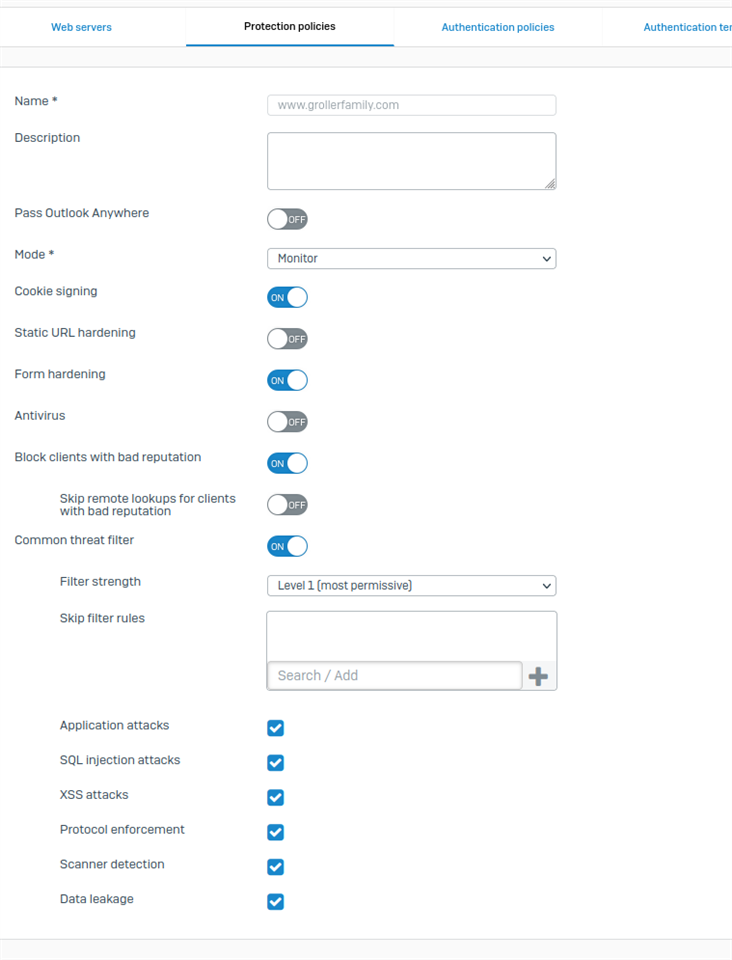
When this policy is applied to the firewall rule, everything works fine until I attempt to upload a very large file to the blog. Recently, I attempted to upload our family's Christmas morning video to my site, which was 1.3GB. Not only did it fail, but the entire firewall crashed... and crashed hard. The house went offline, DNS resolution went down, I couldn't connect to the firewall via the IP address, nothing. It just died. I had to go into Proxmox, kill the VM, then restart it. Upon restart everything was fine.
If I remove the WAF policy, the file uploads. If I enable the WAF policy and transfer the file, everything comes crashing down. It's a very easily reproduced. What could be causing this?
This thread was automatically locked due to age.


