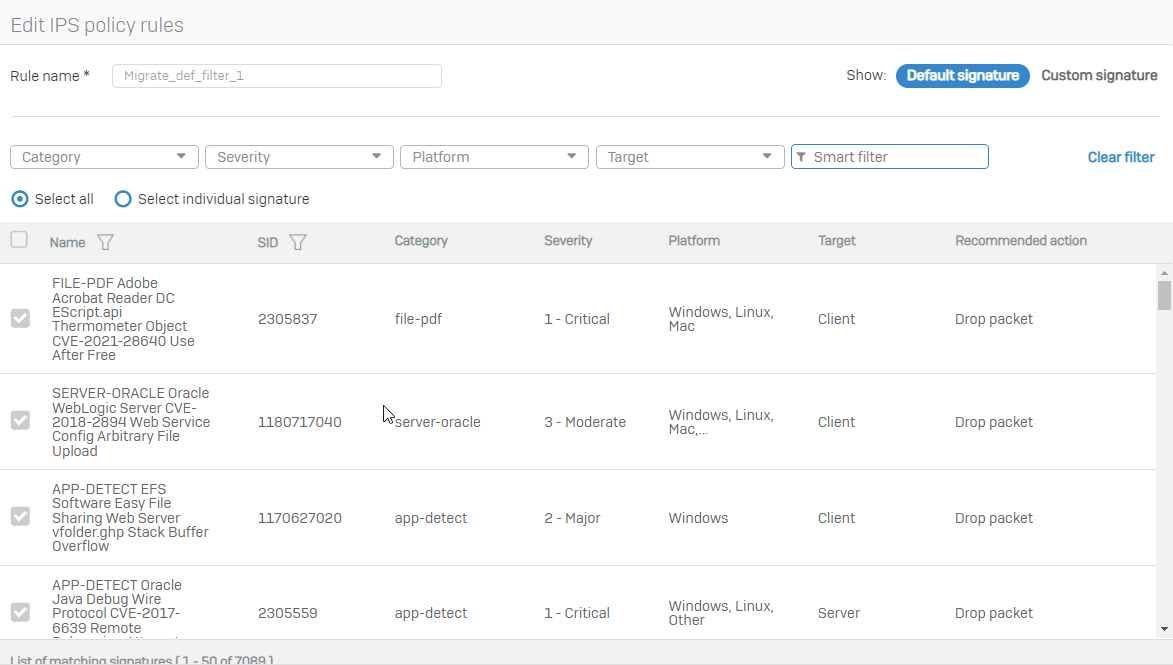
There is a critical 0-Day exploit for Exchange already being exploited, which is pretty much the same as the "ProxyShell" vulnerability in March.
How can I check if the mitigation is already working with Snort or IPS rules?
There is also written (see "Temporary containment measures") how to create a rewrite rule to address the vulnerability, until a patch becomes available.
This thread was automatically locked due to age.