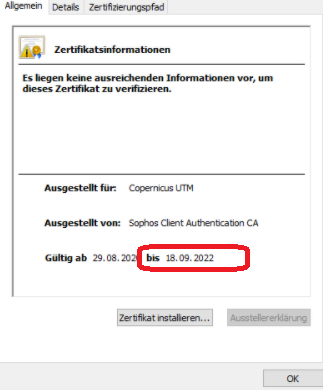
The CAA certificate on our XG 18.5 MR4 has expired without any warning. Nice!
So all our clients with CAA cannot authenticate against that firewall.
How would Sophos resolve that issue withour recreating the ApplicanceCertificate?
C:\OpenSSL-Win64\bin> openssl s_client -connect 1.2.3.4:9922
CONNECTED(00000154)
Can't use SSL_get_servername
depth=0 C = DE, ST = BW, L = Karlsruhe, O = Sophos, OU = NSG, CN = Copernicus UTM, emailAddress = no@email.com
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = DE, ST = BW, L = Karlsruhe, O = Sophos, OU = NSG, CN = Copernicus UTM, emailAddress = no@email.com
verify error:num=21:unable to verify the first certificate
verify return:1
depth=0 C = DE, ST = BW, L = Karlsruhe, O = Sophos, OU = NSG, CN = Copernicus UTM, emailAddress = no@email.com
verify error:num=10:certificate has expired
notAfter=Sep 18 05:42:24 2022 GMT
verify return:1
depth=0 C = DE, ST = BW, L = Karlsruhe, O = Sophos, OU = NSG, CN = Copernicus UTM, emailAddress = no@email.com
notAfter=Sep 18 05:42:24 2022 GMT
verify return:1
---
Certificate chain
0 s:C = DE, ST = BW, L = Karlsruhe, O = Sophos, OU = NSG, CN = Copernicus UTM, emailAddress = no@email.com
i:C = DE, ST = BW, L = Karlsruhe, O = Sophos, OU = NSG, CN = Sophos Client Authentication CA, emailAddress = no@email.com
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIEzzCCA7egAwIBAgIBADANBgkqhkiG9w0BAQsFADCBlDELMAkGA1UEBhMCREUx
CzAJBgNVBAgMAkJXMRIwEAYDVQQHDAlLYXJsc3J1aGUxDzANBgNVBAoMBlNvcGhv
czEMMAoGA1UECwwDTlNHMSgwJgYDVQQDDB9Tb3Bob3MgQ2xpZW50IEF1dGhlbnRp
Y2F0aW9uIENBMRswGQYJKoZIhvcNAQkBFgxub0BlbWFpbC5jb20wHhcNMjAwODI5
MDU0MjI0WhcNMjIwOTE4MDU0MjI0WjCBgzELMAkGA1UEBhMCREUxCzAJBgNVBAgM
AkJXMRIwEAYDVQQHDAlLYXJsc3J1aGUxDzANBgNVBAoMBlNvcGhvczEMMAoGA1UE
CwwDTlNHMRcwFQYDVQQDDA5Db3Blcm5pY3VzIFVUTTEbMBkGCSqGSIb3DQEJARYM
bm9AZW1haWwuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA6eSq
ugp4yQNBBMPyev/POVPYVUJ9LmFPVEFt+vlQ2TNBF6ZVLIPtbx0HwTjTC/Hv5gGn
+QWtGt6tez45jMG00Jbljs4j2S65zD1Af4UxzRlyd8fiZz6P2Fj3U4x+xRJED7Jp
pyRdzgX6RQ5WajOIwtmOiP6HR8NLlTO82mTL06rNrLOnuKb8oWRYrPFcRfah/e98
VYPccooU3o7v0eiZD/UCK2cREoRMzczxLtXLEWdzZBkcTuGWochXZ2ASm6xlkrWA
Gcv3aQwlpDw7HSWI6kHKTWSEvLhSMExWOjAhxBqepf2tgxd5KOhxasat9LKpG59p
L8aqmFxhpJX6JckJsQIDAQABo4IBOTCCATUwCQYDVR0TBAIwADAsBglghkgBhvhC
AQ0EHxYdT3BlblNTTCBHZW5lcmF0ZWQgQ2VydGlmaWNhdGUwHQYDVR0OBBYEFJP9
dCr5ErN+fUTHrn0mlj4P1hM4MIHJBgNVHSMEgcEwgb6AFIJx3GzaIQRZRJjE+Dt5
P3A7wzoLoYGapIGXMIGUMQswCQYDVQQGEwJERTELMAkGA1UECAwCQlcxEjAQBgNV
BAcMCUthcmxzcnVoZTEPMA0GA1UECgwGU29waG9zMQwwCgYDVQQLDANOU0cxKDAm
BgNVBAMMH1NvcGhvcyBDbGllbnQgQXV0aGVudGljYXRpb24gQ0ExGzAZBgkqhkiG
9w0BCQEWDG5vQGVtYWlsLmNvbYIJAIlfkI0Hk3OmMA8GA1UdEQQIMAaHBAECAwQw
DQYJKoZIhvcNAQELBQADggEBAChJMFKBCcDUkKKJCQsQ11K9yQ9uOa8OZUTe+0dF
22fALTNiDGcCqfoUTmEw5sKcq9D9Xt65JY4YifwTKVsRokJRXAOzl6X7SViCAHvJ
Mcp/GPpsHedSmjGmr2FvOjJDAxIUIcsckrDVRvQkGRa5Vv80jUFoJ+fWS2+zP4o7
ASIYCC+6pSP9YvQWOFaKf7bakKIh92G4RCDtA4G8uPGG5X/aWeRqibBuqIWW2xQr
EmUSLHkMoygxtkZxC1sSBHSL8hdpksHQgRr8LZdNdR8T/EYln7w4Ah+FjhJi7DN7
sffDMB5c+AtxGfCkULdJ7opq+UnjywdcFEkGhxTmfwA0n7c=
-----END CERTIFICATE-----
subject=C = DE, ST = BW, L = Karlsruhe, O = Sophos, OU = NSG, CN = Copernicus UTM, emailAddress = no@email.com
issuer=C = DE, ST = BW, L = Karlsruhe, O = Sophos, OU = NSG, CN = Sophos Client Authentication CA, emailAddress = no@email.com
---
No client certificate CA names sent
Peer signing digest: SHA512
Peer signature type: RSA
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 1889 bytes and written 419 bytes
Verification error: certificate has expired
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: BBE7B50D73AC4CE827DE7F159B0F6A062BAAC6017497FA16D81AC048FBE1EABD
Session-ID-ctx:
Master-Key: BE91C30D405AE4494C3B150A087859A941597B46BFCFF74C1FE171205840D56CA58904909767340BC04F59551660380E
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - ae 11 78 4a 2a db 57 32-5e a7 12 1b a1 c9 40 35 ..xJ*.W2^.....@5
0010 - 25 ff f7 c9 9c e8 ab a0-6b 51 7a 60 7f e9 82 ec %.......kQz`....
0020 - 76 30 ee 74 7d 54 b2 2d-fe 8d ac ac 07 f2 da 0f v0.t}T.-........
0030 - 2c 3c b0 58 a3 c8 ad 24-1c 49 5b ec d5 44 1a 98 ,<.X...$.I[..D..
0040 - 73 ce 34 25 58 fb 0d 43-cf 1d 44 3b cd 00 16 56 s.4%X..C..D;...V
0050 - 57 8f f8 a0 5b ee 2b f5-7a dc b6 9a 6a fd 10 3e W...[.+.z...j..>
0060 - c6 3f 51 c8 e3 af ad 29-32 40 b3 f0 fb e1 28 ef .?Q....)2@....(.
0070 - fa de 80 27 af a1 e2 81-6d e8 69 4e c1 13 48 93 ...'....m.iN..H.
0080 - e0 f5 54 fd 67 cb ea ce-1c 32 f3 b7 77 88 b9 fd ..T.g....2..w...
0090 - 5e a6 32 0e 01 19 d7 f8-30 33 fa 06 86 3e ea ee ^.2.....03...>..
Start Time: 1663571691
Timeout : 7200 (sec)
Verify return code: 10 (certificate has expired)
Extended master secret: no
---
XG430_WP02_SFOS 18.5.4 MR-4-Build418# ls -lah /conf/certificate/internalcas/*
-rwxr-xr-x 1 root 0 1.2K Aug 29 2020 /conf/certificate/internalcas/ClientAuthentication_CA.der
-rw------- 1 root 0 1.7K Aug 24 2018 /conf/certificate/internalcas/ClientAuthentication_CA.key
-rwxr-xr-x 1 root 0 1.6K Aug 24 2018 /conf/certificate/internalcas/ClientAuthentication_CA.pem
-rwxr-xr-x 1 root 0 11.4K Jan 8 2022 /conf/certificate/internalcas/cloud-ca.crt
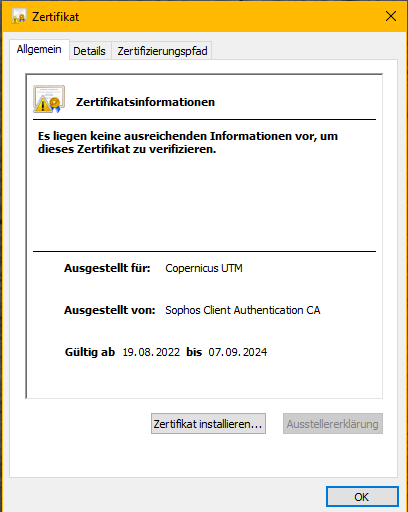
Edit: just found out, the CAA cert on XG has been renewed but probably the Auth Server still uses the old one and just need to be restarted.
thats the new one:
XG430_WP02_SFOS 18.5.4 MR-4-Build418# ls -lah /conf/certificate/internalcerts/*Auth*
-rw------- 1 root 0 1.6K Aug 19 00:00 /conf/certificate/internalcerts/ClientAuthentication_cert.key
-rwxr-xr-x 1 root 0 1.7K Aug 19 00:00 /conf/certificate/internalcerts/ClientAuthentication_cert.pem
This thread was automatically locked due to age.
