Hi,
I've rolled out many UTMs in the past and now starting to replace them with XGS, v19.
Pretty much makes sense but im puzzled by the firewall rules and how they are executed.
Here's one example that I dont get
I have simple LAN - 192.168.1.X that has Netgear wifi broadcasters attached to them.
I needed to create a guest network on those wifi broadcasters so created that with a VLAN, ID20, IP 192.168.100.x. Zone is LAN
Setup on the XGS the stuff required so Vlan interface, DHCP for vlan, etc etc.
The firewall rule is

All working fine, users are on guest, got internet, no problem. I can see clearly from the DHCP pool table that the guests are getting IP addresses for that Vlan segment.
However, as you see from the rule 0 B and 0 B for in and out.
I now wonder if the phones are just falling over to 4g because I look at the firewall logs and all I see is denies for anything from that network going out to the internet, not a single Allow.
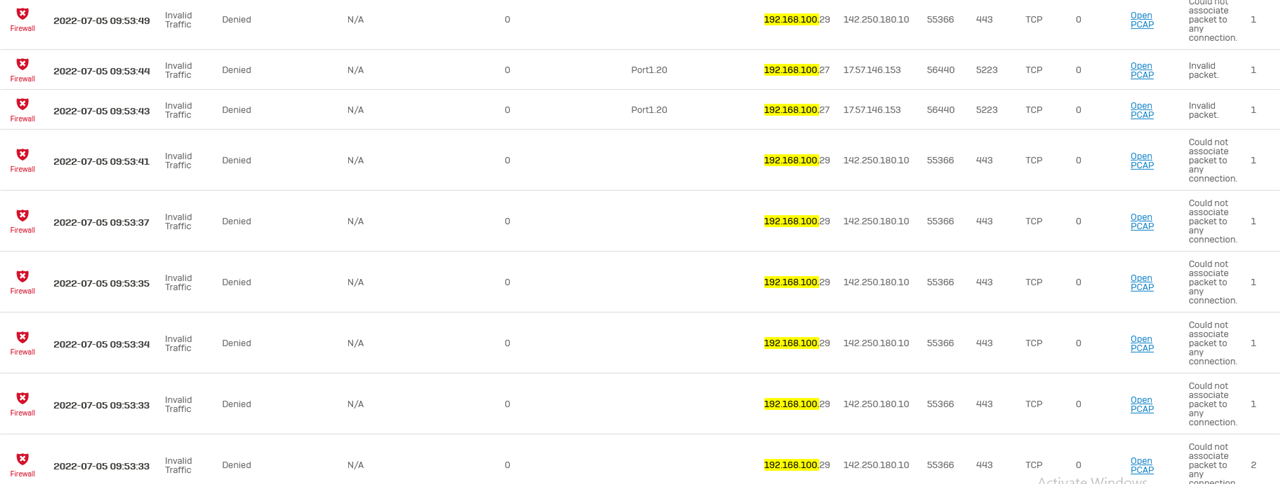
Im really stumped because I dont know why its saying invalid packet or how to progress with this
Throwing a random idea but on UTM you had to create a masq rule for all networks needing the internet, I havent done that nor clicked on create NAT rule during the firewall rule setup. Should I have done or does the XGS handle that?
Many thanks in advance if you can help
Edited TAGs
[edited by: Erick Jan at 4:42 AM (GMT -8) on 15 Nov 2022]



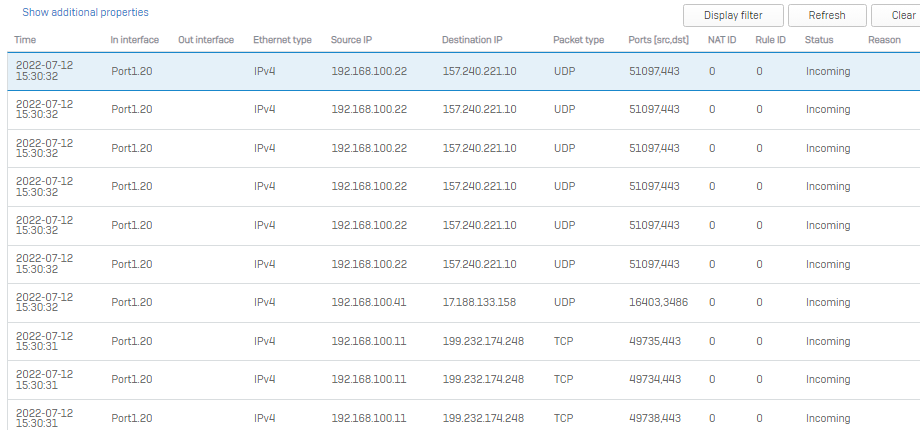
 +
+