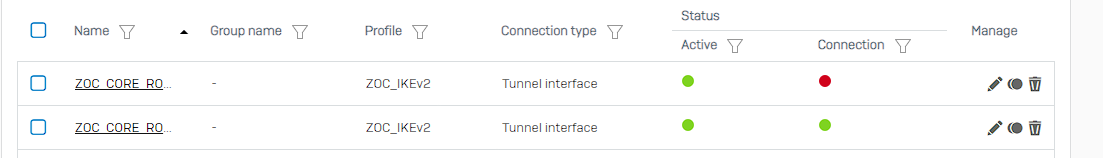
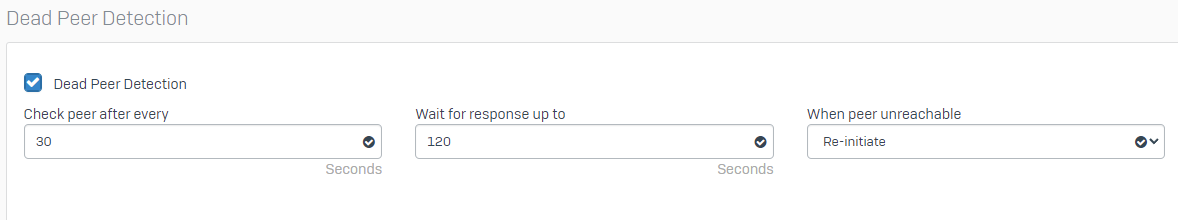
Is there something other than the gateway monitoring that takes a tunnel down?
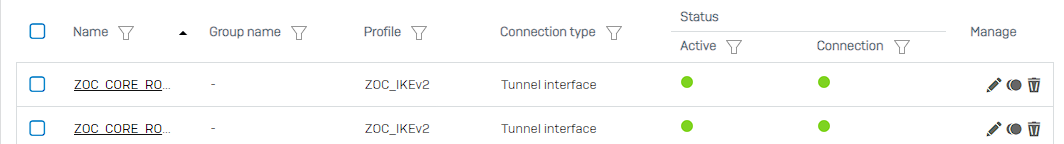
I ask because my device (SFOS 18.5.3 MR-3-Build408) has two tunnels, a primary and a backup, to another XG(SFOS 18.0.5 MR-5-Build586).
Connection type: Tunnel Mode
XFRMs: configured as a /30
Gateway Monitoring: pinging the other end of the tunnel's XFRM(the other /30)
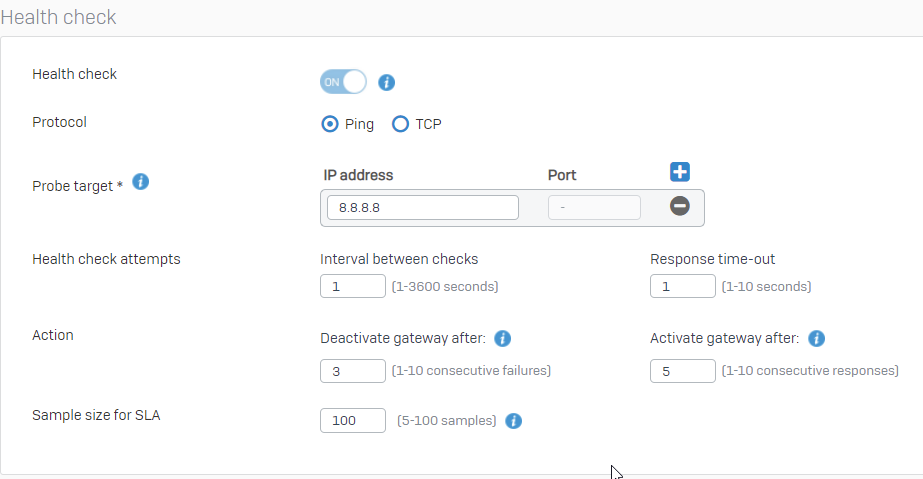
Heres my health check settings:
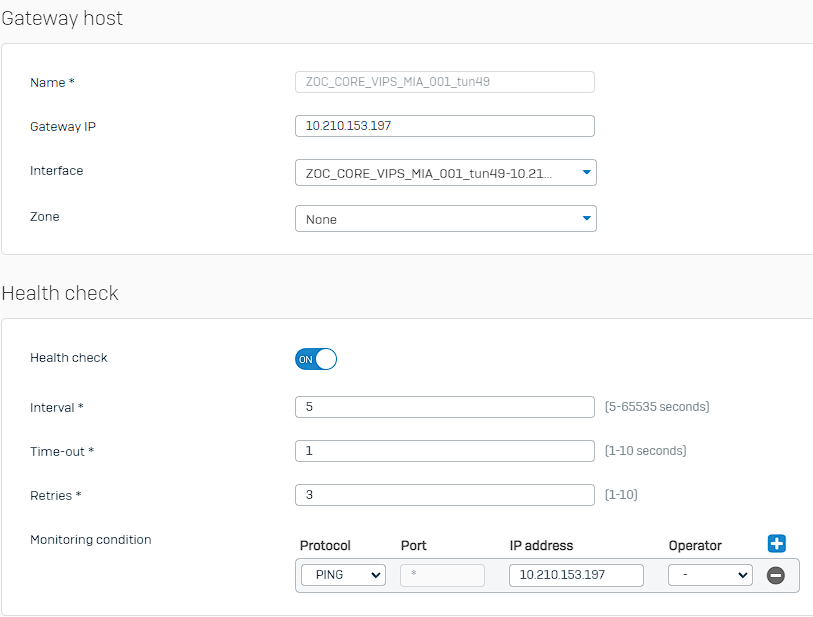
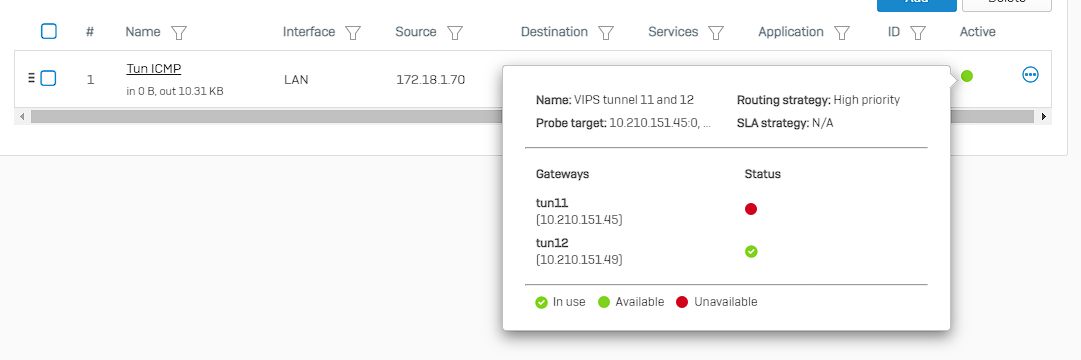
Problem is when I pull my WAN1 cable, the WAN link monitoring takes it down and the Gateway monitoring registers the 10.210.153.197 as unpingable on the other side of the tunnel BUT the IPsec connection keeps that tunnels "Connected" state green for nearly 2 minutes and 40 seconds before it finally takes it down. That's way to long to wait for tunnel traffic to resume.
Does anyone have any ideas for this issue to bring the tunnel down faster?
This thread was automatically locked due to age.