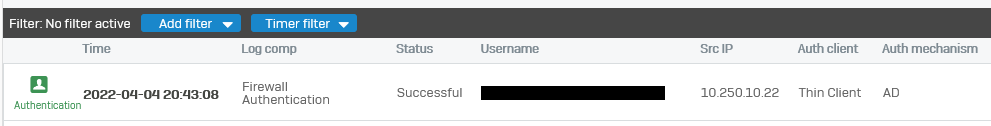
Authentication logs show the user is authenticated correctly
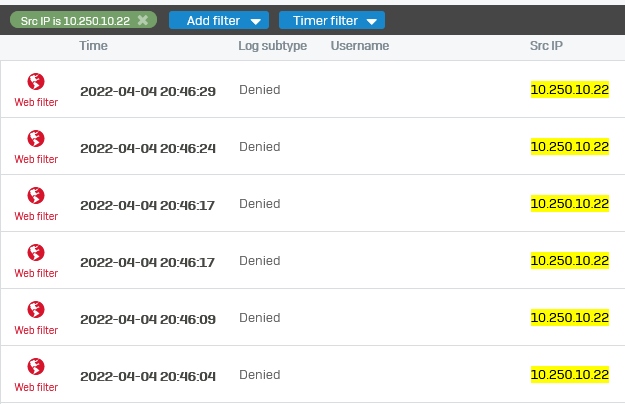
However when browsing, the web filter doesn't pick up the user, so therefore doesn't apply the right policies
Any ideas where to look?
This thread was automatically locked due to age.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Authentication logs show the user is authenticated correctly

However when browsing, the web filter doesn't pick up the user, so therefore doesn't apply the right policies

Any ideas where to look?
No, no server protection client
Did you install SATC, which is End of Life? This tool does not work anymore.
__________________________________________________________________________________________________________________
Did you install SATC, which is End of Life? This tool does not work anymore.
__________________________________________________________________________________________________________________
Ok. That would explain it. Must have missed this. It's still available to download in the Sophos under authentication / client downloads?
What's the replacement to SATC to authenticate users on a terminal server?
Further to that, it's still listed in the Sophos documentation
And there's even a step by step document here: https://support.sophos.com/support/s/article/KB-000036877?language=en_US
The authentication part is working fine. It recognises and authenticates the user. It's just that the web policy doesn't recognise that authentication.
SATC was removed due the issues within SATC. It does not work with Internet Explorer, it does not work with Chrome anymore. It will not work, if you have enhanced AV protection by several AVs installed etc.
https://bugs.chromium.org/p/chromium/issues/detail?id=930750
Therefore SATC was removed and put into EoL state. It got replaced by Server Protection (Intercept X for Server) and a new feature in V19.0 with the legacy proxy.
Using V18.5 and Intercept X will work like before in SATC.
Using V19.0 and new feature multihost is a new technology to implement a terminal server authentication. You need to have v19.0 for this but you do not need intercept x. https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Authentication/HowToArticles/AuthenticationConfigurePerConnectionAuth/index.html#create-firewall-rules-for-multi-user-host-traffic
__________________________________________________________________________________________________________________
So, if a customer has a Sophos XG Firewall and doesn't use Sophos Antivirus, they can't have user based web filtering on a terminal server??
They can use the new feature in V19.0.
__________________________________________________________________________________________________________________
Version 19 isn't in general release though, and for a lot of customers means buying new hardware.
I am not sure, how many customers have a XG85/105 and a terminal server and not Intercept X. That is the only customer affected by this.
__________________________________________________________________________________________________________________
It's not just XG85/105, it's XG115-135, XG210, XG550-750 as well (Rev 1/2). We've got clients that spent $10,000 putting in HA failover hardware devices and now a core function of the firewall they were sold doesn't work and they're being told the only way to get back the functionality you paid for is to spend another $10,000 to replace everything. Bizarre.
Anyway, this particular device I'm looking at is a SFV1C4 - they are on the latest version 18.5.2 MR2-Build380 - how can I fix this issue?
Just XG85/105 are limited to V17.5. All other products will be able to upgrade to V19.0 once its available.
You are not paying this much for a authentication service, instead for one of the best protection layer products on the market (Intercept X). But thats by the way.
V19.0 is a EAP Product, so you can install the EAP or you can wait for the GA release in a couple of weeks.
__________________________________________________________________________________________________________________