Hello from Germany,
I am trying to wrap my brain aroud the following situation:
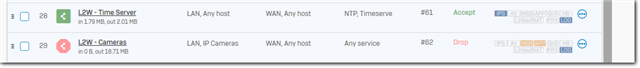
- I have a rule that allows access to an NTP server to anybody (# 61, rule says ACCEPT, see below)
- I have IP Cameras which should not be allowed to reach outside of the LAN (# 62, rule says DROP, see below)
- I have placde the IP-Camera rule below the TIMESERVICES rule
- I expect everything to be dropped now (except NTP of course)., but looking at the log for rule # 62 I see
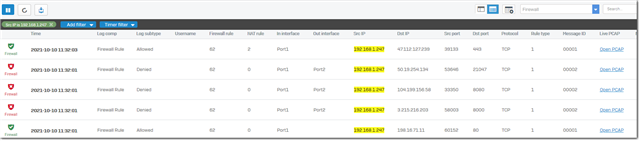
Rule #62 allows traffice on TCP 80 and TCP 443.
Now, the "out interface " shows up empty - of course this is not covered by rule # 62. What is really happening, or better, what is not happening (like traffic going to China)
With beste regards
Volker
IP Host entry for bspc0030:
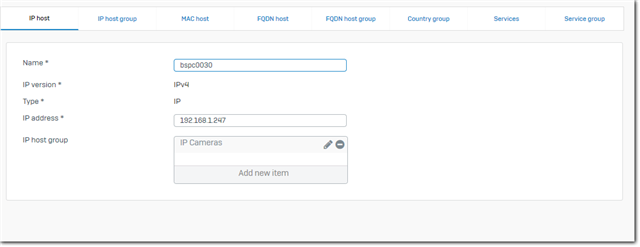
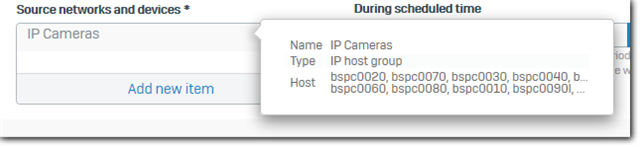
IP Host group used in IP-Camera rule
IP-Camera rule
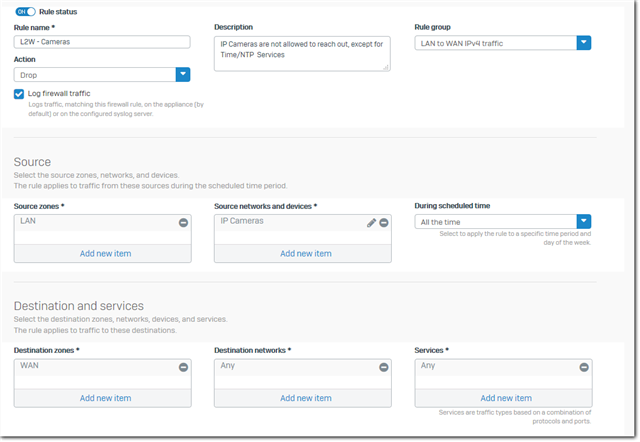
Rules in LAN-TO-WAN group
This thread was automatically locked due to age.
