Hello,
I have the following SSL VPN (site-to-site) connections:

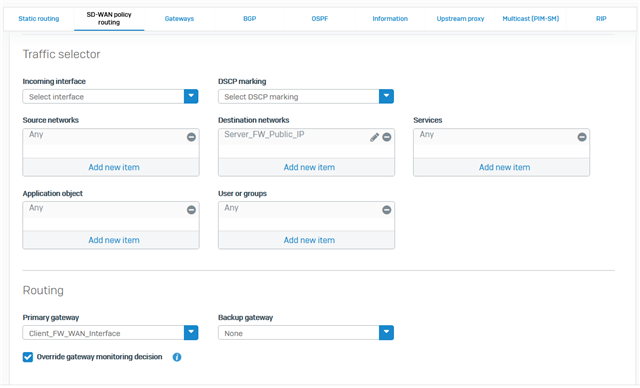
I've 2 WAN interfaces (configured as Active/Active with a 50% balance - which is exactly what I want):

As a client firewall, I'd simply like to force the SSL VPN (site-to-site) connections to go through a specific WAN, and even if this WAN was down it should not go through the other one.
I'd be glad to get your help.
Thanks
This thread was automatically locked due to age.