We have Sophos XG125 firewall with the current firmware SFOS 18.0.5 MR-5-Build586.
Users have been imported from on-prem AD and are currently using L2TP VPN to connect remotely. The goal is to switch them to more secure SSL VPN with OTP (one-time password, aka MFA).
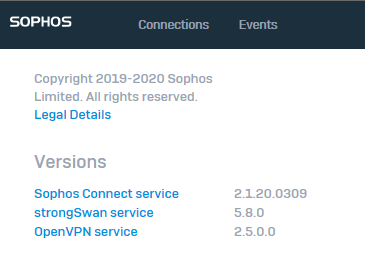
We are using Sophos Connect SSL VPN client current version:
Problem is, I can configure OTP/MFA for a local (non-AD synced) firewall account with Microsoft Authenticator app, and use it to connect via SSL VPN without any issues. But I cannot do the same with AD-synced accounts. I am able to go as far as the OTP setup, and can sign in to the firewall's User Portal WebUI with the OTP code. But I cannot connect with the SSL VPN client... getting authentication failures like this:
messageid="17711" log_type="Event" log_component="SSL VPN Authentication" log_subtype="Authentication" status="Failed" user="NAME REDACTED" user_group="" client_used="N/A" auth_mechanism="Local,AD" reason="wrong credentials" src_ip="IP ADDRESS REDACTED" message="User NAME REDACTED failed to login to SSLVPN through Local,AD authentication mechanism because of wrong credentials" name="" src_mac=""
Any suggestions would be helpful!
This thread was automatically locked due to age.


