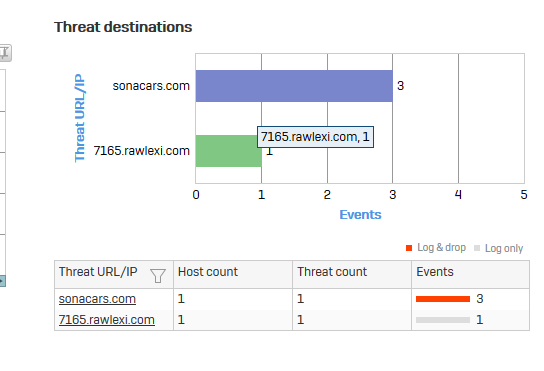
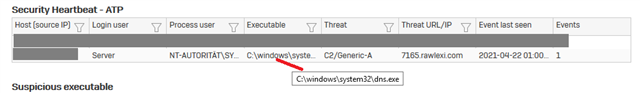
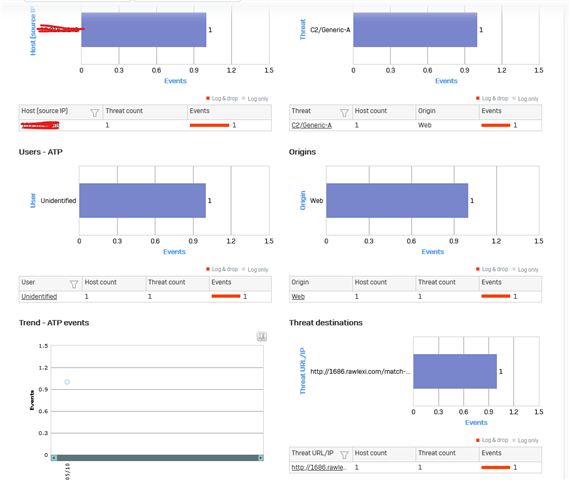
I'm curious about what the best course of action is. One of the XG Firewalls we manage detected an attempt to communicate with a botnet. The policy is set to Log and Drop and the alert itself says "no further action is needed", but why not? I don't think we just want to log and drop this, do we?
Don't we also want to find out what's going on with the device that triggered this?
What are other people doing when they get these alerts?
I can run an additional virus scan with Malwarebytes. I can run a manual scan with Sophos Endpoint protection. I can check to see what programs are installed...
Does anyone have any other recommendations? Ideally I can come up with a procedure to follow whenever we get one of these alerts.
This thread was automatically locked due to age.