Hi SOPHOS Community,
I'm have an issue to setup this IPSec Site-To-Site VPN configuration. Here's a brief description of what is happening. I'm an IT consultant for a business where we have deploy a SOPHOS XG210 Rev 2 firewall on the perimeter of their infrastructure. Here's the IP configuration of the interfaces on the SOPHOS XG210:
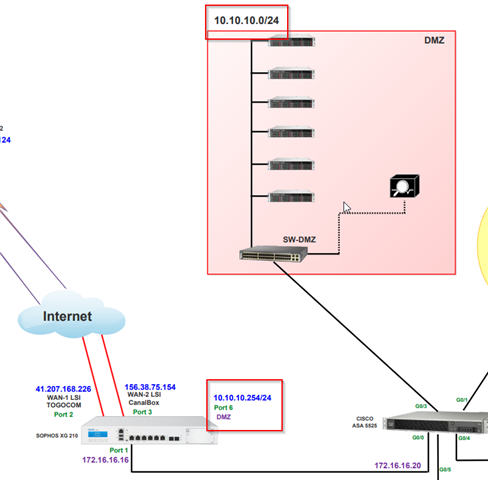
Port1(LAN): 172.16.16.16/24
Port2 (WAN 1): 41.207.168.226
Port3 (WAN 2): 156.38.75.154
The SOPHOS XG 210 FW is directly connected via its LAN (Port 1) to a CISCO ASA FW which has an IP 172.16.16.20 on its WAN ( Gi 0/0) interface.
Behind the CISCO ASA FW exists a DMZ Segment (IP: 10.10.10.0/24). On this DMZ segment, a server which has an IP of 10.10.10.101 have to be reachable through the IPSec VPN Tunnel. How this VPN Tunnel is build?
Indeed, the IPsec VPN Tunnel is build between the SOPHOS XG210 FW and an OCI (Oracle Cloud Infrastructure) . Everything works well for the VPN configuration:
* A machine (192.0.1.3) from the Oracle Cloud Infrastructure (OCI) is able to ping the LAN (Port 1: 172.16.16.16) of the SOPHOS XG210 FW and the WAN ( Gi 0/0: 172.16.16.20) of the ASA FW while passing through the VPN Tunnel. But that machine from the Cloud (192.0.1.3) is not able to ping the machine (10.10.10.101) that resides in the DMZ (10.10.10.0/24) network segment that's behind the CISCO ASA FW and while on the SOPHOS XG i'm able to successfully ping the machine 10.10.10.101 that's behind the CISCO ASA FW.
Any successful advice or solution is welcomed.
This thread was automatically locked due to age.