Hello
I have uncovered a strange issue in routing (or lack of it). First let me describe my environment -
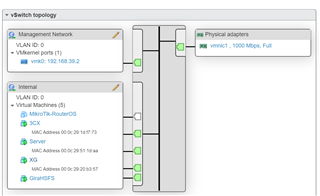
XG, Windows server are hosted on ESXi.
Windows server has one NIC, connected to vswitch0 - port group 0, called Internal.
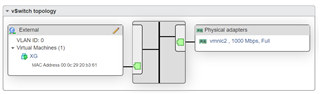
XG has 2 NIC, one connected to Internal, and the other connected to port group 1, called external. XG uses pppoe to get internet. It uses IPsec to connect to two other remote sites (Mikrotik and TMG).
These two NIC are physical NIC (2 port intel ethernet card). One port is connected to internal (so my other laptops etc can connect) and one port is connected to Fiber box(XG dialing into pppoe). All works well as intended.
Now, after establishing IPSEC, I can ping to remote sites if I am pinging from other computers, which are NOT hosted by ESXi. Eg, from my laptop (XG is default gateway), I can ping the remote computers. The remote computers can ping me.
The problem -For whaterever I try, I cannot ping from ANY (I tried installing experimental linuxes also in ESXi) of the ESXi hosted computers (same network - internal) to any of the remote sites. Ofcourse I have checked the usual suspects such as default gateway etc - I am ok in the basics of networking - so usual suspects taken care of). The remote computers CAN ping the esxi hosted computers, so its a one way ping. (makes me think XG is somehow blocking ping from windows host)
XG packet capture, logs DONOT show anything. So how do I troubleshoot. Is this ESXi issue or XG issue? Should I install packet capture in Windows host(I doubt it will help). The packet capture in XG seems to be useless(just like logging).
Also, I tried the promiscous, forged MACs and other things in ESXi. No change.
Tracert from windows (in ESXi)shows that packets are sent to XG, but XG is silently dropping those packets without logging. XG has no problem in routing correctly if the packets originated outside the esxi host. This is ONLY for IPSEC tunnels. I can access XG ui in any case (from ESXi hosted or outside ESXi).
Thank You
This thread was automatically locked due to age.