I'm having a Policy Routing issue on a VM upgraded from v17.5 MR9.
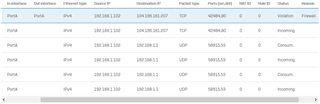
I have 2 gateways. On v17 I had three firewall rules that routed designated clients over the secondary gateway. After upgrading, these rules still work with Migrated Policy Routes. I deleted one of the Migrated Policy Routes to try to create it the "normal" way. I cannot get this new Policy Route to work. When it is enabled, the devices in the designated Host Group can no longer access the Internet. When it is disabled, those devices can access the Internet over the primary/normal gateway. The Migrated Policy Routes (that I didn't touch) use the same secondary gateway and they are working with no issues.
I assume there's some step I'm missing here. Has anyone gotten this working?
To create the new Policy Route, I did the following:
- Change the Route Precedence
- system route_precedence set static sdwan_policyroute vpn
- Delete the Migrated Policy route
- Disable the firewall rule (in v17 it only existed to route these clients over the VPN)
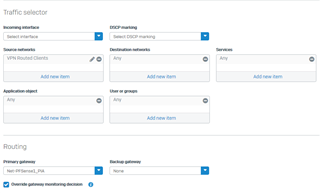
- Create a new Policy Route with the same settings (screenshot below)
This thread was automatically locked due to age.