Hi,
I have just installed this morning coming from pfSense and have connected to the internet but require my LAN & WiFi Ports to see each other.
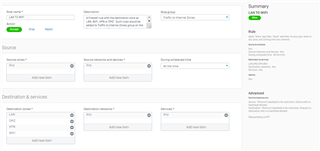
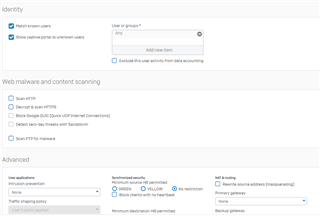
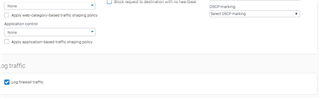
I have configured the zone to zone firewall rule to any from any but it is not working?
Wife & Kids are going mad as we are in lockdown :-(
Massive thanks to any help in advance!
This thread was automatically locked due to age.