Hi,
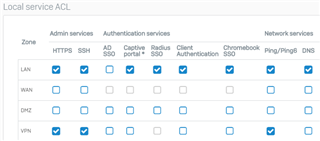
I'm trying out the XG v18 route based VPN. So far I've got it replacing the policy based VPN to Azure and between sites. What I've noticed is that since switching the VPN from policy to route, I'm unable to ping the XG from the other side of the tunnel. I can ping other devices so I know the tunnel is working, I just can't ping the XG's local IP from the remote tunnel. Pinging the XG's WAN IP works, however that would be cause of the local ACL exception. All XG are on SFOS 18.0.0 GA-Build354.
Thank you.
WA
This thread was automatically locked due to age.