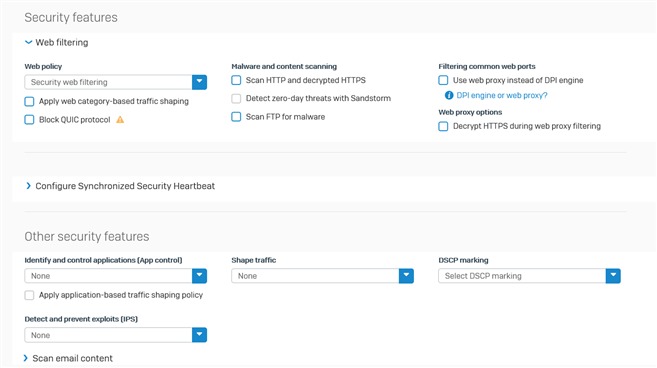
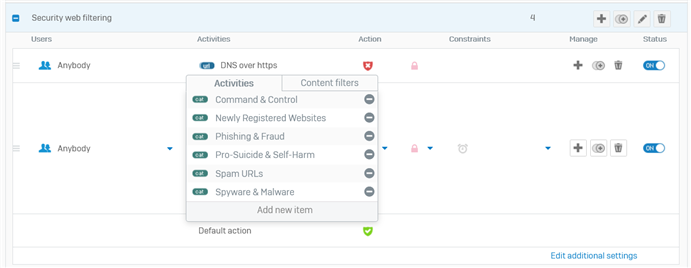
This is the web filter policy that I have applied to some firewall rules where I used the DPI engine
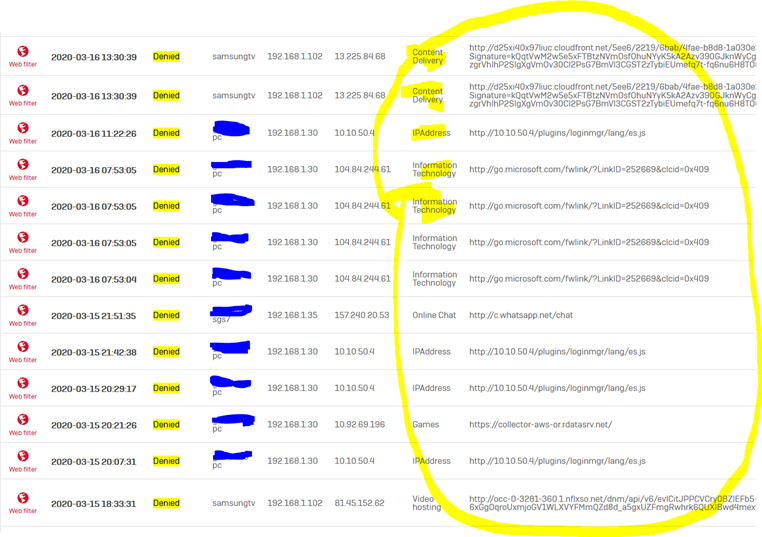
The web filter is blocking other random categories for no reason. This is the log
And example
2020-03-16 13:30:39Web filtermessageid="16002" log_type="Content Filtering" log_component="HTTP" log_subtype="Denied" status="" fw_rule_id="10" user="samsungtv" user_group="Clientless Open Group" web_policy_id="13" web_policy="" category="Content Delivery" category_type="Acceptable" url="d25xi40x97liuc.cloudfront.net/.../70a53108-c477-4e1e-be16-2b5f2cc987fe_320w.bif content_type="" override_token="" response_code="" src_ip="192.168.1.102" dst_ip="13.225.84.68" protocol="TCP" src_port="60076" dst_port="80" bytes_sent="661" bytes_received="0" domain="d25xi40x97liuc.cloudfront.net" exception="" activity_name="" reason="HTTP pipelined request encountered." user_agent="Ignition/1.0 (samsungtv, arm)" status_code="403" transaction_id="" referer="" download_file_name="" download_file_type="" upload_file_name="" upload_file_type="" con_id="1501110912" app_name="" app_is_cloud="0" override_name="" override_authorizer="" used_quota="0"
Why is this happening?
This thread was automatically locked due to age.