Hello,
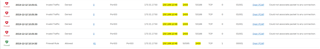
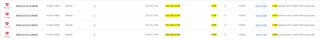
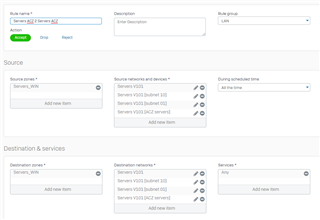
I have a problem with communication between two servers? My firewall is rejecting packets as seen from the picture. Due to this reason both sides cannot exchange MS SQL data. Ping is also functional only from 172.21.17.50, but not reverse. I checked the wireshark on the Windows Server(172.21.17.50) and ICMP replies are sent during ping, but they are not reaching the destination(Linux 192.168.12.46). See second picture.
As you can see there is one allowed communication using rule 41.
I relly don't know what is the cause of this, could you please anyone help?
Note: I have migrated from UTM to XG. It worked on UTM with no problem.
THanks
Lubomir Klas
This thread was automatically locked due to age.