Hi there,
I've got a customer with a dedicated server at OVH, running ESXi.
They wish that a XG protect there virtual servers and managing the traffic.
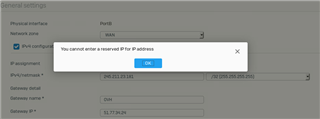
But this simple setup, a XG and myself failed to accomplish this.
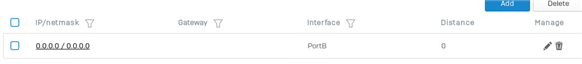
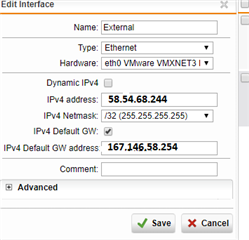
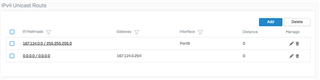
I need to set a host-IP on an interface e.g. 45.85.47.13/32 and use a route to the servers primary IPs gateway e.g. 145.4.7.254/24
This is the official OVH documentation:
docs.ovh.com/.../
EDIT:
Tested with a vUTM and works fine out of the box.....the configuration look like this (and this is everything to configure on the UTM!)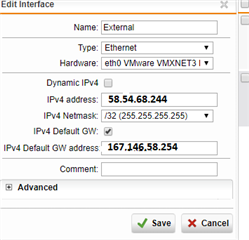
This thread was automatically locked due to age.