Hi. I've encountered a troubling error with Sandboxie this morning after having no issues for quite some time.
I'm running on the latest version of Windows 10, with ESET as my antivirus solution. The Sandbox in question contains only Chrome, version 75.0.3770.100.
I first experienced this issue on Sandboxie version 5.31.1
I have since upgraded and seen the issue on Sandboxie 5.31.2
---------
The Issue:
I have a sandbox configured to contain Chrome, which on termination of Chrome processes, auto-deletes the contents of the sandbox. Last night (and for years prior) this was not an issue.
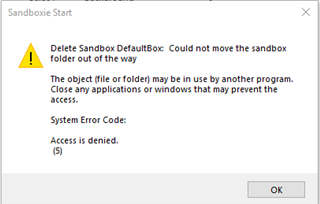
This morning I started up my machine, did some light browsing, and then closed Chrome to go to work. Sandboxie initiated the self-purge of the sandbox, and then gave this error:
The error reads "Delete Sandbox DefaultBox: Could not move the sandbox folder out of the way. The object (file or folder) may be in use by another program. Close any application or windows that may prevent access. System Error Code: Access is denied. (5)"
I attempted to update Sandboxie from 5.31.1 to 5.31.2, but the error persisted.
By rebooting my computer and then invoking a delete sandbox command from Sandboxie, I was able to purge the sandbox - But only if it was the first thing I did. If I opened Chrome again, then the error would repeat. It is not possible to purge the sandbox unless the system is rebooted again.
All Chrome processes are terminated when this error is observed. The Sandbox lists no processes running within it, and Process Explorer doesn't show any Chrome processes running.
By manually going into the sandbox folder, I was able to find the file that is giving the problem:
RegHive seems to be the culprit, though I'm not sure how. Somehow this file is in use and/or access to it is denied to both me, and from Sandboxie.
--------------
Any help on this would be greatly appreciated. I'm not sure why everything would have been fine last night, and now suddenly this is happening - As I installed no new software, and not even any updates were applied. I fear something nefarious may be afoot, but an ESET scan is not revealing anything.
If anyone could provide assistance, I am getting worried and would thank you profusely for helping to determine just what is going on here. Thanks.
EDIT: After a deeper Google Search, it appears this issue has been discussed numerous times on the old forums. Is there any way to access that knowledge? Clicking each Google search result link just brings me right back here, and there's no cached versions to view.