Becoming more familiar with the UTM I am making an effort to check my logs for suspicious activity. I have been keeping an eye on my wireless protection logs and I am noticing something suspicious. an unknown wireless device has been attempting to connect to my wireless network all day long, every day. I have a very long 20+ character alphanumeric random password with special characters, which I highly doubt anyone could crack. I use AES encryption only.
My AP is bridged to LAN using WPA2 personal AES encryption.
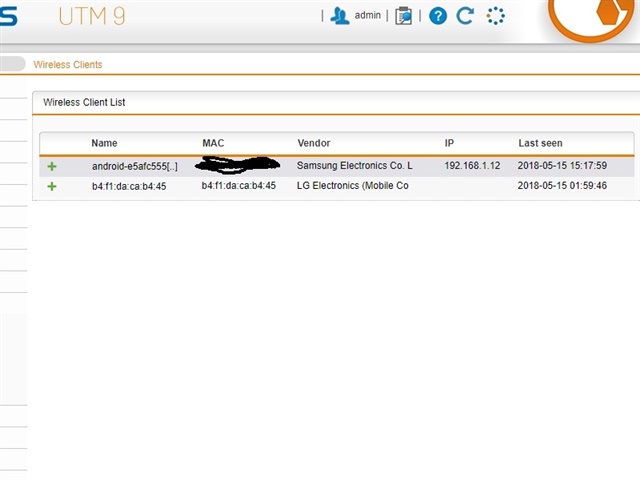
The device would just appear in my logs as STA authentication/association/WPA failure, so I figured maybe someone was trying to guess my wifi password (Good luck!) until just right now I noticed that the device actually showed up in my wireless client list which means they had successfully connected to my network, but how could this happen??? I have scoured my DHCP logs for the matching MAC address and can't find any evidence that they were handed an IP address, and the device does not show up in the IPv4 lease table, so this is bizarre. Before they gained access to my network I had blacklisted the MAC address which locked ME out of the network (I have verified that the MAC address of my Samsung phone is completely different) and so I deleted my access point and created a new one with an even longer password.
The wireless client appears as an "LG electronics"with the name and MAC address being both the same. The MAC address does not belong to my Sophos AP15. At first I thought maybe the access point had separate MAC address for the 2.4 and 5GHz radios but I don't think this is the case.
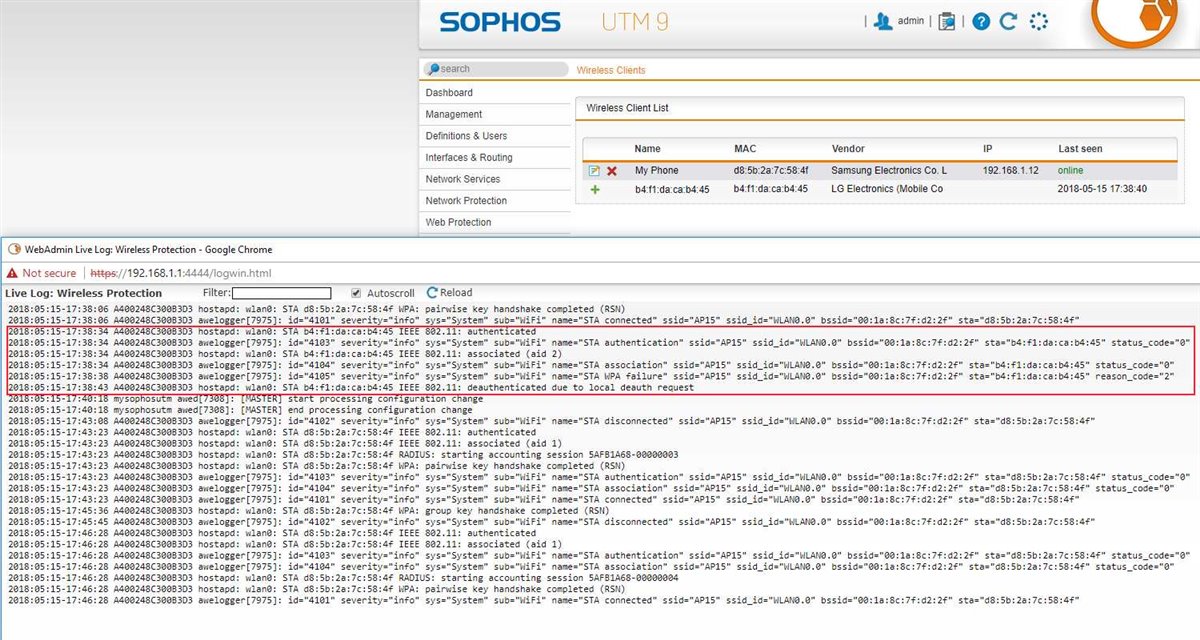
Here is the output of the log. In the screen shot you can see that at 1:59:46 the device must have authenticated.
2018:05:15-01:49:47 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: authenticated 2018:05:15-01:49:47 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: associated (aid 1) 2018:05:15-01:49:47 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-01:49:47 A400248C300B3D3 awelogger[1423]: id="4104" severity="info" sys="System" sub="WiFi" name="STA association" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-01:49:51 A400248C300B3D3 awelogger[1423]: id="4105" severity="info" sys="System" sub="WiFi" name="STA WPA failure" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" reason_code="2" 2018:05:15-01:49:56 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: deauthenticated due to local deauth request 2018:05:15-01:50:17 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: authenticated 2018:05:15-01:50:17 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: associated (aid 1) 2018:05:15-01:50:17 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-01:50:17 A400248C300B3D3 awelogger[1423]: id="4104" severity="info" sys="System" sub="WiFi" name="STA association" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-01:50:21 A400248C300B3D3 awelogger[1423]: id="4105" severity="info" sys="System" sub="WiFi" name="STA WPA failure" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" reason_code="2" 2018:05:15-01:50:26 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: deauthenticated due to local deauth request 2018:05:15-01:54:18 mysophosutm awed[4669]: [MASTER] start processing configuration change 2018:05:15-01:54:18 mysophosutm awed[4669]: [MASTER] end processing configuration change 2018:05:15-01:55:55 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: did not acknowledge authentication response 2018:05:15-01:55:55 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-01:56:26 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: did not acknowledge authentication response 2018:05:15-01:56:26 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-01:59:47 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: authenticated 2018:05:15-01:59:47 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: associated (aid 1) 2018:05:15-01:59:47 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-01:59:47 A400248C300B3D3 awelogger[1423]: id="4104" severity="info" sys="System" sub="WiFi" name="STA association" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-01:59:50 A400248C300B3D3 awelogger[1423]: id="4105" severity="info" sys="System" sub="WiFi" name="STA WPA failure" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" reason_code="2" 2018:05:15-01:59:55 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: deauthenticated due to local deauth request 2018:05:15-02:00:17 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: authenticated 2018:05:15-02:00:17 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: associated (aid 1) 2018:05:15-02:00:17 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-02:00:17 A400248C300B3D3 awelogger[1423]: id="4104" severity="info" sys="System" sub="WiFi" name="STA association" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-02:00:21 A400248C300B3D3 awelogger[1423]: id="4105" severity="info" sys="System" sub="WiFi" name="STA WPA failure" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" reason_code="2" 2018:05:15-02:00:26 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: deauthenticated due to local deauth request 2018:05:15-02:00:48 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: authenticated 2018:05:15-02:00:48 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: associated (aid 1) 2018:05:15-02:00:48 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-02:00:48 A400248C300B3D3 awelogger[1423]: id="4104" severity="info" sys="System" sub="WiFi" name="STA association" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-02:00:52 A400248C300B3D3 awelogger[1423]: id="4105" severity="info" sys="System" sub="WiFi" name="STA WPA failure" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" reason_code="2" 2018:05:15-02:00:57 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: deauthenticated due to local deauth request 2018:05:15-02:54:16 mysophosutm awed[4669]: [MASTER] start processing configuration change 2018:05:15-02:54:16 mysophosutm awed[4669]: [MASTER] end processing configuration change 2018:05:15-03:54:17 mysophosutm awed[4669]: [MASTER] start processing configuration change 2018:05:15-03:54:17 mysophosutm awed[4669]: [MASTER] end processing configuration change 2018:05:15-04:54:32 mysophosutm awed[4669]: [MASTER] start processing configuration change 2018:05:15-04:54:32 mysophosutm awed[4669]: [MASTER] end processing configuration change 2018:05:15-05:54:18 mysophosutm awed[4669]: [MASTER] start processing configuration change 2018:05:15-05:54:18 mysophosutm awed[4669]: [MASTER] end processing configuration change 2018:05:15-06:54:17 mysophosutm awed[4669]: [MASTER] start processing configuration change 2018:05:15-06:54:17 mysophosutm awed[4669]: [MASTER] end processing configuration change 2018:05:15-06:54:33 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: did not acknowledge authentication response 2018:05:15-06:54:33 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-06:59:35 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: disassociated due to inactivity 2018:05:15-06:59:36 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: deauthenticated due to inactivity (timer DEAUTH/REMOVE) 2018:05:15-07:13:58 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: authenticated 2018:05:15-07:13:58 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: associated (aid 1) 2018:05:15-07:13:58 A400248C300B3D3 awelogger[1423]: id="4103" severity="info" sys="System" sub="WiFi" name="STA authentication" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-07:13:58 A400248C300B3D3 awelogger[1423]: id="4104" severity="info" sys="System" sub="WiFi" name="STA association" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" status_code="0" 2018:05:15-07:14:02 A400248C300B3D3 awelogger[1423]: id="4105" severity="info" sys="System" sub="WiFi" name="STA WPA failure" ssid="AP15" ssid_id="WLAN1.0" bssid="00:1a:8c:7f:d2:2f" sta="b4:f1:da:ca:b4:45" reason_code="2" 2018:05:15-07:14:06 A400248C300B3D3 hostapd: wlan0: STA b4:f1:da:ca:b4:45 IEEE 802.11: deauthenticated due to local deauth request
This thread was automatically locked due to age.