I've got a weird one here thats making my head spin.
Ill try to keep this simple using images.
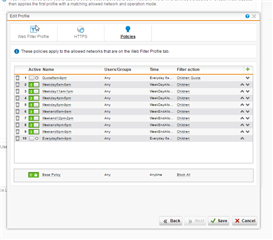
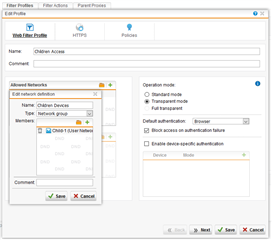
So I have Web Filter Profiles, the below one is for the kids, it has the kids devices defined in "Allowed networks" to filter them in here, as you can see I have a bunch of Policies defined for certain times which allowed them to surf.
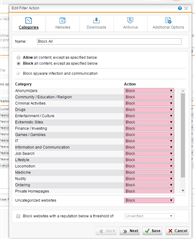
When they fall out of scope of these times, they fall to the Base policy with BLOCK ALL which has everything blocked:
So my aim here is simply to allow them to surf between certain times (time definitions exist as per the Policy names) and when they fall out of these times, they land up in the Block All policy which shuts them down.
This works and has been working all along until now for some reason.
What I'm finding is if Chrome downloads youtube and google into its cache (eg the chrome browser has a tab with https://www.youtube.com loaded and a tab with https://www.google.com loaded) once the times are not allowed and BLOCK ALL takes effect, the tab that has the youtube player active can be used to watch video after video.
I also see that if I load up https://www.google.com I can search for anything I want, but clicking any results get blocked.
Flushing the browser cache and then attempting to establish a connection to https://www.google.com or https://www.youtube.com gets blocked.
Its almost like since the youtube player and google search page has been already downloaded into the webbrowser cache, that the searches and media streams bypass the webproxy until they get flushed and need to be re-downloaded.
I may be going about setting time limits here the hard and silly way, but I have not had any issues where youtube didnt get blocked (stream would stop) once the time limits ran out and it fell to the BLOCK ALL Policy.
Im hoping this makes sense, has anyone had any such experiences or does anyone have any advice?
Thanks much
Sheldon
This thread was automatically locked due to age.