Hello all,
I have been banging my head against this one all day.
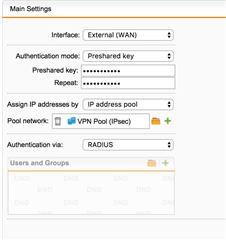
I have L2TP over IPsec setup using the default VPN pool.
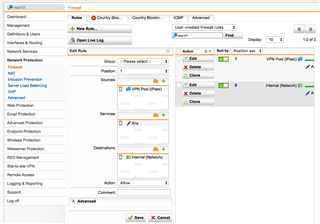
I have a Firewall rule set: (Source) VPN pool --------(Service) Any ---------(Destinations) Internal (Network)
The rule is enabled yet None of my clients can see anything on the internal network.
I have tried setting up NAT Masq. rules with no effect.
What am I missing here?
SG230,
Firmware version: 9.414-2
This thread was automatically locked due to age.