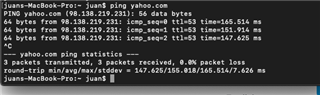
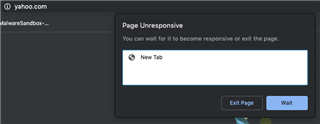
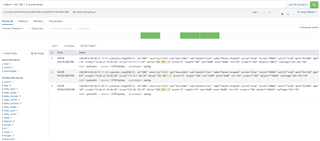
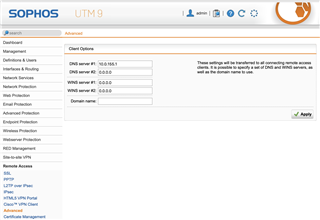
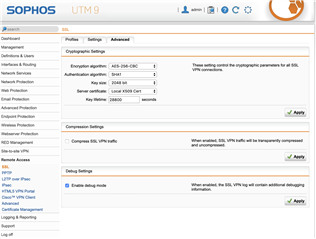
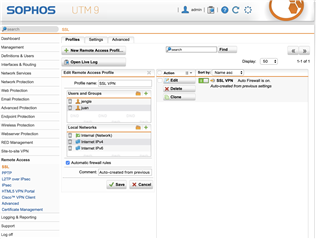
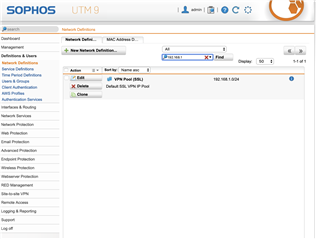
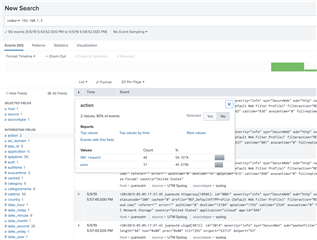
Running Sophos UTM (9.601-5) successfully for a couple years and recently had to rebuild my laptop. After rebuild I pulled openvpn config from user portal and imported to viscosity client. I am able to successfully connect and can ping external sites (8.8.8.8) when connected, can SSH to the UTM device itself, but...I cannot open anything with a web-browser (Chrome/Safari), including the Sophos dashboard. I have looked at my logs and can see successful DNS resolution, nothing obvious in FW logs, have tried toggling IPS and web-proxy into off position without any success...anything obvious I might be missing here?
This thread was automatically locked due to age.