Hello,
I'm having a hard time trying to establish a new VPN tunnel from my UTM 220 (Firmware version: 9.508-10) to an ASA 5525.
We have many IPSec tunnels, which are working on this device... but not the latter.
I get the following ERROR: "S_UT**" #41: sendto on eth2 to 196.****:500 failed in main_outI1. Errno 1: Operation not permitted
I triple checked all IKE parameters, PSK, etc and they're ok.
All the interfaces in question (remote network, remote gateway) are not bound to a specific interface. (left with "any')
On the UTM side we NAT to a public IP.
The thing is that we receive the remote peer's packets (as seen on debugging_log), but the outbound packets get dropped by the firewall.
ulogd[5464]: id="2001" severity="info" sys="SecureNet" sub="packetfilter" name="Packet dropped" action="drop" fwrule="60003" outitf="eth1" srcmac="00:1a::):f0:f3:41" srcip="9.XXXXX" dstip="196.XXXXXX" proto="17" length="288" tos="0x00" prec="0x00" ttl="64" srcport="500" dstport="500"
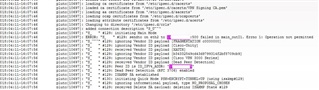
I attached firewall and IP-Sec logs
I don't understand where is the problem... what is blocking the packets.
Thank you!
This thread was automatically locked due to age.