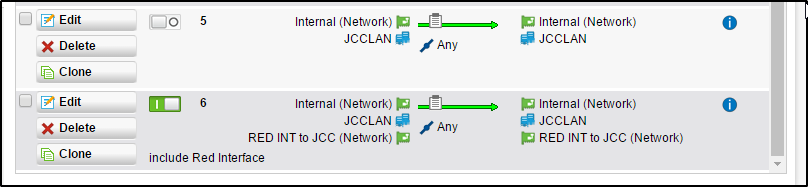
I set up a UTM to UTM red tunnel following https://community.sophos.com/kb/en-us/120157.
This actually was very easy to do and works well except that, although I can access the Sophos WebAdmin page for the devices on the opposite ends of the tunnel, what I can't seem to do is access the web administration of any other system or device across the tunnel.
For example if I try to open the web interface of networked HP printer through the tunnel I eventually get a timeout message from the UTM. This is true for any other http or https site I try to access, such as hitting the Outlook Web Access of an internal mail server, the IWA app for our single sign on solution. From within the same site all these things work as expected.
Any idea why this would happen?
This thread was automatically locked due to age.