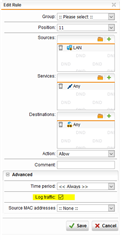
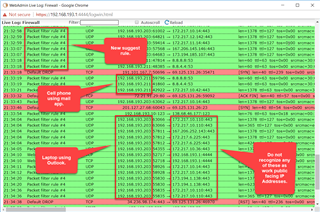
I am so confused. I have been using the Sophos UTM 9 (at home) for years and have been very satisfied with it. However, very recently something has changed and I have no idea what because the reality is that I make very little changes to the firewall. By that I literally mean like adding Static Mappings to DHCP and updating the firmware.
Anyway, as of about a week ago I can no longer receive work e-mails at home. My Microsoft Outlook client, my cell phone mail client, and OWA will NOT connect. Everything times out. No matter what I do.
Keep in mind that my devices have always been in a "Bypass Firewall" group due to that whole debacle and workaround to get Netflix and other services workings, from years ago. The only way for me to receive e-mail while at home is by (1) connecting my laptop to my work VPN and (2) disconnecting my cell phone from my wireless network.
Please advise. Thanks.
This thread was automatically locked due to age.